To connect to Microsoft Azure, map the Azure account information to a functional ID. Then, assign that functional ID to a team.
Before you begin
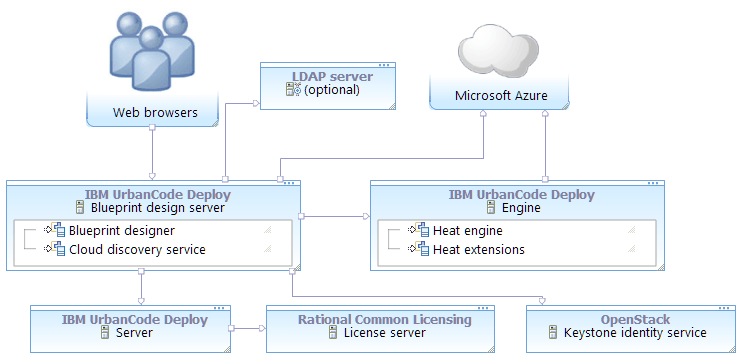
- Obtain an OpenStack Keystone server. The blueprint design server requires a Keystone server to connect to any cloud. You can reuse a Keystone server that is connected to a different cloud, or you can install a Keystone server for use with Azure. See the OpenStack documentation.
- Obtain an engine. The engine version must match the version of the OpenStack
Keystone server. You can use any of the following options for the engine:
- Install an engine. See Installing engines in silent mode or Installing engines in interactive mode.
- If you already have an engine, connect it to the Keystone server as described in Connecting engines to Keystone servers.
- Extend an existing Heat orchestration engine and connect it to the Keystone server. See Extending Heat orchestration engines.
- Create a functional user account on the Keystone server. This user account must be a member of the administrative tenant on the Keystone server. Later, you associate the Azure account information with this functional ID. With this account, users can authenticate to Azure.
- Install the blueprint design server. See Installing the blueprint design server.
- Connect the blueprint design server to the server. See Connecting the blueprint design server to the server.
- Ensure that the blueprint design server can connect to Azure. You can verify the connection path with the curl or telnet commands. For example, make sure that no firewall, proxy, or security settings prevent communication between the blueprint design server and the cloud. The blueprint design server must be able to access the Azure endpoints for the regions that you plan to use.
- Install the Azure command-line client. See https://azure.microsoft.com/en-us/documentation/articles/xplat-cli-install.
- Set up an account on Azure, including a subscription.
- On the Azure web portal, create a resource group. You must place any custom images, virtual networks, and storage accounts that your blueprints use in this resource group.
About this task