 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
General considerations for user ID delegation z/OS Security Server RACF Security Administrator's Guide SA23-2289-00 |
|||||||||||||
|
This topic discusses things to consider for delegating
administrative tasks to other users.
Choose the best option for your installation.
Note: The group-SPECIAL attribute allows password resetting for user
IDs within the group whereas JOIN does not.
Figure 1 shows delegating authority in another way. Figure 1. Delegating authority
(user profiles)
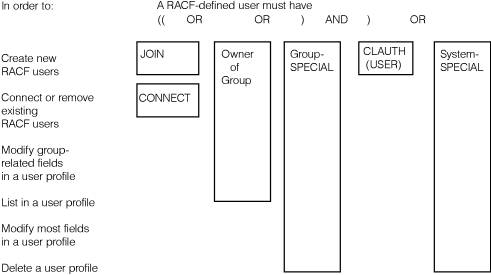 A user with the SPECIAL attribute has full authority over all users and groups. By contrast, a user without the SPECIAL attribute might require a combination of authorities to complete the same tasks with limited scope. For example, to create a new RACF user, the creating user without the SPECIAL attribute must have at least one of the following and have the CLAUTH(USER) attribute:
For detailed information about the authorities required for the
following administrative tasks related to user ID delegation, see
the "Authorization required" topic for the associated RACF command in z/OS Security Server RACF Command Language Reference.
For details about the group-SPECIAL attribute, see User attributes at the group level and The SPECIAL or group-SPECIAL attribute. For details about delegating administrative tasks to help desk personnel, see Authorizing help desk functions. 


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |