Application Transparent Transport Layer Security data protection
The Transport Layer Security (TLS) protocol defined in RFC 2246 provides communications privacy over the Internet. The protocol enables client and server applications to communicate in a way that is designed to prevent eavesdropping, tampering, and message forgery. To implement TLS protocols, typically, applications must be modified to incorporate a TLS toolkit. Modifying applications requires significant development overhead, ongoing maintenance for each application, and application-specific knowledge of the parameters needed to implement TLS for that application.
Application Transparent Transport Layer Security (AT-TLS) consolidates TLS implementation in one location, reducing or eliminating application development overhead, maintenance, and parameter specification. AT-TLS is based on z/OS® System SSL, and transparently implements these protocols in the TCP layer of the stack. As shown in Figure 1, most applications do not need any awareness of the security negotiations and encryption done by TCP/IP on its behalf. However, you might want some applications to be aware of AT-TLS or have control over the security functions being performed by TCP/IP. For example, if the application is a server requesting client authentication, you might want the application to get the partner certificate or the user ID associated with the partner certificate, or the application might negotiate in cleartext with its partner to decide whether a secure session is necessary. If both agree to a secure session, the application needs to tell AT-TLS to set up a secure session. The SIOCTTLSCTL ioctl provides the interface for the application to query or control AT-TLS.
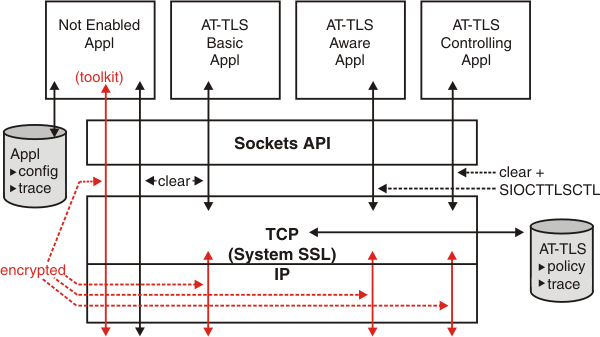
In all cases, an application using a socket enabled with AT-TLS continues to send and receive text data in the clear while encrypted data flows over the network. This allows the use of TLS with applications that cannot be modified or that cannot incorporate one of the available tool kits. The partner application must also support TLS protocols, either by using AT-TLS or an available TLS toolkit.