CICSPlex SM security checking sequence
A user can issue a single CICSPlex® SM command that causes data to be gathered about or an action to be performed against one or more CICS® systems comprising a CICSplex. These CICS systems can reside in different MVS™ images.
When a user issues a request, the request is directed
to the CMAS that manages the target CICS system
or systems. Figure 1 and Figure 2 are flowcharts showing the procedure
followed by CICSPlex SM to
evaluate the security requirements of a request from a user. Here
is a description of that procedure:
- CICSPlex SM determines
whether CICSPlex SM rules
allow the request to be processed.
- If not, CICSPlex SM terminates the request and issues an error message.
- CICSPlex SM determines
whether simulated CICS security checking is to be
performed.
- If not, processing continues at 9.
- CICSPlex SM determines
whether the user is exempt from simulated CICS security checking.
- If so, processing continues at 9.
- CICSPlex SM determines
whether simulated CICS command checking is to be performed.
- If not, processing continues at 6.
- CICSPlex SM determines
whether the user is allowed to process the command.
- If not, CICSPlex SM terminates the request and issues an error message.
- CICSPlex SM determines
whether the request is an action (not a request for information).
- If not, processing continues at 9.
- CICSPlex SM determines
whether simulated CICS resource checking is to be performed.
- If not, processing continues at 9.
- CICSPlex SM determines
whether the user is allowed access to information about the resource.
- If not, CICSPlex SM terminates the request and issues an error message.
- CICSPlex SM performs the action or gets the information.
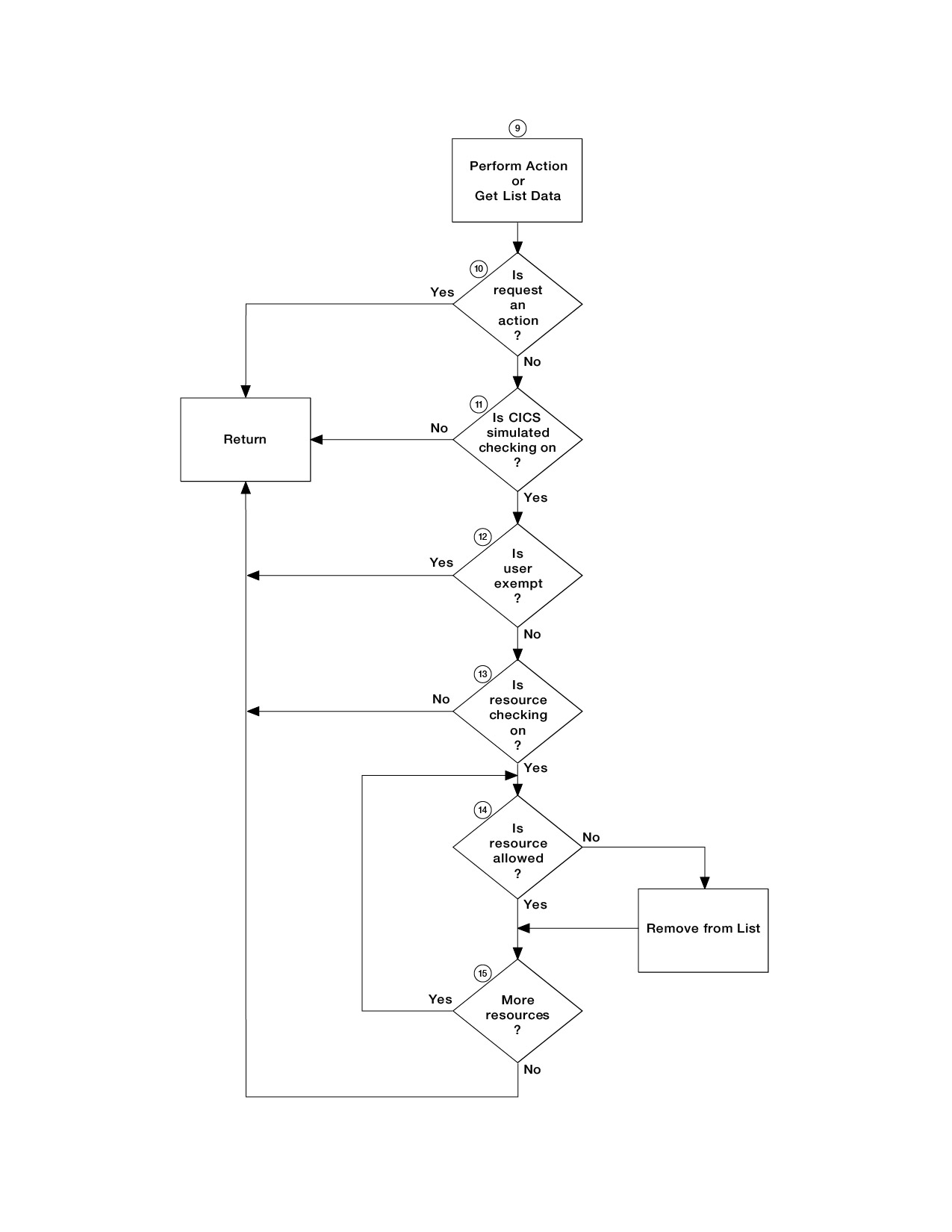
- CICSPlex SM determines
whether the request is an action (not a request for information).
- If so, CICSPlex SM returns the results of the action.
- CICSPlex SM determines
whether simulated CICS security checking is to be performed.
- If not, CICSPlex SM returns the requested information in the appropriate view.
- CICSPlex SM determines
whether the user is exempt from simulated CICS security checking.
- If so, CICSPlex SM returns the requested information in the appropriate view.
- CICSPlex SM determines
whether simulated CICS resource checking is to be performed.
- If not, CICSPlex SM returns the requested information in the appropriate view.
- CICSPlex SM determines
whether the user is allowed access to information about the resource.
- If not, CICSPlex SM excludes the requested information from the appropriate view.
- CICSPlex SM determines
whether information for another resource is requested.
- If so, processing continues at 14.
- Otherwise, CICSPlex SM returns the requested information in the appropriate view.
No further security checking is required. Figure 1. Flowchart of CICSPlex SM security
checking sequence - part 1
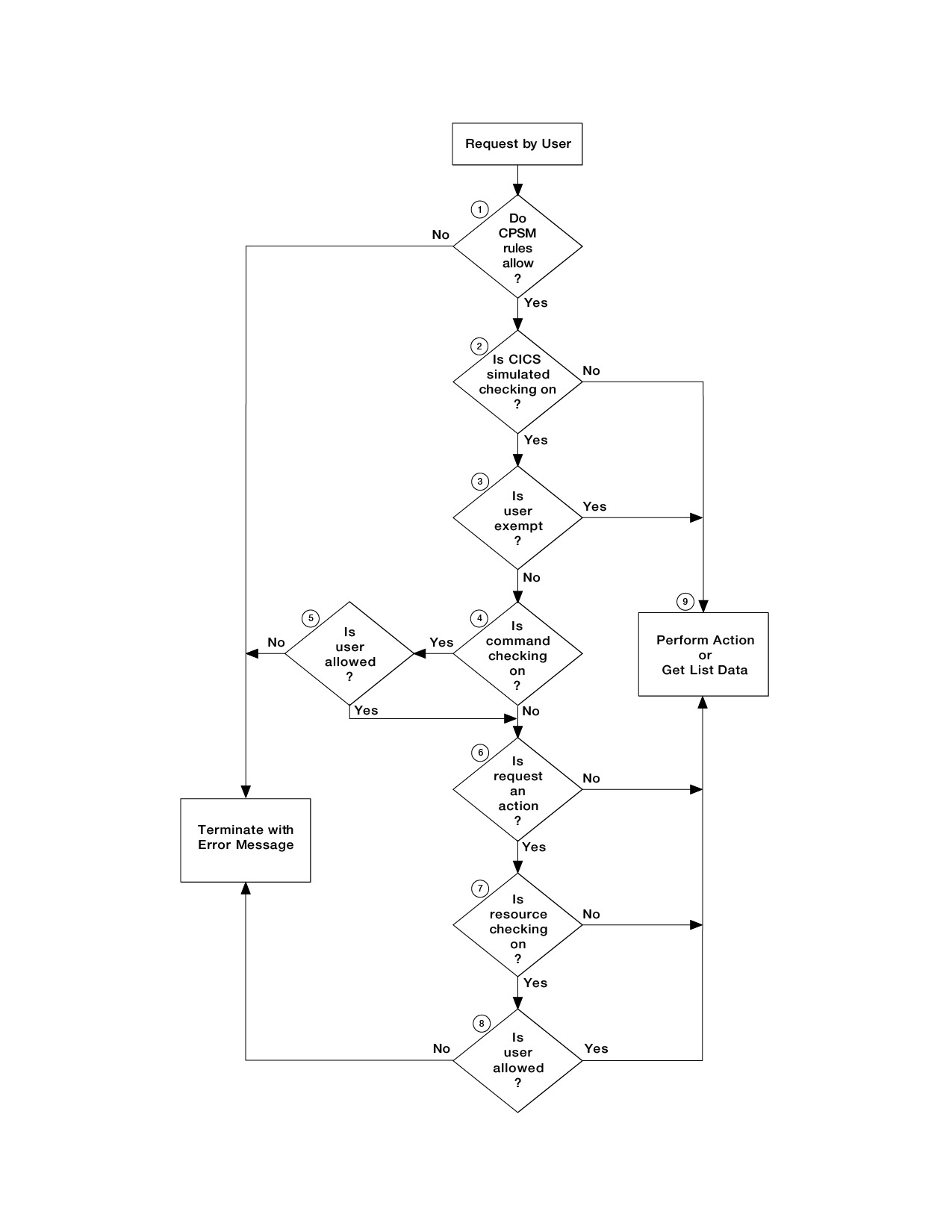
Figure 2. Flowchart
of CICSPlex SM security
checking sequence - part 2