You can configure the Liberty profile to integrate with
a third-party security service using Trust Association Interceptors
(TAI). The TAI can be called before or after single sign-on (SSO).
Before you begin
Make sure that you have already installed a third-party
security server as a reverse proxy server. The third-party security
server can act as a front-end authentication server when the Liberty
profile server applies its own authorization policy onto the resulting
credentials, which are passed by the proxy server. You must also have
a JAR file that contains the custom TAI class, which implements the
com.ibm.wsspi.security.tai.TrustAssociationInterceptor interface.
Note: There
is no support for monitoring changes of this JAR file.
About this task
A TAI is used to validate HTTP requests between a third-party
security server and a Liberty profile server. The TAI inspects the
HTTP requests from the third-party security server to see if they
contain any security attributes. If the process of validating a request
by the TAI is successful, the Liberty profile server authorizes the
request by checking whether the client user has the required permission
to access the resources.
For more information of custom TAI
and SSO configuration with LTPA, see Developing a custom TAI for the Liberty profile and Customizing SSO configuration using LTPA cookies for the Liberty profile.
 You can also
use the developer tools to configure a TAI service. For more information
about the tools support, see Configuring TAI on the Liberty profile by using developer tools
You can also
use the developer tools to configure a TAI service. For more information
about the tools support, see Configuring TAI on the Liberty profile by using developer tools
Procedure
- Enable the
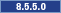 appSecurity-2.0 Liberty
feature in the server.xml file.
appSecurity-2.0 Liberty
feature in the server.xml file. <featureManager>
<feature> appSecurity-2.0</feature>
</featureManager>
appSecurity-2.0</feature>
</featureManager>
- Deploy your applications to the Liberty profile server
and enable all required Liberty features, such asjsp-2.2, jdbc-4.0,
and so on.
- Place the TAI implementation library simpleTAI.jar in
your server directory.
- Update the server.xml file with the
TAI configuration options and location of the TAI implementation library.
In the following
server.xml file, the
custom TAI is enabled, but does not perform authentication for unprotected
URIs and does not allow to fallback to application authentication
method if the TAI authentication fails. As shown in the example, the
following configuration elements are available for TAI support:
- trustAssociation
- interceptors
- properties
<trustAssociation id="myTrustAssociation" invokeForUnprotectedURI="false"
failOverToAppAuthType="false">
<interceptors id="simpleTAI" enabled="true"
className="com.sample.SimpleTAI"
invokeBeforeSSO="true" invokeAfterSSO="false" libraryRef="simpleTAI">
<properties prop1="value1" prop2="value2"/>
</interceptors>
</trustAssociation>
<library id="simpleTAI">
<fileset dir="${server.config.dir}" includes="simpleTAI.jar"/>
</library>
...
Note: The property name
cannot start with a period (.), config.,
or service. Also, the property name id or ID is
not allowed.
For more information about the <trustAssociation>, <interceptors> and <properties> elements,
see also Liberty profile: Configuration elements in the server.xml file.
 You can also
use the developer tools to configure a TAI service. For more information
about the tools support, see Configuring TAI on the Liberty profile by using developer tools
You can also
use the developer tools to configure a TAI service. For more information
about the tools support, see Configuring TAI on the Liberty profile by using developer tools appSecurity-2.0
appSecurity-2.0 Task topic
Task topic