 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Authorization checking z/OS Security Server RACF Security Administrator's Guide SA23-2289-00 |
|
|
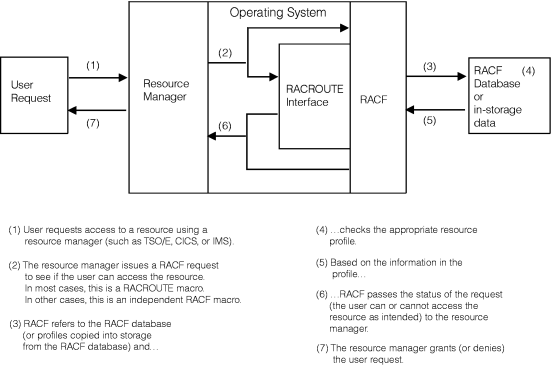
Having identified a valid user, the software access control mechanism must next control interaction between the user and the system resources. It must authorize not only what resources that user can access, but also in what way the user can access them, such as for reading only, or for updating as well as reading. This controlled interaction, or authorization checking, is shown in Figure 1. Before this activity can take place, however, someone with the proper authority at the installation must establish the constraints that govern those interactions. With RACF®, you are responsible for protecting the system resources (data sets, tape and DASD volumes, IMS™ and CICS® transactions, TSO logon information, and terminals) and for issuing the authorities by which those resources are made available to users. RACF records your assignments in profiles stored in the RACF database. RACF then refers to the information in the profiles to decide whether a user should be permitted to access a system resource. Figure 1. RACF authorization checking


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |