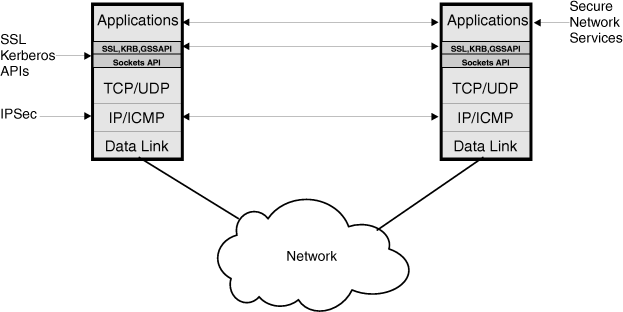
Workload-based security deployment
In making a security protocol selection, an important consideration
is the application workload to be protected. In order to illustrate
this concept, it is helpful to understand where various protocols
are implemented from a protocol layering perspective.
Figure 1. Security
protocols from a protocol layering perspective