Field level security
You can use field level
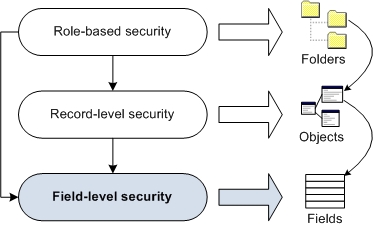
security to control access to individual fields within an object. Field level security is applied to
the set of objects that the user is entitled to by either role-based security or record level
security rules. If no field level security is defined for an object, security is applied at the
object level (if security rules are defined) or at the folder level.
When you define a field level security rule, you must consider all the scenarios that are required to access the field. If any scenarios are not defined, a user's access to the field is denied. This is known as redaction.
For example, one rule might specify that if a user is not an Owner, they have Read access only to a field. If a user is an Owner, they have Read and Update access. When the outcome of the formula is true, then Read access or Read and Update access is granted to a user. When the outcome of the formula is false, the field is redacted.
The way that access is restricted depends upon whether the outcome
of a formula is true or false when it is applied to a field.
- True: The field is available to users as Read Only or Read and Update.
- False: The field is redacted. Users can see the field label, but not its value. Instead, the
value is redacted, and the user sees some text, such as
Confidential
in place of the field value.
Restrictions:
- System fields are not supported.
The system fields are
Name
,Description
,Location
,Creation Date
,Created By
,Last Modification Date
,Last Modified By
, andComment
. - Computed fields are not supported.
- If more than one rule applies to a field, each is rule is combined by using an OR condition.
- If more than one rule is defined for the same field, and one grants Read access to the field and another grants Read and Update access, then a user is granted Read and Update access if the outcome of the formula for each rule is true.