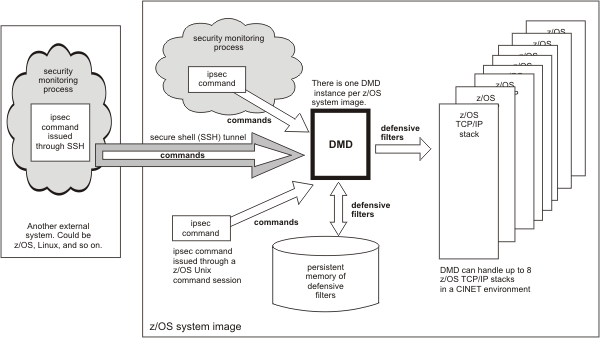
Defensive filtering
An external security information and event manager, through analysis and correlation of messages from multiple sources and systems in the network, can take action to block attacks by installing defensive filters in the TCP/IP stack. A defensive filter is a rule to discard packets, separate from IP security filters. Filter processing matches a defensive filter rule to data traffic, based on any combination of IP source or destination address, protocol, source or destination port, or direction of flow. Filter processing checks defensive filters before IP security filters.
The z/OS® UNIX ipsec command provides the ability to add and manage defensive filters. Defensive filters are typically added automatically as a result of an external security information and event manager's analysis. However, you can also add a defensive filter by manually issuing the ipsec command. The Defense Manager daemon (DMD) is an integral part of managing the defensive filters.
Figure 1 shows an overview of defensive filtering and the DMD.
For more information about defensive filters and the DMD, see Defensive filtering.