| SPECIAL |
When you assign it at the system
level, the SPECIAL attribute gives the user full control over all
of the RACF profiles in the RACF database. At the system level,
the SPECIAL attribute allows the user to issue all RACF commands. When you assign the SPECIAL
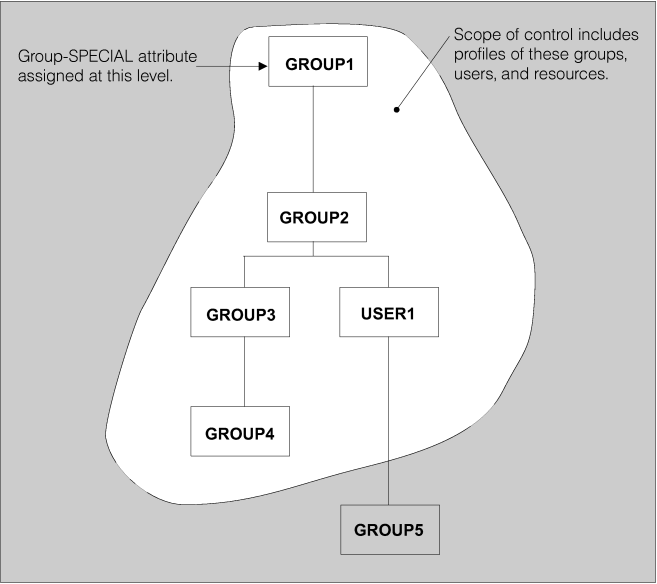
attribute at the group level, the group-SPECIAL user has full control
over all of the resources that are within the scope of the group but
cannot issue RACF commands
that would have a global effect on RACF processing.
|
| AUDITOR |
When you assign it at the system
level, the AUDITOR attribute gives the user full responsibility for
auditing the security controls and use of system resources across
the entire system. With the AUDITOR attribute at the system level,
the user can specify logging options on the RACF commands and list the auditing options
of any profiles using the RACF commands. In addition, the user can control additional logging to
SMF for detecting changes and attempts to change the RACF database and for detecting accesses and
attempts to access RACF-protected resources. When you assign the
AUDITOR attribute at the group level (that is, when you assign the
group-AUDITOR attribute), auditing authority is limited to resources
that are within the scope of the group.
|
| OPERATIONS |
When you assign the OPERATIONS attribute
at the system level, the user can perform any maintenance operations
on RACF-protected resources, such as copying, reorganizing, cataloging,
and scratching data. At the group-OPERATIONS level, authority to
perform these operations is limited to resources that are within the
scope of the group.
|
| CLAUTH |
The CLAUTH (class authority) attribute
allows the user to define profiles in a specific RACF class. A user can have class authority
for the USER class and any of the classes that are defined in the
class descriptor table (CDT). Examples of classes that IBM® supplies in the CDT are the TERMINAL class
(for terminals) and the TAPEVOL class (for tape volumes). For a list
of valid class names, see Supplied RACF resource classes. For a list of the RACF commands
that the CLAUTH attribute allows users to issue, see Table 1.
If the SETROPTS GENERICOWNER
option is in effect, this authority is limited. See Restricting the creation of general resource profiles (GENERICOWNER option).
|
| GRPACC |
When a user with the GRPACC attribute
creates a data set profile for a group data set, RACF gives UPDATE access authority to other
users in the group (if the user defining the profile is a member of
that group). A group data set is a data set whose high-level qualifier,
or the qualifier derived from the RACF naming convention table, is a RACF-defined group name. |
| ADSP |
The ADSP attribute establishes an
environment in which all permanent DASD data sets created by this
user are automatically defined to RACF and protected with a discrete profile. ADSP can be assigned
at the group level, in which case it is effective only when the user
is connected to that group. |
| REVOKE |
The REVOKE attribute prevents the
RACF-defined user from entering the system. REVOKE can be assigned
at the group level, in which case the user cannot enter the system
and connect to that group. |
| RESTRICTED |
The RESTRICTED attribute prevents
a user from gaining access to a protected resource, other than a z/OS UNIX file system
resource, unless the user is specifically authorized on the access
list. Global access checking, the ID(*) entry on
the access list, and the UACC will not be used to allow a restricted
user to access a protected resource. To prevent a restricted user
from gaining access to a z/OS UNIX file system
resource unless specifically authorized, see Controlling access to file system resources for restricted users.
|
Guideline: You and your delegates should assign
the SPECIAL, AUDITOR, and OPERATIONS attributes to the minimum number
of people necessary to administer security at your installation.
|
 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide



 Copyright IBM Corporation 1990, 2014
Copyright IBM Corporation 1990, 2014