Configuring Mobile Enterprise Gateway (MEG) in Standalone mode
Follow these steps to configure your gateway in Standalone mode.
About this task
To set up your gateways in a High Availability (HA) cluster, go to Mobile Enterprise Gateway (MEG) in High Availability (HA) mode. You cannot switch the gateway mode from Standalone to High Availability (HA) mode for a gateway that is already configured.
Procedure
- From the Enterprise Gateway section of the Cloud Extender® Configuration Tool, choose the Standalone configuration mode.
- Choose to run the gateway as a Relay or
Direct.
- To run the gateway in relay access mode, configure these settings:
- Select Relay:
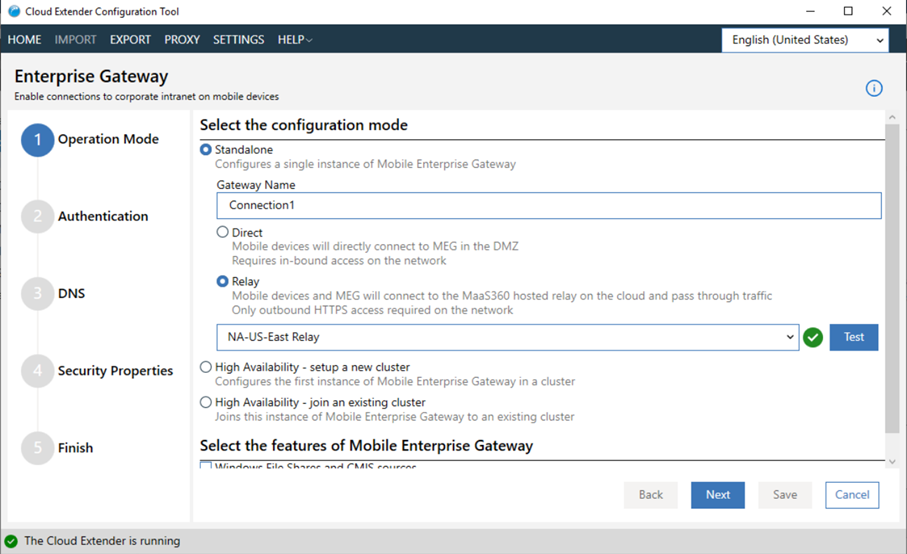
