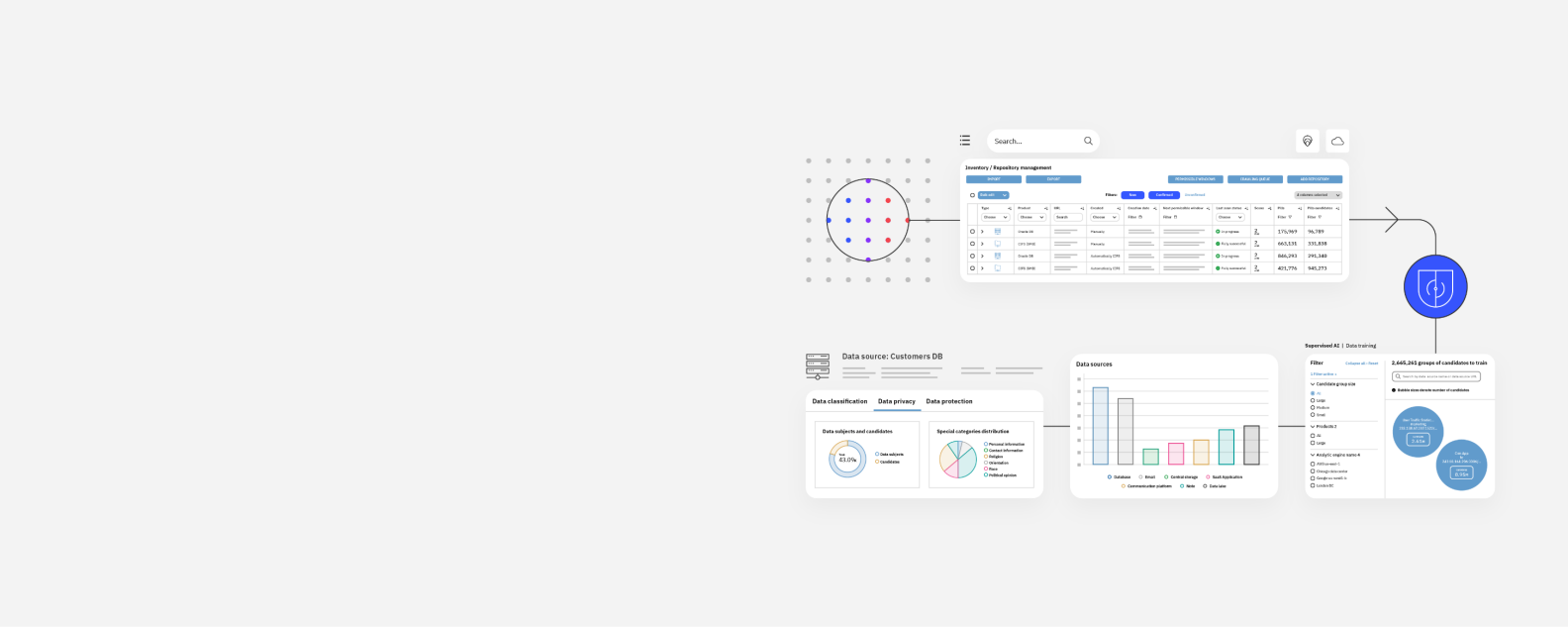
IBM Security Discover and Classify software discovers and classifies sensitive data across on-premises and cloud environments. It forms part of the IBM Guardium family of data security products.
Robust data protection begins by knowing where your sensitive data resides. IBM Security Discover and Classify (ISDC) discovers known and unknown sensitive data on-premises and in the cloud—whether structured, unstructured, in motion or at rest.
ISDC’s network-based analytics, compliance-ready capabilities, and ease of deployment make it a powerful complement to IBM Security® Guardium® and improves your data security posture management.
Check out the X-Force Threat Intelligence Index 2024 for deeper insight into attackers’ tactics and recommendations to safeguard identities
Learn more about the Guardium family of products
100% accuracy in unstructured (flat files) data.
98.6% accuracy in structured (database) date.
9 of 9 categories show IBM Security Guardium as a "strong positive", making it an Overall Leader.
Enhance your existing security tools with precise sensitive data intelligence to prioritize effective actions.
Find and map previously unknown data—at rest or in motion—in the cloud or on premises.
Use scale-up architecture that supports loads of any size irrespective of data source type or location.
Apply automated controls for sensitive data according to business context and risk factors.
Achieve higher accuracy and minimize false positives and negatives in data classification.
Reduce the time and effort needed to discover and classify data in a complex environment.
Use cases
IBM Security Discover and Classify provides automated, near-real-time discovery, network mapping and tracking of sensitive data. Combined with robust data monitorization from IBM Security Guardium Data Protection, it can help you boost operational efficiency, significantly reduce risk and lower costs for your organization.
Managed virtual servers (MVS) are used for structured data discovery and Terabyte (TB) is used for unstructured data discovery. Pricing varies based on number of data sources and configuration of your environment.
We count the number of individual database servers to determine the number of MVS, irrespective of the amount of database schema or data sources on this server.
The amount of uncompressed data on a repository, on a cloud or on premises.
Knowing what data you’re working with is essential when deciding on the most appropriate security and privacy measures.
Learn how the rise in digital technology drives the need for strong data discovery and classification to protect sensitive information.
Learn from the experiences of fellow Guardium users and share your own data protection best practices.
Get centralized visibility, monitoring, compliance, advanced analytics and data source flexibility. Simplify data security and analytics.
Looking to identify shadow data and its movement across applications? Read about the Data Security Posture Management (DSPM) capabilities in Guardium Insights.
Monitor data activity and accelerate compliance auditing and reporting for your data stored anywhere. Discover and classify data and data sources, monitor user activity, and respond to threats in near real time.
Scan your data to detect vulnerabilities, threats and security gaps to help safeguard your data.
Deliver centralized, secured key management with reduced costs and greater operational efficiency.
Encrypt sensitive data in all states and across environments for different types of data, including your files, databases and applications. Address data security and privacy regulations, and control encryption keys for cloud-based data.