Steps for configuring the partner company with NAT model (host-to-host with IPSec)
In the partner company with NAT model, the partner company model topology is modified to include private addressing in the private network of each partner company, with a NAT device in front of each private network.
Before you begin
The following statements and concepts are covered in the discussion of this model:
- AllowNat and NatKeepAliveInterval parameters on the KeyExchangePolicy and KeyExchangeAction statements
- IKE traffic on UDP port 4500, in addition to port 500
- NAT implications for host-to-host dynamic IKE negotiations:
- Local and remote data endpoints
- Local and remote security endpoints
- IKE initiator and responder roles
- Restriction on HowToAuth protocol (AH not supported)
- Using wildcards for location and identity
- RSA signature peer authentication
- Certificates and certificate authorities
- CaLabel
- SupportedCertAuth
Steps for configuring the partner company model (host-to-host with IPSec) assumed a network topology with both partner companies using public IP addresses in their internal networks. Often one or both businesses have an internal network that uses IETF-defined private IP addresses (10.0.0.0/8, 172.16.0.0./12, and 192.168.0.0/16). Private IP addresses cannot be routed outside an internal network. Network address translation (NAT) is used to create a mapping of private addresses to public addresses and perform the necessary translation as packets traverse the NAT device.
When IPSec Security Associations traverse a NAT, there are problems because the NAT is unable to update IP addresses and checksums that are part of the encapsulated data (encrypted, authenticated, or both). The IETF has defined a solution known as NAT traversal (NATT) that allows IPSec Security Associations to successfully traverse a NAT device.
Figure 1 shows the partner company with NAT topology when the partner company model topology has been modified to include private addressing in each partner company's private network with a NAT device in front of each private network.
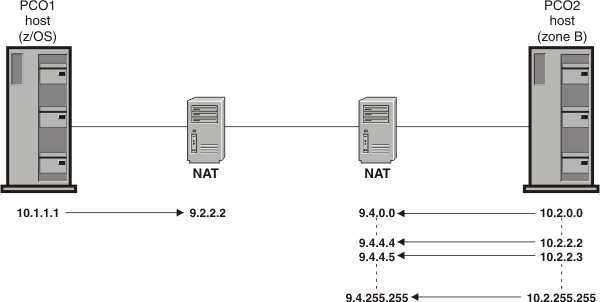
The steps in this topic will describe the configuration considerations and requirements when the NATT solution is implemented to traverse NAT devices in a host-to-host environment. The partner company with NAT model has the same basic security requirements as the partner company model. Configuration statements added or changed for the partner company with NAT model are shown in bold. The example describes the policy for partner company 1 (PCO1).
For this example, assume you must meet the following requirements to allow network communications from a partner company (PCO2) in an untrusted zone B behind a NAT over a connected network (9.4.0.0/16) to a server on this host that is behind a NAT:
- IKE traffic from untrusted zone B that is behind a NAT is allowed to this host that is behind a NAT.
- Secure FTP traffic (using TLS/SSL) from untrusted zone B is allowed to a secure FTP server running on this host.
- Enterprise Extender (EE) traffic from untrusted zone B is allowed to an EE service running on this host using a dynamic IPSec tunnel with strong encryption and authentication.
- FTP traffic from untrusted zone B is allowed to an FTP server running on this host using a dynamic IPSec tunnel with strong authentication.
- The dynamic IPSec tunnel for EE is activated when outbound EE traffic is detected (on-demand activation).
- A dynamic IPSec tunnel for normal FTP control activates for each remote host that initiates an FTP connection (remote activation).
- A dynamic IPSec tunnel for normal FTP data activates for each remote host that initiates an FTP data connection (remote activation).
- Peers authenticate themselves using the RSA signature method.
Procedure
Perform the following steps to meet these requirements and configure the partner company with NAT model.
Results
A completely configured policy, including all objects and their references, is as follows:
# IpFilterPolicy for secure public server
IpFilterPolicy
{
PreDecap off
IpFilterGroupRef ZoneB
}
KeyExchangePolicy
{
AllowNat Yes
NatKeepAliveInterval 0
KeyExchangeRuleRef ZoneB_KeyExRule1
}
###### All re-usable statements follow #######
IpFilterGroup ZoneB
{
IpFilterRuleRef ZoneB-Permitted-traffic
IpFilterRuleRef FTPServer-ZoneB #IPSec-protected
IpFilterRuleRef EE-ZoneB #IPSec-protected
}
######################################
# IpFilterRules #
# defines: #
# data endpoints #
# Allowed services #
# Actions (permit, deny, ipsec) #
######################################
IpFilterRule ZoneB-Permitted-traffic
{
IpSourceAddrRef PrivateServerAddress
IpDestAddrSetRef ZoneB-subnet
IpServiceRef IKE-local-500
IpServiceRef IKE-local-4500
IpServiceGroupRef SecureFTPServer
IpGenericFilterActionRef permit-nolog
}
IpFilterRule EE-ZoneB
{
IpSourceAddrRef PrivateServerAddress
IpDestAddrSetRef ZoneB-subnet
IpServiceRef Enterprise-Extender