- Provide the name of the gateway. This name is displayed in all MaaS360® Portal workflows.
- From the Relay list, select an available relay server. MaaS360 administrators provision the relay server list during service provisioning. If a regional relay is missing from your list (US, EU, or APAC), contact IBM® Support.
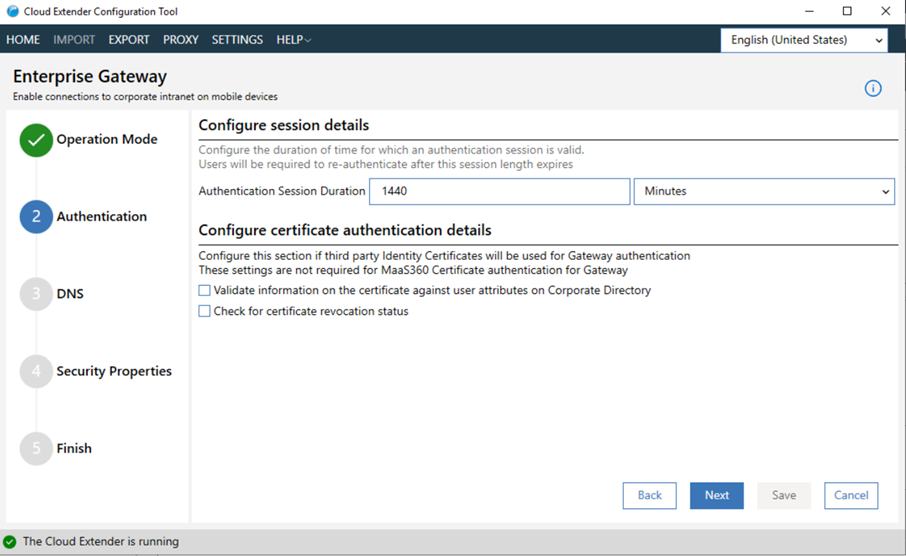
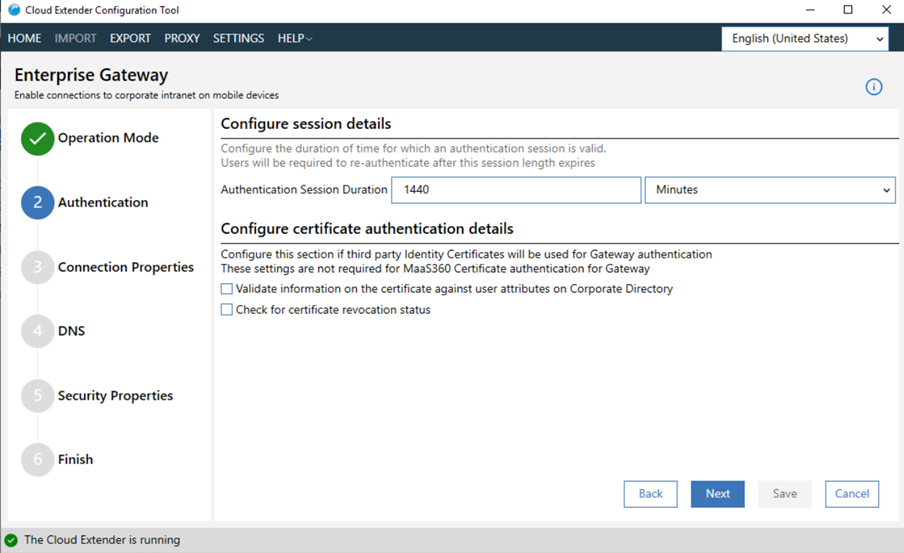
- Configure session and certificate authentication details:
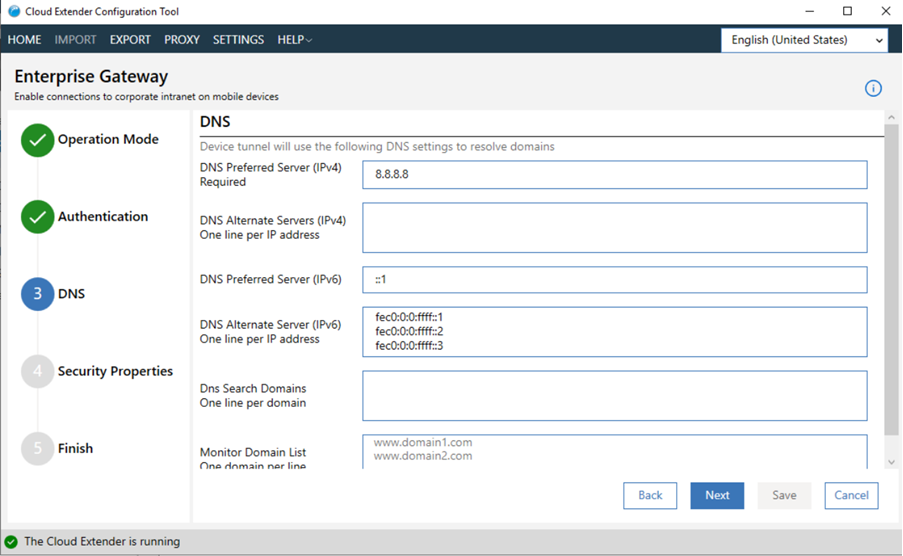
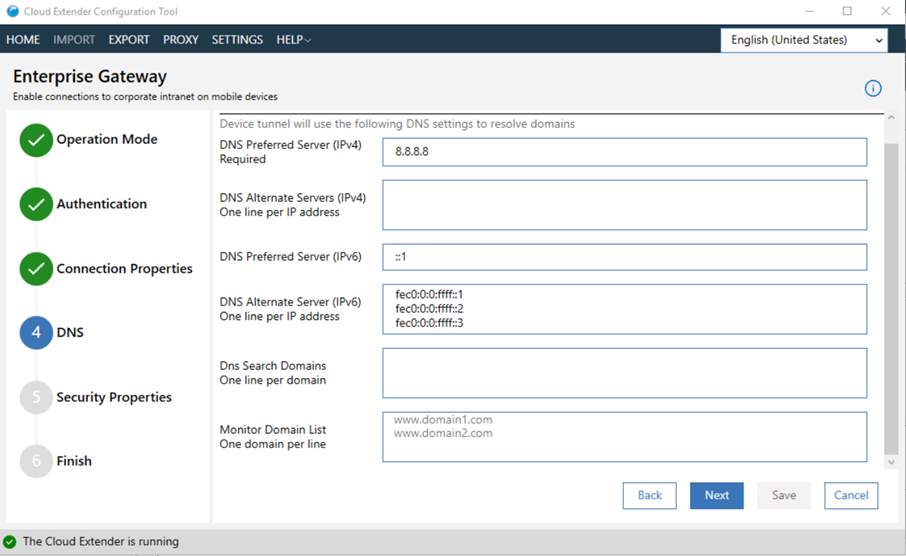
- Configure DNS settings:
- Configure security properties. Accept all Untrusted Certificates to configure the gateway to
ignore certificate exceptions from intranet resources.
