SSL security for Explorer connections
When required, you can secure connections between CICS Explorer® and CICS® systems by using the Secure Sockets Layer (SSL) protocol. You specify the security and certificate management preferences that apply to secure connections between CICS Explorer and CICS systems, then specify whether to use security when you configure each CICS system connection.
Security and certificate management preferences
By default, certificate management is enabled for CICS Explorer.
- In CICS Explorer IZE0106E Connect failed with error "javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure (SYSA CMCI SECURE)"
- In the job log DFHSO0123 09/19/2012 10:13:22 IYCYZC2K Return code 402 received from function 'gsk_secure_socket_init' of System SSL. Reason: No common ciphers negotiated. Peer: 9.20.210.250, TCPIPSERVICE: XFHWUTCP.
You can use the Security and certificate management pane in the Preferences window to turn trust verification on or off to define keystores for your certificates, and to configure smart card access.
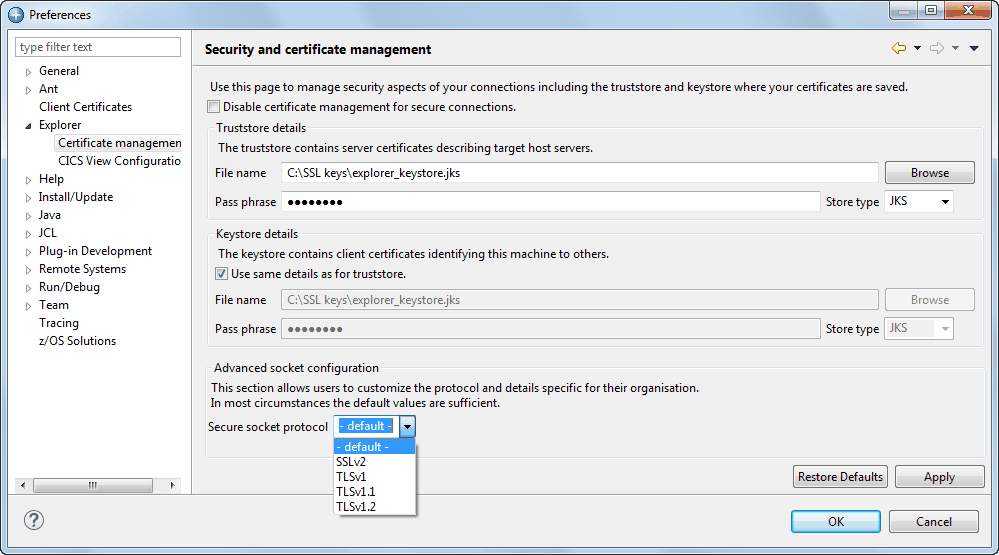
- A keystore is an encrypted file that contains the certificates that are presented to another system to authenticate you.
- A truststore is a type of keystore that contains SSL certificates that are used to verify that a server can be trusted. The truststore can be held in a central location.
- A smart card or CAC (Common Access Card) is a keystore that is held on a physical card. The card is inserted into a reader on your PC and contains certificates that are used to authenticate you to a host server. You must install a compatible driver to access a smart card; either configure a specific PKCS11 driver from disk or on Windows, use the operating system cryptography support.
You can also use some optional parameters that provide explicit control of some of the protocols that are used during connection negotiation. Ask your network administrator for information about the keystores in your organization.
CICS Explorer provides a default keystore in the user's workspace that can serve as both a truststore and keystore. The default pass phrase for the truststore is changeit.
For more information, see  Managing SSL security and certificates in IBM Explorer for z/OS V3.1.1 product documentation.
Managing SSL security and certificates in IBM Explorer for z/OS V3.1.1 product documentation.
CICS system connection configuration
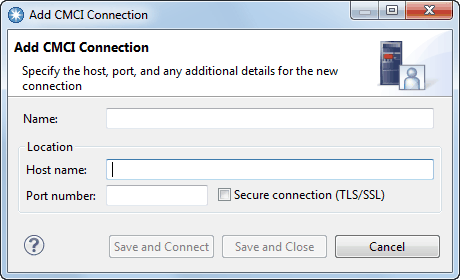
When you configure a CICS system connection, the Add Connection window includes an option to select SSL security for the connection. Certificate authentication can be used only with an SSL-secured connection. The following example shows the Add CMCI Connection window.
- IZE0106E Connect failed with error "Unexpected end of file from server"
When you make a connection, CICS Explorer checks that the SSL settings are the same at each end of the connection. For example, if you do not select Secure connection (TLS/SSL), but the server expects SSL, the connection fails. In this situation, for the first connection attempt, CICS Explorer shows a message that indicates the mismatch and provides the option to attempt the connection again with SSL enabled.
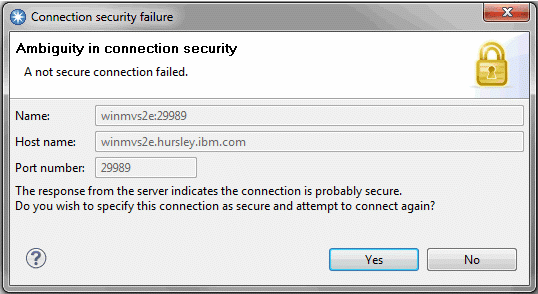
The Ambiguity dialog is shown only for existing or old connections where the SSL setting was not confirmed by a previous version of CICS Explorer such as an Explorer upgrade or an import (not load).
If you connect to a server for the first time, CICS Explorer prompts you to accept the certificate if it does not exist in the keystores.
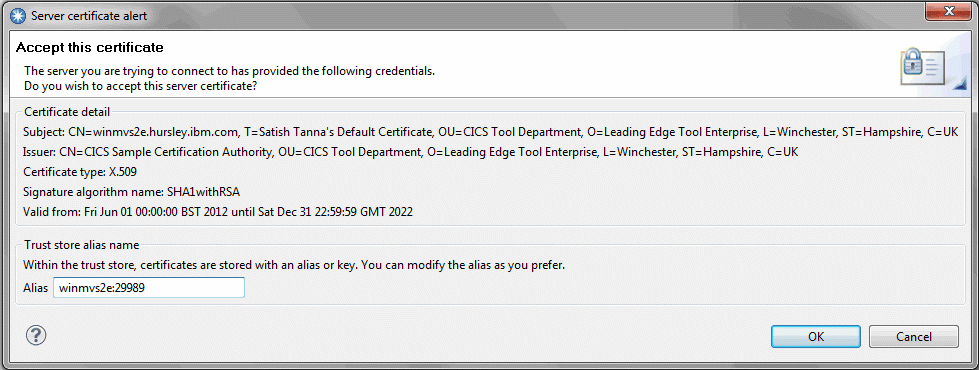
Read the information in the certificate carefully and satisfy yourself that this connection is to the server you expect and that the connection is valid. If you click OK, the certificate is accepted and stored in the keystore. It is then used on every subsequent attempt to connect with this server. You are not prompted again to check the certificate.
You can manage the certificates in your keystore with the iKeyman utility. This utility is supplied as part of the IBM Java Security Socket Extension package.