IBM Z® Security and Compliance Center is an integrated set of microservices that collects evidence data from participating IBM software components and products. It works with products and elements on your IBM Z platform running z/OS or Linux on Z system to collect and validate compliance data.
IBM LinuxONE Security and Compliance Center offers function equivalent to IBM Z Security and Compliance Center for the LinuxONE platform.
Compliance audits are often a major time drain, taking staff away from more pressing efforts to satisfying auditor’s demands and stitching together data from multiple sources. Fighting mainframe compliance “drift"—maintaining, updating and adding new processes for compliance—can be a costly effort.
The IBM Z® and LinuxONE Security and Compliance Center will help take the complexity out of your compliance workflow and the ambiguity out of audits.
IBM Z Security and Compliance Center
IBM LinuxONE Security and Compliance Center
You might reduce audit prep from one month to one week and reduce the team on audit prep by over 40%.
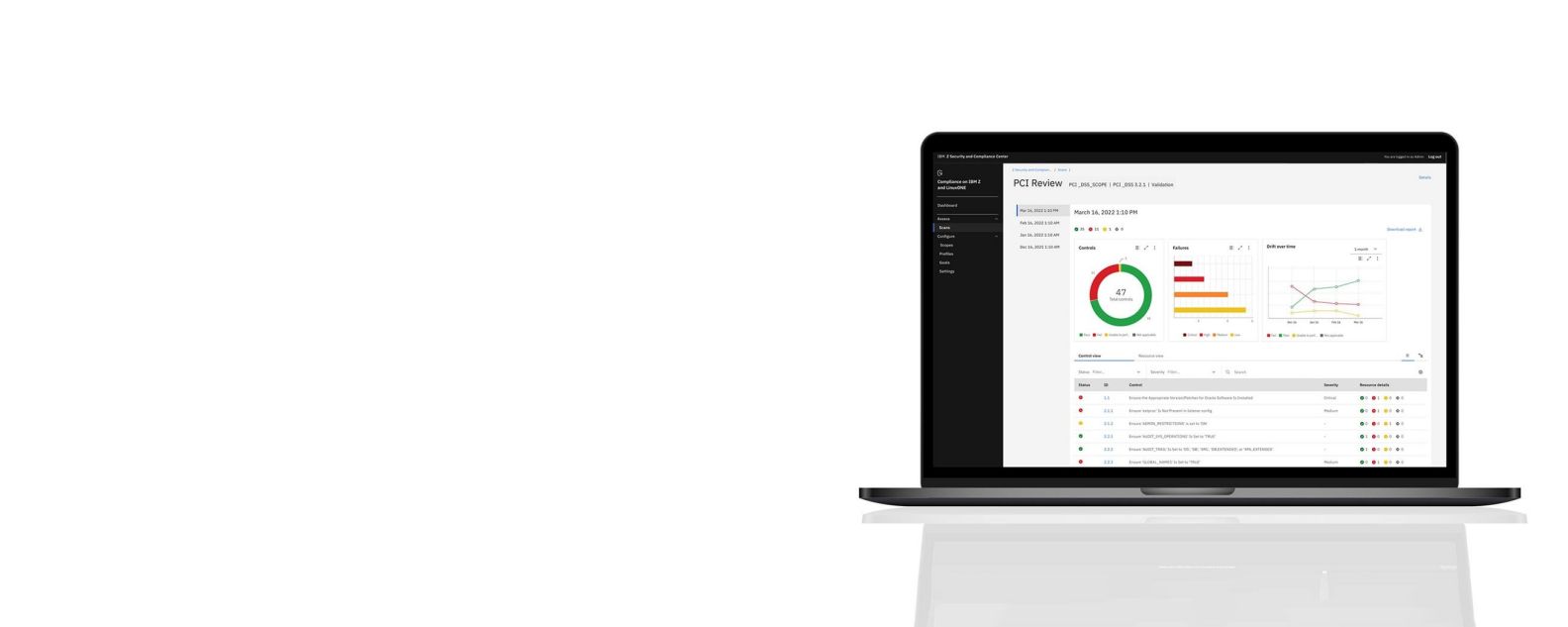
Automated tracking stays current, even as regulations drift. A unified dashboard tracks ongoing compliance.
Clarify processes and reduce the risk of less-experienced users misinterpreting changing regulations.
Automate data validation against goals to help increase visibility into potential compliance oversights.
CISOs and auditors receive current views of compliance to accelerate the remediation process.
Automate data collection and validation against goals to increase visibility into compliance oversights.
Regulatory controls are translated to be IBM Z and LinuxONE-specific.
See progress with a consolidated view of baseline standards.
System-generated, time-stamped evidence for added security.
Security and compliance management are driven by triggered evidence.
Adjust to your needs, validation thresholds, and specify scan timing.
Sysplexes deliver and store compliant, relevant data.
Use cases
Measure and verify the effectiveness of your mainframe security policies and security compliance.
Automate and centrally manage your organization’s compliance to regulatory and internal standards.
Protect your mainframe resources with tools that manage and control access to valuable z/OS data.
Protect your business data against cyberthreats—inside your data center and throughout your hybrid cloud—with IBM Z and LinuxONE.
Make the best use of IBM Z Security and Compliance Center and learn to map all the necessary IBM Z security capabilities to meet compliance and improve your security posture.
Learn how to safeguard your people and data from cyberattacks. Get deeper insight into attackers’ tactics and recommendations to proactively protect your organization.
Frequently asked questions
The IBM Z Security and Compliance Center can be deployed from z15 or z16®. In addition, it can be deployed natively on LinuxOne. IBM Z Security and Compliance Center can collect data from any system running z/OS 2.4 version or newer.
Yes, this solution requires the use of OpenShift® Container Platform on Linux on IBM Z. Additionally, we now support IBM zCX Foundation for Red Hat® OpenShift (for native z/OS deployment).
Yes, if you are running z/OS 2.4 or later.
The initially available version of the IBM Z Security Compliance Center will feature predefined 1-to-1 mappings of IBM Z controls to requirements specified in the following standards.
- PCI DSS v3.2.1
- NIST SP800-53
- CIS Benchmarks
Additional standards will be considered in the future based on user feedback.
Yes, you can create your own profiles and groups of controls using a selection of hundreds of technical checks that the IBM Z Security Compliance Center can perform out of the box. You can also import an extensive set of predefined mappings as a basis for your security procedures.
Through this process, the application may be used to prepare your organization for regulatory frameworks not covered by initially available predefined mappings, as well as for internal requirements that are specific to your organization.
Yes, for z/OS systems you can select which LPARs will be in the scope of your scan.
The IBM Z Security Compliance Center automates the collection of compliance relevant data on IBM Z and Linux on IBM Z.
The application contains predefined 1-to-1 mappings of security controls written for IBM Z components (such as RACF, Db2, IBM CICS, IBM IMS, and IBM MQ) to requirements from regulatory frameworks (such as PCI DSS). These mappings were defined by the IBM Z Security team and have been validated with auditors.
Additionally, the solution includes an interactive, customizable dashboard displaying the security controls validated for each requirement, as well as which resources passed and failed. The solution also reports on compliance drift: how compliance posture has changed from one point in time to another.
Yes. You can view detailed scan results in the IBM Z Security Compliance Center dashboard, or a report generated by the application.
For each technical check, you can view a list of all the IBM Z resources that have passed and failed across multiple sysplexes.
You may also view the logic of each scan performed by the application to see exactly what it checked.
The IBM Z Security Compliance Center is equipped with a microservice which sends an ENF signal to all compatible IBM Z components, triggering them to generate compliance data in an enhanced SMF record that has been custom built for this application.