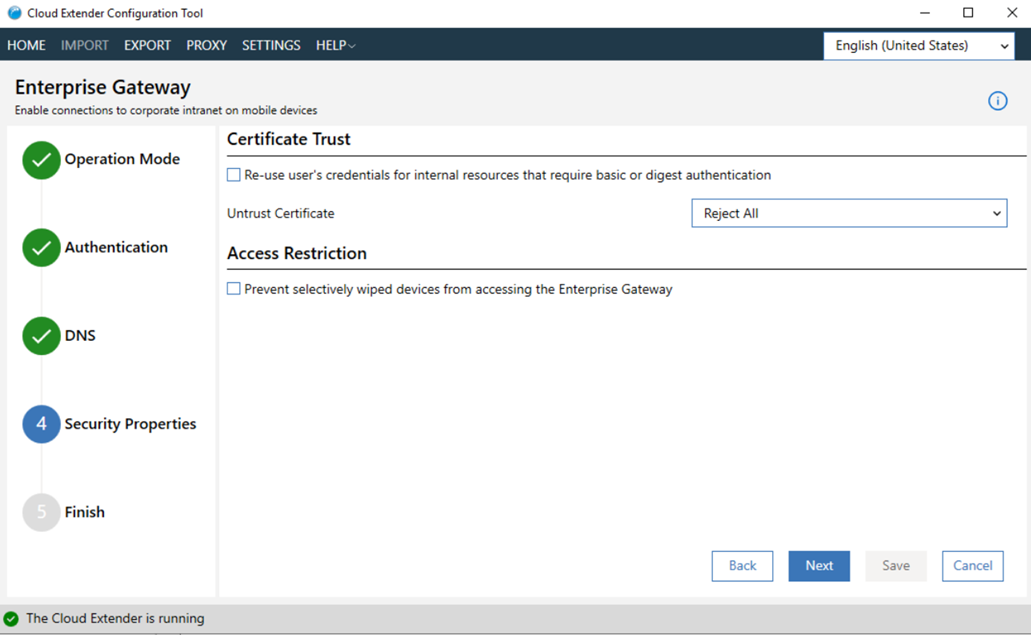
For example, if your intranet site uses a self-signed certificate, then access to this site produces a certificate exception. When you enable this option, the exception is ignored and the request is served by the gateway. For security reasons, disable this option and install the site SSL certificates to the certificate store of the gateway server instead.
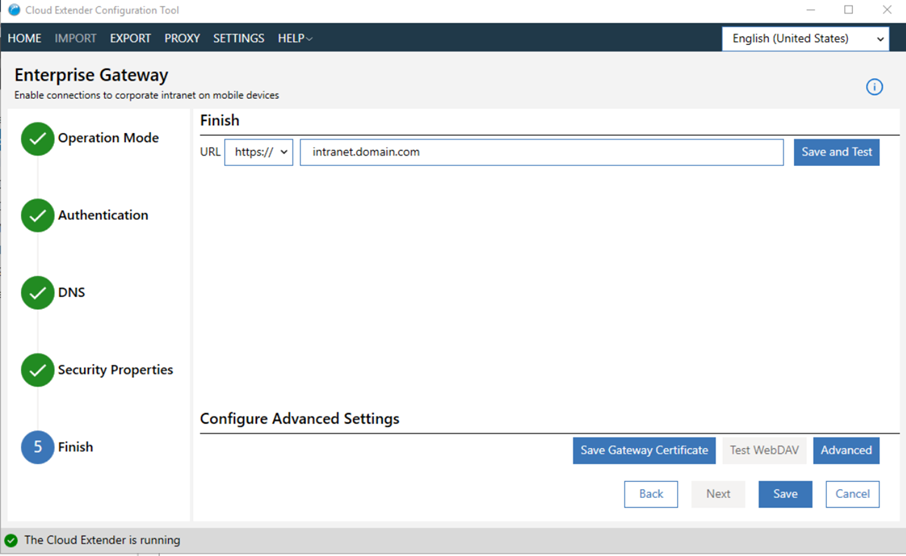
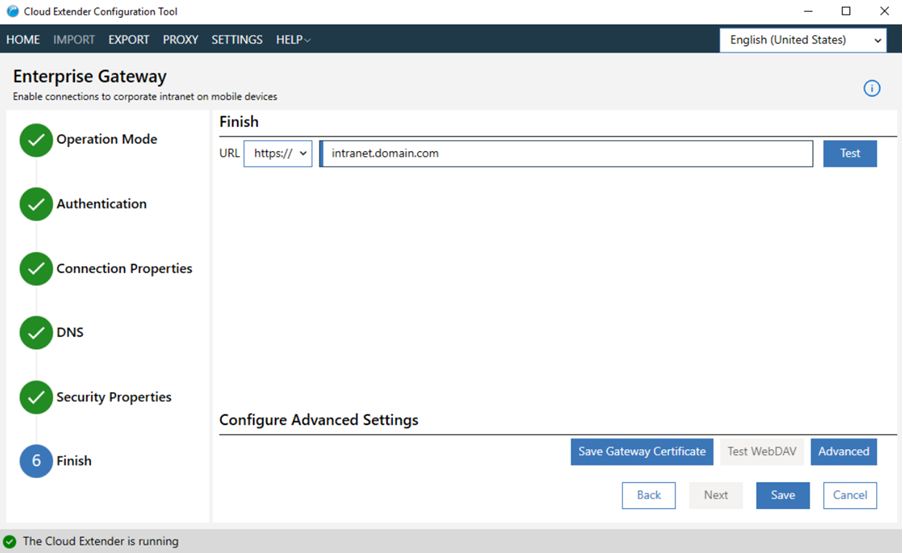
- Test the URL to validate the gateway connection:
- Select Relay:
- To run the gateway in direct mode, configure these settings:
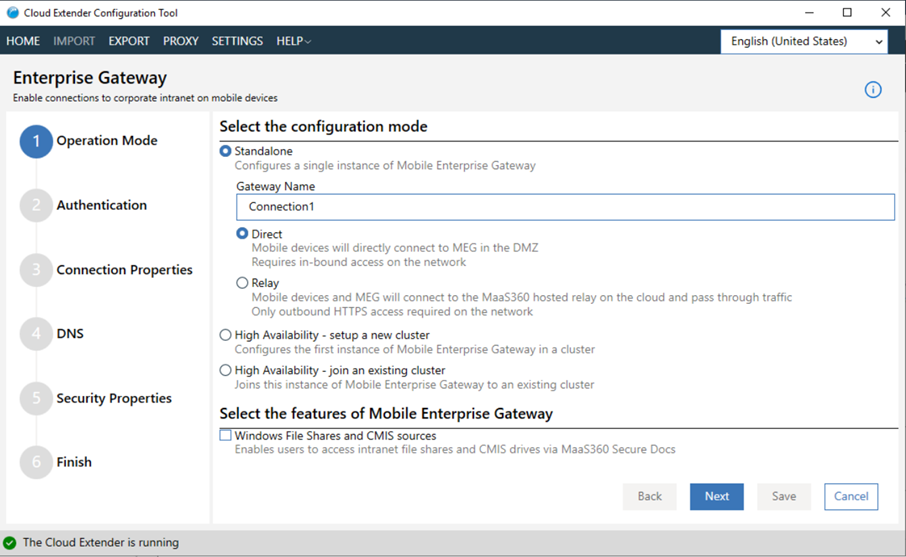
