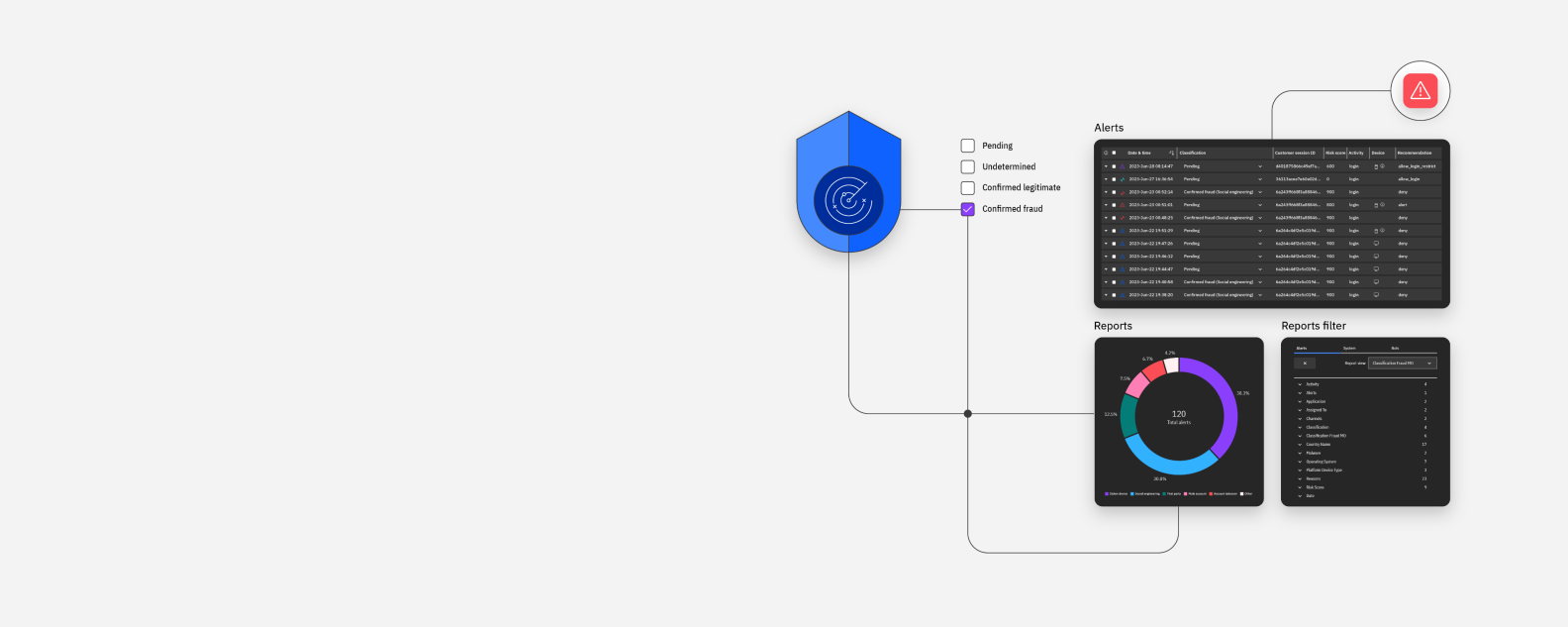
IBM Security® Trusteer® Pinpoint Detect is SaaS for real-time risk assessment and fraud detection. It is part of the Trusteer family of products in the IBM Security® portfolio.
IBM Security Trusteer Pinpoint Detect helps organizations quickly and transparently establish digital identity trust throughout a seamless customer experience without compromising on security. It is real-time, cloud-based risk assessment software that analyzes online identities to differentiate between malicious users and true customers. Trusteer Pinpoint Detect uses artificial intelligence and machine learning to protect digital channels against account takeover and fraudulent transactions and to detect user devices infected with high-risk malware.
In 2023, organizations saw a 71% spike in cyberattacks caused by exploiting identities. Check out the new report to learn how to best safeguard identities.
KuppingerCole Leadership Compass - See why Trusteer was named an overall leader in the latest Leadership Compass: Fraud Reduction Intelligence Platforms (FRIP).
Trusteer assesses session risk to authenticate users throughout the omnichannel lifecycle.
Fraud and security experts maintain adaptable policies.
Trusteer uses advanced detection models and global consortium data to achieve high detection rate and reduce false positives.
Detect legitimate and malicious users transparently.
Assess risk in every session and activity by leveraging our global device intelligence consortium.
Identify and prevent fraudulent transactions.
Get immediate protection through continuous data analysis.
Use a cognitive approach for behavioral profiling of user biometrics across mobile and desktop.
Detect a wide range of malicious mobile and desktop malaware targeting credential theft and account takeover.
Detect legitimate and malicious remote access tools in a cyberattack.
Access advanced models for detecting mule rings used in fraudulent transactions.
Protect against on-device fraud attacks used in social engineering and scams.
Use cases
Learn the potential ROI that enterprises may capture by deploying IBM Security Trusteer.
See how scoring enables seamless authentication customer experiences.
Learn about a new trend in financial mobile malware that targets Android and is replacing the classic overlay approach.
When using IBM Cloud® offerings, your company can scale and adapt quickly to changing business needs without compromising security, privacy or risk levels. Learn more about IBM Cloud security.
This offering meets the following industry and global compliance standards, depending on the edition you choose.
- EU-US Privacy Shield and Swiss-US Privacy Shield Framework
- FFIEC for Financial USA
- ISO 27001
- SOC2 Type 2 (SSAE 16)
To learn about the compliance and certifications for a specific offering edition, consult the Cloud Services data security and privacy data sheets.
Seamlessly assess the risk of new and guest digital identities.
Access an embedded security library for native mobile web applications.
Detect and remediate malware and identify phishing attacks within minutes.
Frequently asked questions
Get answers to the most commonly asked questions about this product.
With Pinpoint Detect, Trusteer provides comprehensive digital identity insights to seamlessly determine whether the user accessing the service is the true user owning that identity.
Companies often have to make tradeoffs between security and customer experience in today's threat landscape. Digital identity trust technology lets companies measure both risk and trust to keep the customer’s digital journey secure while still offering a better digital experience.
IBM Security Trusteer Pinpoint Detect enables the collection of intelligence from digital endpoints—that is, the organization’s mobile app, mobile browser or desktop browsers—and combines the information with IBM worldwide intelligence sources and complementary third-party intelligence sources.
IBM Security Trusteer Pinpoint Detect takes 5 context domains into consideration when evaluating risk: user identity and attributes, device information and hygiene, activity being performed or resource being accessed, environmental factors such as location and IP networks, and behavioral information.
Pinpoint Detect works transparently, without the need for downloading executable files or plugins to the user's computer. For web applications, Pinpoint uses code embedded into the web page. For mobile applications, the organization’s app uses the IBM Security Trusteer Mobile SDK.
As a software as a service (SaaS) solution, Pinpoint Detect can deploy quickly and easily. The best practice is to follow a four-stage deployment process, which includes scoping, implementation, launch and validation with training.
Launch the interactive demo for a step-by-step walkthrough, or get more detailed implementation techniques at the Security Learning Academy.
IBM Security Trusteer Pinpoint Assure assesses the risk of new or anonymous users. IBM Security Trusteer Pinpoint Detect continuously assesses the digital identities of known or enrolled users. Finally, IBM Security Trusteer Pinpoint Verify allows organizations to confirm trust for high-risk users with strong authentication.
Launch the interactive demo for a step-by-step walkthrough, or get more detailed implementation techniques at the Security Learning Academy.
IBM Trusteer products are primarily used by banks, financial institutions, insurers, retailers, telecommunications, travel and transportation industries.
In general, software as a service (SaaS) solutions offer the ability to deploy quickly and easily. The SaaS deployment also allows Trusteer to employ agile, ongoing threat protection that uses AI and analytics to identify new threats and patterns.