IpGenericFilterActionRef ipsec-nolog
IpDynVpnActionRef EE-vpnaction
IpLocalStartActionRef ZoneB-Start-Action
}
IpFilterRule FTPServer-ZoneB
{
IpSourceAddrRef PrivateServerAddress
IpDestAddrSetRef ZoneB-subnet
IpServiceGroupRef FTPServer
IpGenericFilterActionRef ipsec-nolog
IpDynVpnActionRef FTP-vpnaction
}
#######################
# Local Start Actions #
#######################
IpLocalStartAction ZoneB-Start-Action
{
AllowOnDemand yes
LocalPortGranularity packet
RemotePortGranularity packet
ProtocolGranularity packet
LocalIpGranularity packet
RemoteIpGranulatiry packet
LocalSecurityEndpointRef Local_IKED
RemoteSecurityEndpointRef ZoneB_IKED
}
####################
# IpService groups #
####################
IpServiceGroup FTPServer
{
IpServiceRef FTPServer-Control
IpServiceRef FTPServer-Data-Passive
}
IpServiceGroup SecureFTPServer
{
IpServiceRef SecureFTPServer-Control
IpServiceRef SecureFTPServer-Data-Passive
}
##################################
# Services provided by this host #
##################################
IpService IKE-local-500
{
SourcePortRange 500
DestinationPortRange 500
Protocol UDP
Direction bidirectional
Routing local
SecurityClass 0
}
IpService IKE-local-4500
{
SourcePortRange 4500
DestinationPortRange 4500
Protocol UDP
Direction bidirectional
Routing local
SecurityClass 0
}
IpService SecureFTPServer-Control
{
SourcePortRange 990
DestinationPortRange 1024 65535
Protocol tcp
Direction bidirectional InboundConnect
Routing local
SecurityClass 0
}
IpService SecureFTPServer-Data-Passive
{
SourcePortRange 50201 50400
DestinationPortRange 1024 65535
Protocol tcp
Direction bidirectional InboundConnect
Routing local
SecurityClass 0
}
IpService Enterprise-Extender
{
SourcePortRange 12000 12004
DestinationPortRange 12000 12004
Protocol UDP
Direction bidirectional
Routing local
SecurityClass 0
}
IpService FTPServer-Control
{
SourcePortRange 21
DestinationPortRange 1024 65535
Protocol tcp
Direction bidirectional InboundConnect
Routing local
SecurityClass 0
}
IpService FTPServer-Data-Passive
{
SourcePortRange 50000 50200
Protocol tcp
Direction bidirectional InboundConnect
Routing local
SecurityClass 0
}
######################
# Security Endpoints #
######################
LocalSecurityEndpoint Local_IKED
{
Identity Fqdn Server.PCO1.example.com
Location 10.1.1.1
CaLabel CA4PartnerCompany
}RemoteSecurityEndpoint ZoneB_IKED
{
Identity Fqdn *.PCO2.example.com
Location 9.4.0.0/16
}
##########################
# Generic filter actions #
##########################
IpGenericFilterAction permit-nolog
{
IpFilterAction permit
IpFilterLogging no
}
IpGenericFilterAction ipsec-nolog
{
IpFilterAction ipsec
IpFilterLogging no
}
##################################
# Key Exchange offers #
# defines: #
# Authentication type #
# Encryption type #
# Peer authentication method #
# Refresh limits #
##################################
KeyExchangeOffer RSA-SHA1-3DES-DH2
{
HowToEncrypt 3DES
HowToAuthMsgs SHA1
HowToAuthPeers RsaSignature
DHGroup Group2
RefreshLifetimeProposed 480
RefreshLifetimeAccepted 240 1440
RefreshLifesizeProposed none
RefreshLifesizeAccepted none
}
##################################
# Key Exchange Actions #
# defines: #
# Negotiation mode #
# List of Key exchange offers #
##################################
KeyExchangeAction Main-RSA-SHA1-3DES-DH2
{
HowToInitiate main
HowToRespondIKEv1 main
KeyExchangeOfferRef RSA-SHA1-3DES-DH2
}
######################################
# KeyExchangeRules #
# defines: #
# A pair of security endpoints #
# permitted in IKE negotiations #
######################################
KeyExchangeRule ZoneB_KeyExRule1
{
LocalSecurityEndpointRef Local_IKED
RemoteSecurityEndpointRef ZoneB_IKED
KeyExchangeActionRef Main-RSA-SHA1-3DES-DH2
}
############################
# Data Offers #
# defines: #
# Encapsulation mode #
# Authentication type #
# Encryption type #
# Refresh limits #
############################
### Authenticated offer ###
IpDataOffer TRAN-ESPSHA-NOENCR
{
HowToEncap Transport
HowToEncrypt DoNot
HowToAuth ESP HMAC_SHA1
RefreshLifetimeProposed 240
RefreshLifetimeAccepted 120 480
RefreshLifesizeProposed none
RefreshLifesizeAccepted none
}
### Encrypted Authenticated offer ###
IpDataOffer TRAN-ESPSHA-3DES
{
HowToEncap Transport
HowToEncrypt 3DES
HowToAuth ESP HMAC_SHA1
RefreshLifetimeProposed 240
RefreshLifetimeAccepted 120 480
RefreshLifesizeProposed none
RefreshLifesizeAccepted none
}
##############################
# Dynamic VPN Actions #
# defines: #
# Initiation role #
# Pfs group #
# Lifetime of connection #
# List of Data offers #
##############################
IpDynVpnAction FTP-vpnaction
{
Initiation remoteonly
InitiateWithPfs group2
AcceptablePfs group2
VpnLife 1440
IpDataOfferRef TRAN-ESPSHA-NOENCR
}
IpDynVpnAction EE-vpnaction
{
Initiation localonly
InitiateWithPfs group2
AcceptablePfs group2
VpnLife 1440
IpDataOfferRef TRAN-ESPSHA-3DES
}
################
# IP addresses #
################
IpAddr PrivateServerAddress
{
Addr 10.1.1.1
}IpAddrSet ZoneB-subnet
{
Prefix 9.4.0.0/16
}