
IBM Security and Privacy by Design (SPbD@IBM)
Designing security and privacy into the core of IBM products.
SPbD@IBM is a streamlined and agile set of focused security and privacy practices which reinforces our commitment to embedding security and privacy into the design of our products and services. SPbD@IBM is aligned with the United States National Institute of Standards and Technology (NIST’s) Secure Software Development Framework (SSDF), which drive processes that are required across all business units.
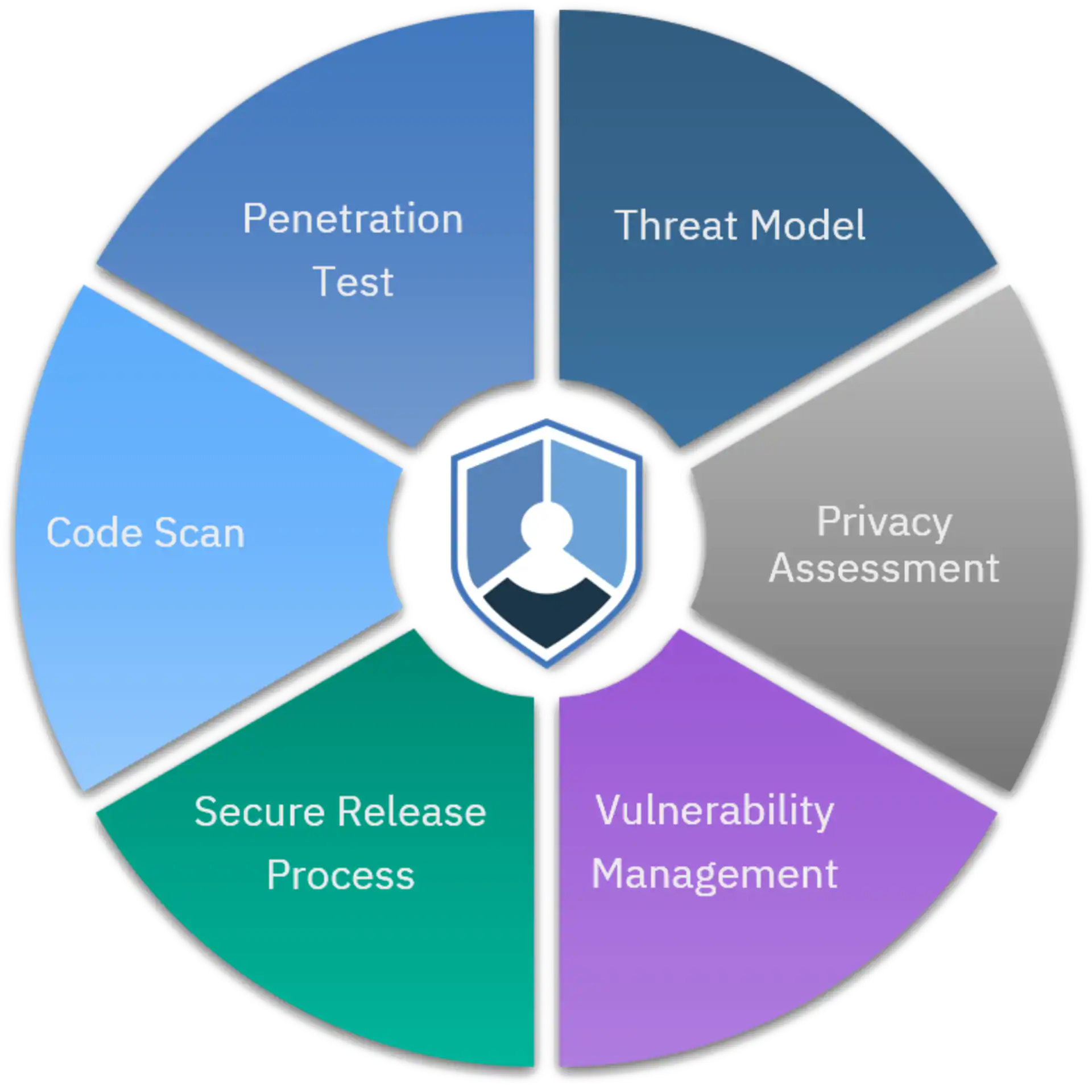
There are three steps in our SPbD@IBM process:
1. Threat Assessments
IBM performs both cyber and privacy threat assessments. We leverage standard industry threat model and privacy impact assessment concepts to help ensure data minimization and adequate data protections are in place from the beginning.
2. Security Testing
System, code, and application security testing are performed in addition to penetration testing and manual ethical hacking. The testing is implemented in a manner that supports agile practices and continuous deployment by being integrated and automated into DevOps pipelines.
3. Release Review
Final individual team and corporate level product reviews prior to GA to help ensure that key foundational security requirements have been fully met.