LPAR considerations
Host image profiles for logical partitions must be correctly configured in order to use the TKE workstation to manage keys and perform other operations. The host support element is used to set and change the configuration.
- Usage domain index – The domain associated with the logical partition.
- Control domain index – The set of domains that can be managed from this logical partition. It must include the usage domain index value for this logical partition. A logical partition used as the TKE host includes the usage domain index values for all logical partitions the TKE workstation may manage.
- Cryptographic Candidate List – The set of cryptographic coprocessors that the logical partition may access.
- Cryptographic Online List – The set of cryptographic coprocessors that will be brought online when the logical partition is activated.
You must be running CSFTTCP on at least one LPAR on each machine. It is best to do all module administration for a single machine from a single LPAR. You can do this if you make all domains 'control domains' for the LPAR that is running CSFTTCP. You may want to run CSFTTCP on two LPARs on the same machine if you want TKE to have a second LPAR to use if needed. However, you should build your TKE domains groups such that you do all module administration using as few LPARs on each machine as possible.
If a command is sent to a domain that is not in a logical partition's control domain index, ICSF returns an error (return code 12, reason code 2015).
There is no specific field to identify a logical partition as a TKE host when you are customizing image profiles. You must decide which logical partition will be the TKE host and set up the control domain index and Cryptographic Candidate List appropriately. The control domain index for this partition must include the usage domain index values for all logical partitions that the TKE workstation will control, and the Cryptographic Candidate List for this partition must include all entries in the Cryptographic Candidate Lists for the logical partitions that the TKE workstation will control. The control domain index must also include the usage domain index value for the TKE host partition itself.
Multiple logical partitions can specify the same usage domain index, provided there are no common entries on their Cryptographic Candidate Lists. (Logical partitions may not share the same domain on the same cryptographic coprocessor, but can use the same domain index value on different cryptographic coprocessors.) In order to control these partitions, however, the TKE host partition must have a unique usage domain index, because its Cryptographic Candidate List must include all coprocessors of the logical partitions being controlled.
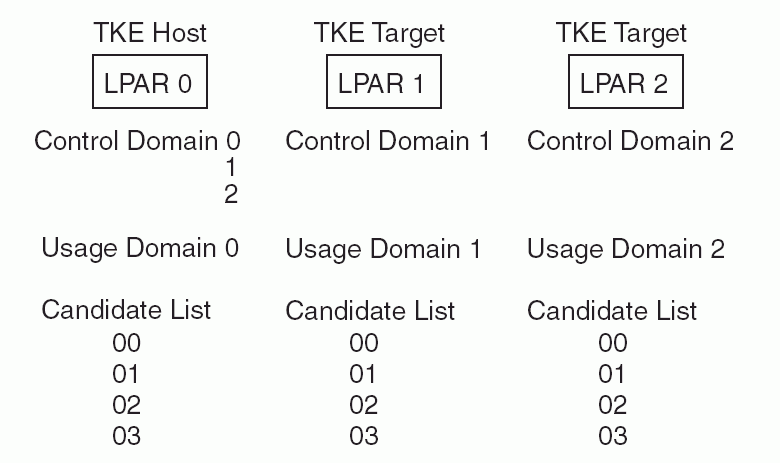
The example in Figure 1 has 3 LPARs and 4 cryptographic coprocessors: 00, 01, 02, 03. There is no domain sharing. In this case, all the cryptographic coprocessors can be specified in the Candidate List for each LPAR.
The example in Figure 2 has 4 LPARs, 2 sharing the same domain and 4 cryptographic coprocessors: 00, 01, 02, 03. In this case, LPAR 1 and LPAR 2 share the same domain, but the Candidate List does not share any of the same cryptographic coprocessors.
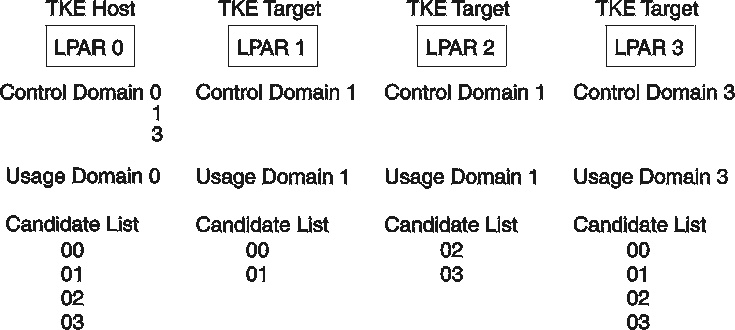
If the same domain is specified by more than one LPAR and the Candidate List has any of the same cryptographic coprocessors, the first LPAR that is activated will IPL without error, but the other LPARs with the same domain will fail activation.