 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
 z/OS Security Server RACF Security Administrator's Guide
z/OS Security Server RACF Security Administrator's Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Pictorial view of RACF authorization checking z/OS Security Server RACF Security Administrator's Guide SA23-2289-00 |
|
|
For a complete description of the numbered steps described in the following figures, see Authorizing access to RACF-protected resources. Figure 1. Process flow
of callers of RACF for RACROUTE
REQUEST=AUTH requests
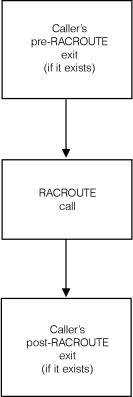 Note: For information about exits that affect RACROUTE calls, see
the documentation for the calling product.
Figure 2. Process flow of
SAF router for RACROUTE REQUEST=AUTH requests
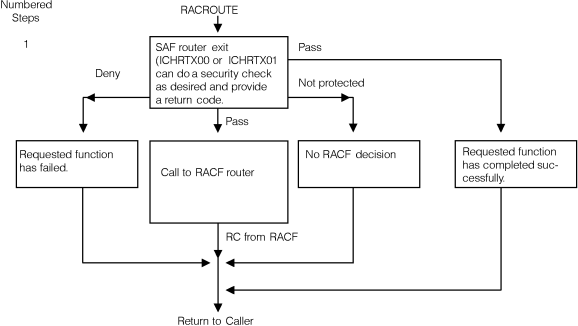 Figure 3. Process flow
of RACF router
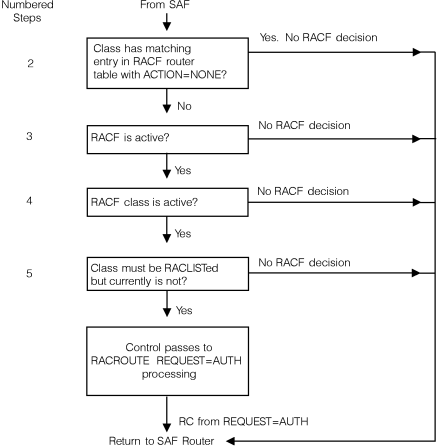 Figure 4. Process
flow of RACF authorization
checking, part 1 of 3
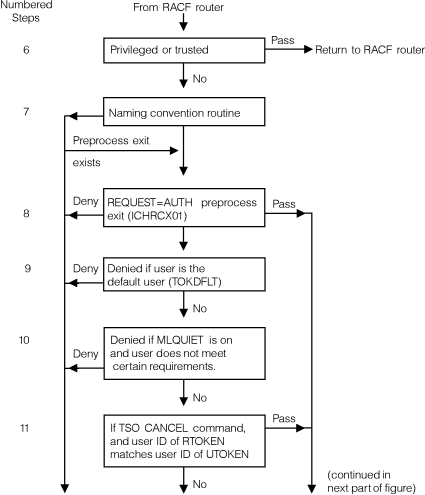 Figure 5. Process flow of RACF authorization checking, part
2 of 3
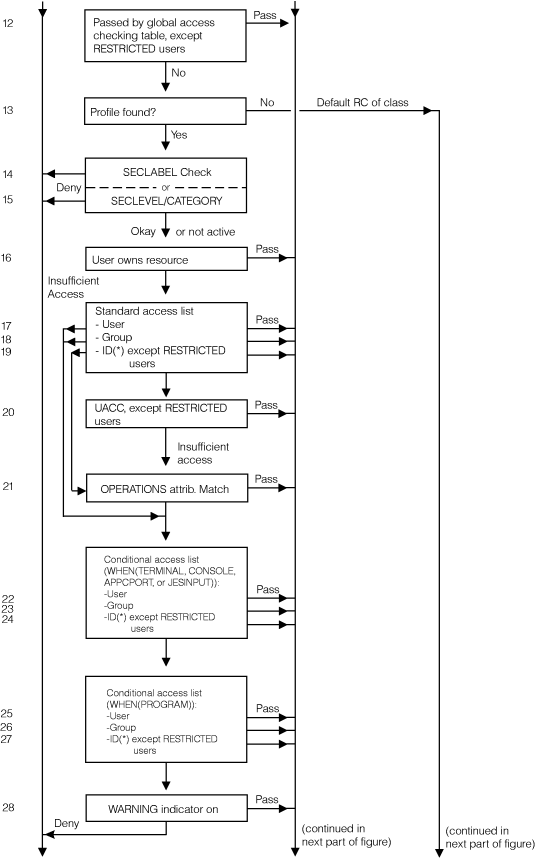 Figure 6. Process flow of RACF authorization checking, part
3 of 3
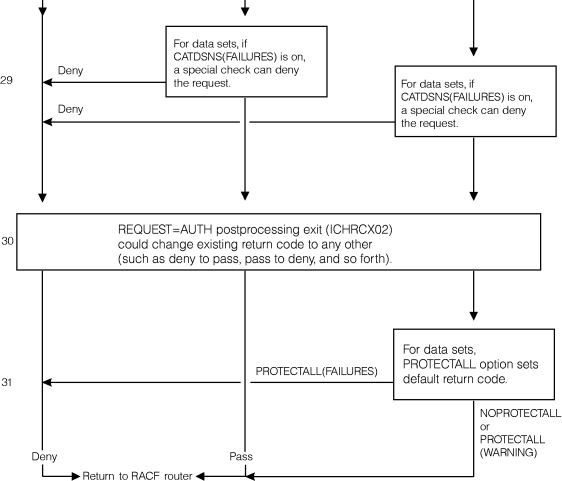 


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |