Manufacturing becomes the world’s most attacked industry.
For the first time in five years, manufacturing outpaced finance and insurance in the number of cyberattacks levied against these industries, extending global supply chain woes. Manufacturers have a low tolerance for downtime, and ransomware actors are capitalizing on operational stressors exacerbated by the pandemic.

How They’re Getting in: Top infection vectors for manufacturing
Malware uses sophisticated new tricks to infiltrate.
As defenses grow stronger, malware gets more innovative. Attackers are increasingly using cloud-based messaging and storage services to blend into legitimate traffic. And some groups are experimenting with new techniques in encryption and code obfuscation to go unnoticed.
In the age of triple extortion, business partners may put you at risk.
Triple extortion is an increasingly popular tactic of encrypting and stealing data, while also threatening to expose the data publicly and engage in a distributed denial of service (DDoS) attack against the affected organization unless a ransom is paid.

Ransomware gangs are also looking to their primary victim’s business partners to pressure them into paying a ransom to prevent their own data leakages or business disruptions caused by a ransomware attack.
Multi-factor authentication shows promising signs of success.

Multi-factor authentication (MFA) can decrease the risk of several different types of attack, including ransomware, data theft, business email compromise (BEC) and server access. But BEC is rising in regions where MFA is seemingly less common, like Latin America.
Big brands are the big ticket into your organization.
Phishing was 2021’s top infection vector, and the brands that were most imitated in phishing kits are among the largest and most trusted companies: Microsoft, Apple and Google.

Four out of 10 attacks start with phishing, but X-Force Red, IBM’s global team of red team hackers that break into organizations and uncover risky vulnerabilities, reports that adding vishing (or voice phishing) to a targeted phishing campaign makes the effort three times as effective as a classic phishing campaign.
Vulnerabilities rise sharply as the Internet of Things expands.
The number of vulnerabilities related to Internet of Things devices increased by 16% year over year, compared to a growth rate of only 0.4% for vulnerabilities overall. For industrial control systems, the rise was even more dramatic at 50%—an elevated risk as threat actors seek to disrupt the manufacturing and energy sectors.

Connectivity Issues: Number of vulnerabilities identified each year since 2011
As organizations move to the cloud, attackers follow.
Malware targeting Linux environments rose dramatically in 2021—a surge possibly correlated to more organizations moving into cloud-based environments, many of which rely on Linux for their operations.

A threat actor to know: A gang called LemonDuck caused several compromises observed by X-Force in 2021. LemonDuck malware evolved from cryptomining and has since built a large botnet of compromised devices; it targets both Linux and Windows systems. LemonDuck campaigns capitalize on news events for phishing lures.
A single gang initiated 37% of ransomware attacks, an organization’s biggest threat.
Ransomware remains the leading type of attack, although it decreased as a share of overall attacks. Why? Our theory is law enforcement action. The REvil operation accounted for a whopping 37% of ransomware attacks that X-Force remediated last year before the gang shut down in October 2021. Members of the gang were arrested, but many ransomware groups that disband later reemerge under new names. The frequency of ransomware attacks tends to shift throughout the year, often increasing in May and June. Ransomware attacks appear to decrease in late summer or early fall, with January having the least amount of activity.
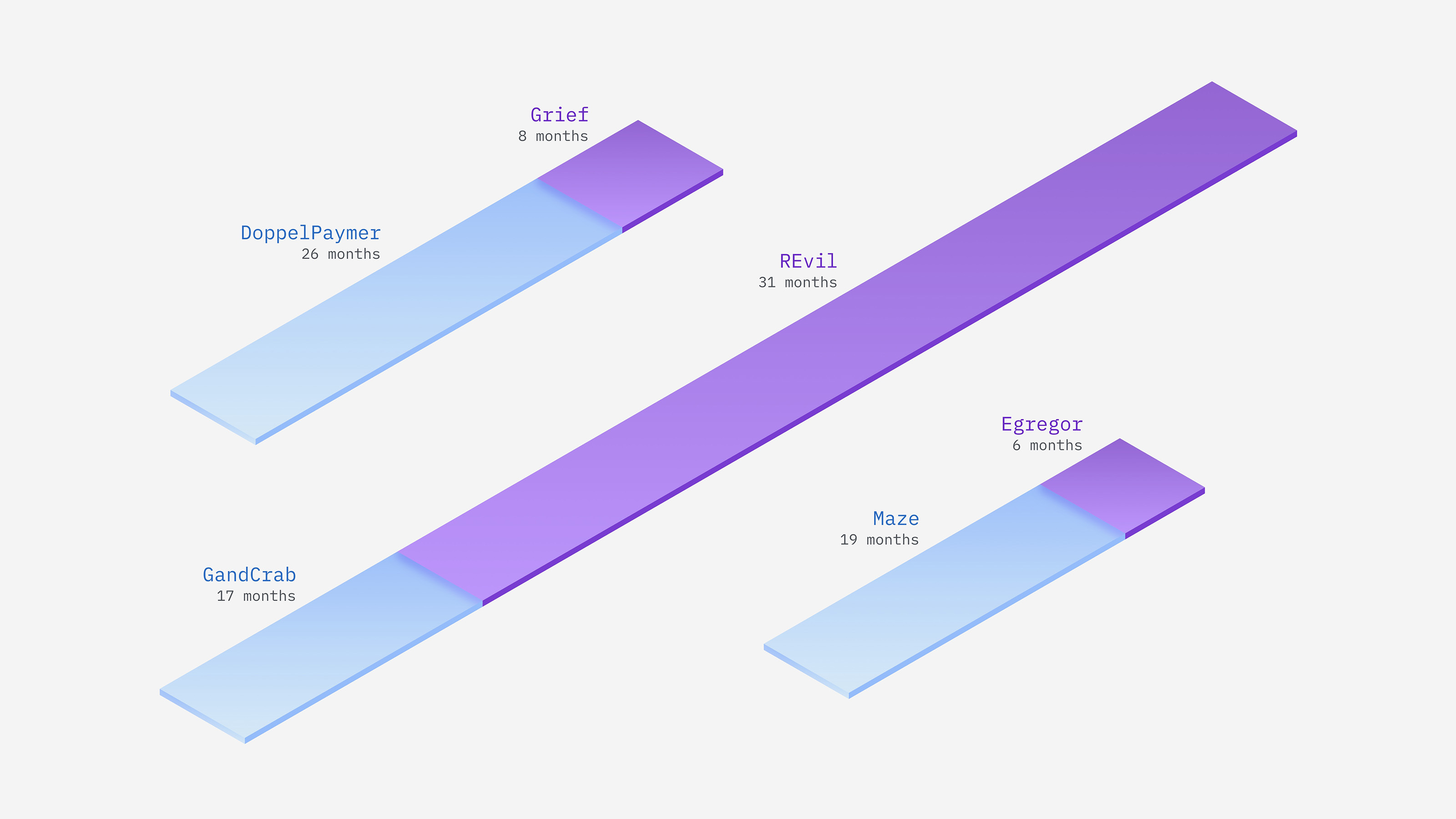
Malfeasant Makeovers: Notable ransomware gang rebrands