CICS parameters controlling transaction-attach security
You control CICS® transaction-attach security checking through CICS system initialization parameters.
- SEC
- Specify SEC=YES if you want to use RACF® services to control access to any CICS resources—in particular, CICS transactions. (For more information, see Security-related system initialization parameters.)
- SECPRFX
- Specify SECPRFX=YES if your transaction profiles are defined to RACF with
a prefix that corresponds to the userid of the CICS region.
Specify SECPRFX=prefix if your transaction profiles are defined to RACF with any other prefix.
(For more information, see Security-related system initialization parameters.) - XTRAN
- Specify XTRAN=YES or XTRAN=resource_class_name if you want CICS to control who can
initiate transactions. If you specify YES, CICS uses profiles defined in the RACF default resource
classes TCICSTRN and GCICSTRN. (See RACF classes for CICS resources for details of these resource classes.)
If you specify a resource class name, CICS uses the name you specified, prefixed with T for the resource class, and G for the grouping class.
If you specify XTRAN=NO, CICS does not perform any authorization check on users initiating transactions.
Note that the default is YES. Therefore if you specify SEC=YES and omit the XTRAN parameter, transaction-attach security is in effect, using the default resource class names.
There are no CICS parameters that allow you to control transaction-attach security at the individual transaction level. When you specify SEC=YES and XTRAN=YES (or XTRAN=resource_class_name), CICS issues an authorization request for every transaction. It does this whether the transaction is started from a terminal, by using an EXEC CICS START command, or triggered from the transient data queue, either with or without the termid operand. CICS performs this security check even if no user has signed on. Users who do not sign on can use only those transactions that are authorized to the default user.
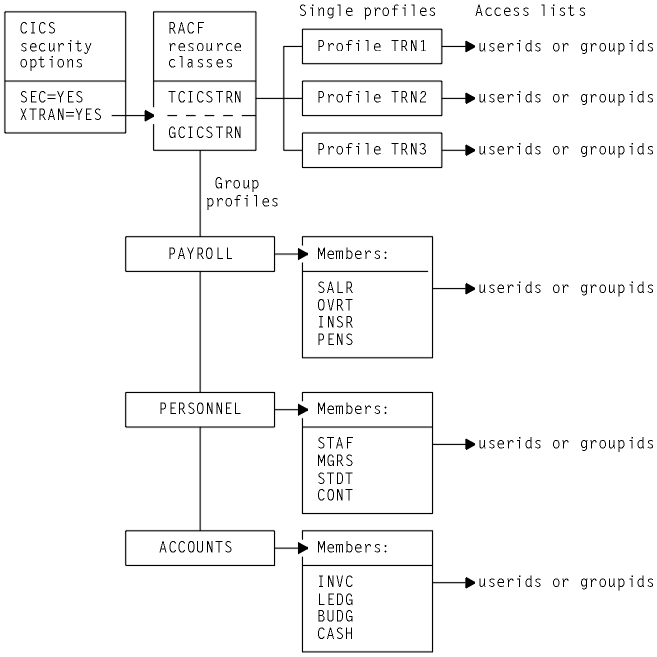
- The following system initialization parameters are specified:
BecauseSEC=YES XTRAN=YESXTRAN=YESis specified, the resource class name is TCICSTRN and the grouping class name is GCICSTRN. - The resource class TCICSTRN contains profiles TRN1, TRN2, and TRN3.
- The grouping class GCICSTRN contains the following group profiles:
- PAYROLL (members SALR, OVRT, INSR, and PENS)
- PERSONNEL (members STAF, MGRS, STDT, and CONT)
- ACCOUNTS (members INVC, LEDG, BUDG, and CASH)