- Provide the name of the gateway in the Gateway Name field. This name is displayed in all MaaS360 Portal workflows.
- Select Direct, and then click Next.
- Configure session and certificate authentication details:
- Configure connection settings:
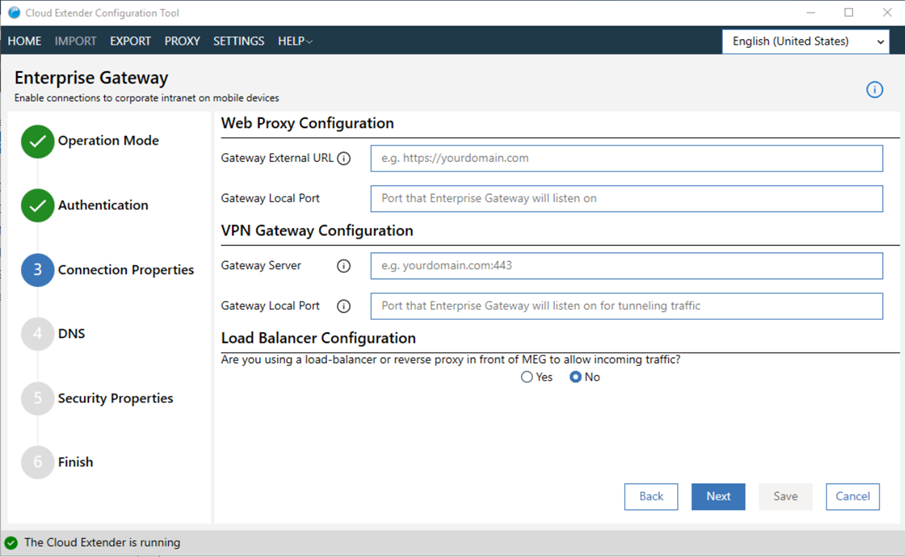
- For Web Proxy Configuration:
In the Gateway External URL and Gateway Local Port fields, provide the gateway URL (or the external URL or host name of your load balancer) if you use a load balancer in front of the gateway. If you do not use a load balancer in front of the gateway, the gateway URL is the host name of this gateway server. This external URL includes the port, if this port is different from the standard ports for HTTP or HTTPS.
