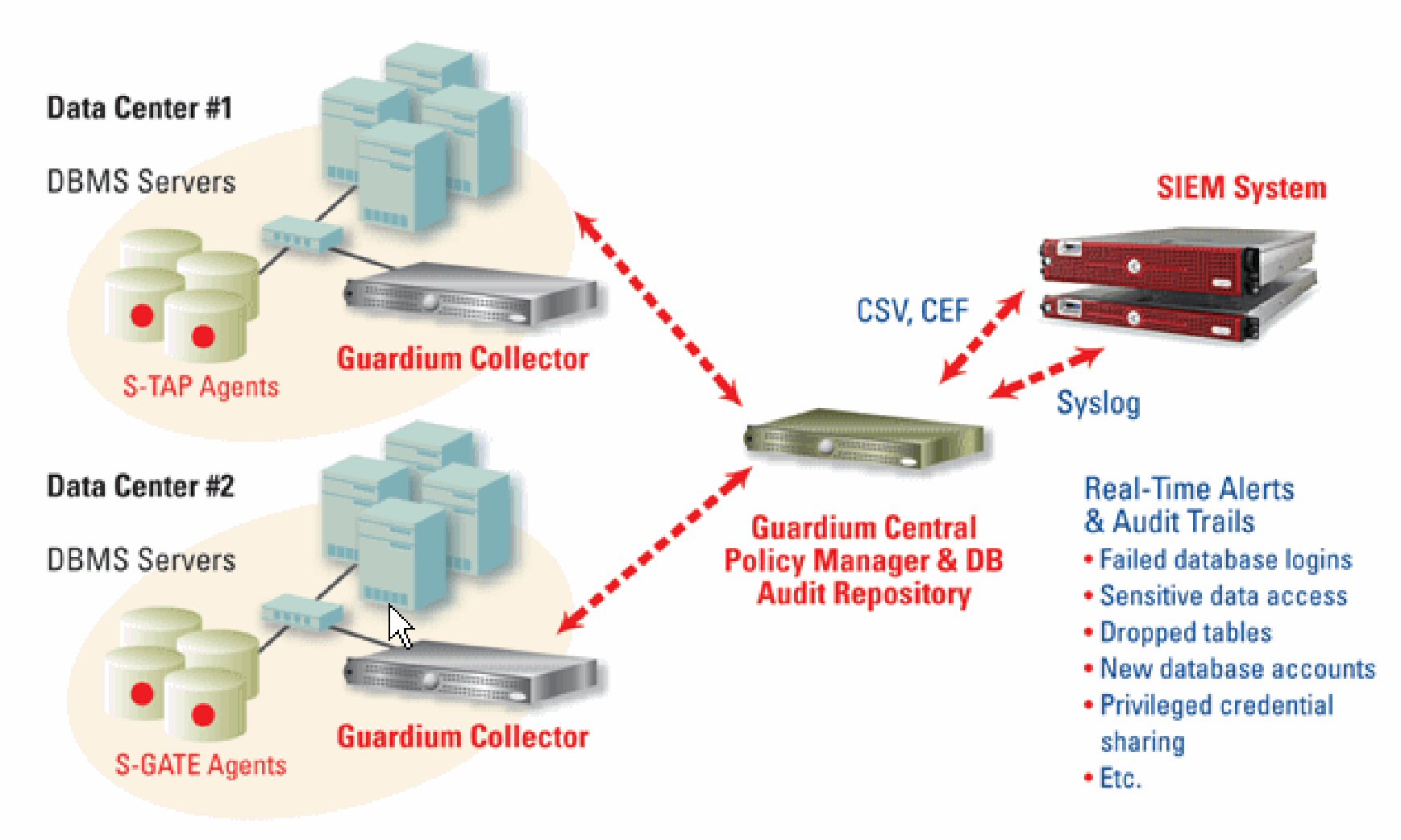
Combining real-time alerts and correlation analysis with SIEM products
Distribute contextual knowledge of database activity patterns, structures, and protocols directly to the third-party database of the SIEM system.
About this task
This Guardium SIEM (Security Incident Event Manager) integration can be done in one of the following ways:
- Syslog forwarding (the most common method for alerts and events)
- Using the CLI command, store remotelog, to specify the Syslog forwarding to facility/priority, and host (destination).
- Using Guardium templates for ArcSight, Envision, and QRadar
- SCP/FTP (CSV or CEF Files sent to an external repository and the SIEM system must upload and parse from this external repository.)
Guardium distributes its contextual knowledge of database activity patterns, structures, and protocols directly to the third-party database of the SIEM system (Guardium has credentials to the SIEM system. It can also write directly to the SIEM database in the SIEM schema. Contact Guardium support as Guardium's entities must be mapped to the third-party schema.
By combining Guardium's real-time security alerts and correlation analysis with SIEM and log management products, companies can enhance their ability to:
- Proactively identify and mitigate risks from external attacks, trusted insiders, and compliance breaches;
- Implement automated controls from Sarbanes-Oxley (SOX), the Payment Card Industry Data Security Standard (PCI-DSS), and data privacy regulations;
- Manage system and network events alongside critical logs and events from the core of their data centers – enterprise databases and applications – for enterprise-wide correlation, forensics, incident prioritization, and reporting.
Security Information and Event Management (SIEM) solutions, also referred to as Security Event Management (SEM) solutions, are offered by companies such as QRadar, ArcSight, CA, Cisco MARS, LogLogic, RSA enVision and SenSage. SIEM products are complementary to Guardium's database activity monitoring solution. They can also use Guardium's filtering and preprocessing of database events to provide 100% visibility and database analytics for SOX, PCI-DSS, and data privacy.
SIEM technology provides real-time analysis of security alerts that are generated by network hardware and applications. It helps companies to respond to network attacks faster and to organize the massive amounts of log data that is generated daily. SIEM solutions are log-based correlation engines.
SIEM solutions are primarily focused on detection and security, but not on auditing. They assemble data from other logs and analyze it at a high level. They correlate much more data such as IP addresses and routers but have little database visibility. They do not have forensics-quality, digitally signed, audit monitoring capabilities so they can be used for immediate information, but not historical proof.
Security information and event management (SIEM) users are faced with the challenge of importing raw logs that are generated by internal DBMS utilities. The performance of DBMS logging utilities, the unfiltered information that they produce, and the lack of necessary granular information create challenges.
Through the Guardium user interface, Guardium can be configured easily to integrate with various SIEM tools.
For SIEM-Guardium Integration, there are predefined templates for QRadar, Envision, and ArcSight so you do not need to define them. You can select the appropriate message template within the rule action.
You can change the default message template, specify the parameters for syslog forwarding, and create the CSV or CEF file to export.
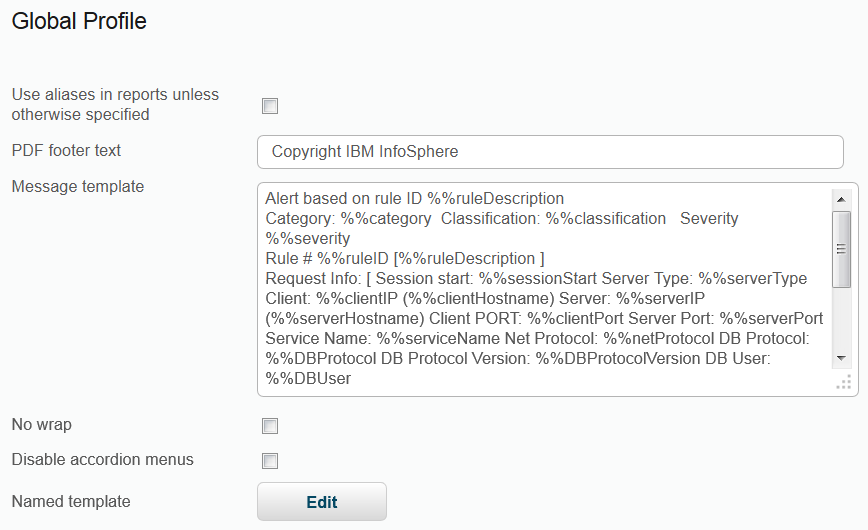
In order for the SIEM product to recognize the information that is being sent, the message template must be changed through the Global Profile. This formatting agreement between the SIEM solution and Guardium allows SIEM products to parse incoming messages and update its own database with the new event/data.
- To open the Global Profile, click .
- Click Edit to Named template.
- Select a template or create a new template with the
 Icon.
Icon.
The Guardium appliance can be configured to send Syslog messages to remote systems. Specific types of Syslog messages can be sent to specific hosts. The Syslog message type is determined from the facility-priority of the message.
The following are examples of facility: all, auth, authpriv, cron, daemon, ftp, kern, local0, local1, local2, local3, local4, local5, local6, local7, lpr, mail, mark, news, security, Syslog, user, uucp. The following are examples of priority: alert, all, crit, debug, emerg, err, info, notice, warning.
Reports containing information that can be used by other applications or reports that contain large amounts of data can be exported to a CSV file format. Report, Entity Audit Trail, and Privacy Set task output can be exported to CSV (Delimiter-separated Value) files. Additionally, CSV file output can be written to Syslog. If the remote Syslog capability is used, the output CSV file is forwarded to the remote Syslog locations.
Each record in the CSV or CEF files represents a row on the report. Contact Guardium Support for a tool that permits the reformatting of CSV files before export.
The Guardium appliance can be configured to send Syslog messages to remote systems, using the store remotelog CLI command. Specific types of Syslog messages can be sent to specific hosts. The Syslog message type is determined from the facility-priority of the message.
Examples of facility are: all, auth, authpriv, cron, daemon, ftp, kern, local0, local1, local2, local3, local4, local5, local6, local7, lpr, mail, mark, news, security, Syslog, user, uucp. Examples of priority are: alert, all, crit, debug, emerg, err, info, notice, warning.
Reports containing information that can be used by other applications, or reports containing large amounts of data, can be exported to a CSV file format. Report, Entity Audit Trail, and Privacy Set task output can be exported to CSV (Delimiter-separated Value) files. Additionally, CSV file output can be written to Syslog. If the remote Syslog capability is used, this action results in the immediate forwarding of the output CSV file to the remote Syslog locations.
Each record in the CSV or CEF files represents a row on the report.
- To open the Audit Process Finder, click .
- Click the
 Icon to add a process or select an existing process from the drop-down list.
Icon to add a process or select an existing process from the drop-down list. - Click New Audit Task under Audit Tasks.
- Enter a description and select Report.
- Select a report from the drop-down list and enter the CSV/CEF File Label.
- Select Export CSV file and Write to Syslog. Choose a named template from the drop-down list.
- Under Task Parameters, choose the Enter Period From >= and Enter Period To <= by using the calendar icon.
- Click Apply.
CSV/CEF files can also be exported on a schedule to the SIEM host. Modify or add an audit task.
- Click to open the Audit Process Finder and modify or add an audit task.
- Choose Export CSV file or Export CEF
file.Note: ACCESS reports can be saved and forwarded in CEF or LEEF format but other reports, such as Guardium Logins, Aggregation Activity Log, and CAS events cannot be mapped to CEF or LEEF.
- Uncheck the Write to Syslog. Otherwise, Syslog messages will be generated instead of a file.
- Open the CSV/CEF Export menu by clicking .
- Select either the SCP or FTP Protocol. Then enter the Host, Directory, Username, Port, and SCP/FTP password.
- In the Scheduling section, define the Start Time, Restart frequency, Repeat frequency, Schedule by Day/Week or Month, Schedule Start Time. Check the box to automatically run dependent jobs.
- Click Save to commit the changes or Reset to clear the fields.
To have a policy alert that is routed to Syslog, exception rules, access rules, and extrusion rules must be modified to trigger notifications to be sent to Syslog. This action can be accomplished by going to the Policy Builder. Policy rules can be sent as email or sent to Syslog and forwarded.
- To open the Policy Builder, click .
- Select the policy and click Edit Rule.
- Click .
- Enter the Description, Category, Classification, and select a Severity level from the drop-down list.
For every policy rule violation logged during the reporting period, the Policy Violations report provides the Timestamp from the Policy Rule Violation entity, Access Rule Description, Client IP, Server IP, DB User Name, Full SQL String from the Policy Rule Violation entity, Severity Description, and a count of violations for that row. With this report, users can group violations and create incidents, set the severity of each violation, and assign incidents to users.