- For VPN Gateway Configuration:
In the Gateway Server and Gateway Local Port fields, provide the port that runs the gateway server and listens for requests. If you use a load balancer, make sure that the load balancer redirects traffic to this gateway port. If you do not use a load balancer, the gateway port is any open port on this gateway server.
- For Web Proxy Configuration:
- Configure DNS settings:
- Optional: If you want to configure SSL for Direct Mode, configure these settings:
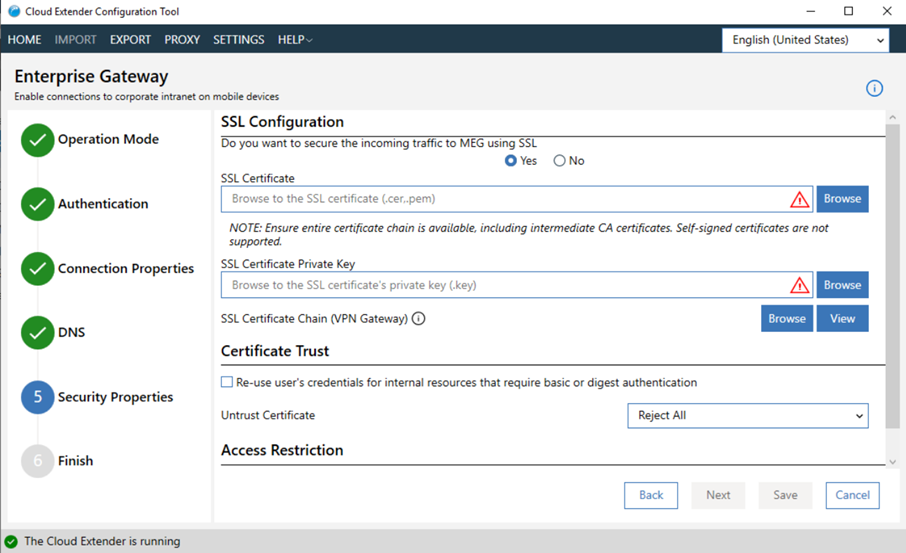
- Select Yes to use SSL.
Use SSL encryption along with AES-256 bit end-to-end encryption to secure communication further between a mobile device and the gateway.
Note: Using SSL encryption is optional. If you choose not to use SSL, the security of the Mobile Enterprise Gateway (MEG) is not compromised.- If you do not use a load balancer, the mobile device uses the SSL certificate that you enter in the SSL Certificate field to initiate an SSL session to the gateway.
- If you use a load balancer, the load balancer uses the SSL certificate that you enter in the SSL Certificate field to initiate an SSL session to the gateway. The load balancer SSL certificate secures the traffic between a mobile device and your load balancer. For more information, see your load balancer documentation.
- In the SSL Certificate field, provide the path to the SSL certificate (PEM) file. If you do not use a load balancer, SSL terminates on your gateway. In this case, you cannot use self-signed certificates. You must receive an SSL certificate from a public certificate authority (CA).
- In the SSL Certificate Private Key field, provide the private key for the SSL certificate (.key) file.
- Select Accept all Untrusted Certificates to configure the gateway to
ignore certificate exceptions from intranet resources. For example, if your intranet site uses a
self-signed certificate, then access to this site produces a certificate exception. When you enable
this option, the exception is ignored and the request is served by the gateway.
For security reasons, disable this option and install the site SSL certificates to the certificate store of the gateway server instead.
- For procedures on how to set up a database, see Setting up a shared database for High Availability (HA).
- Select Yes to use SSL.
- Test the URL to validate the gateway connection:
- To run the gateway in relay access mode, configure these settings: