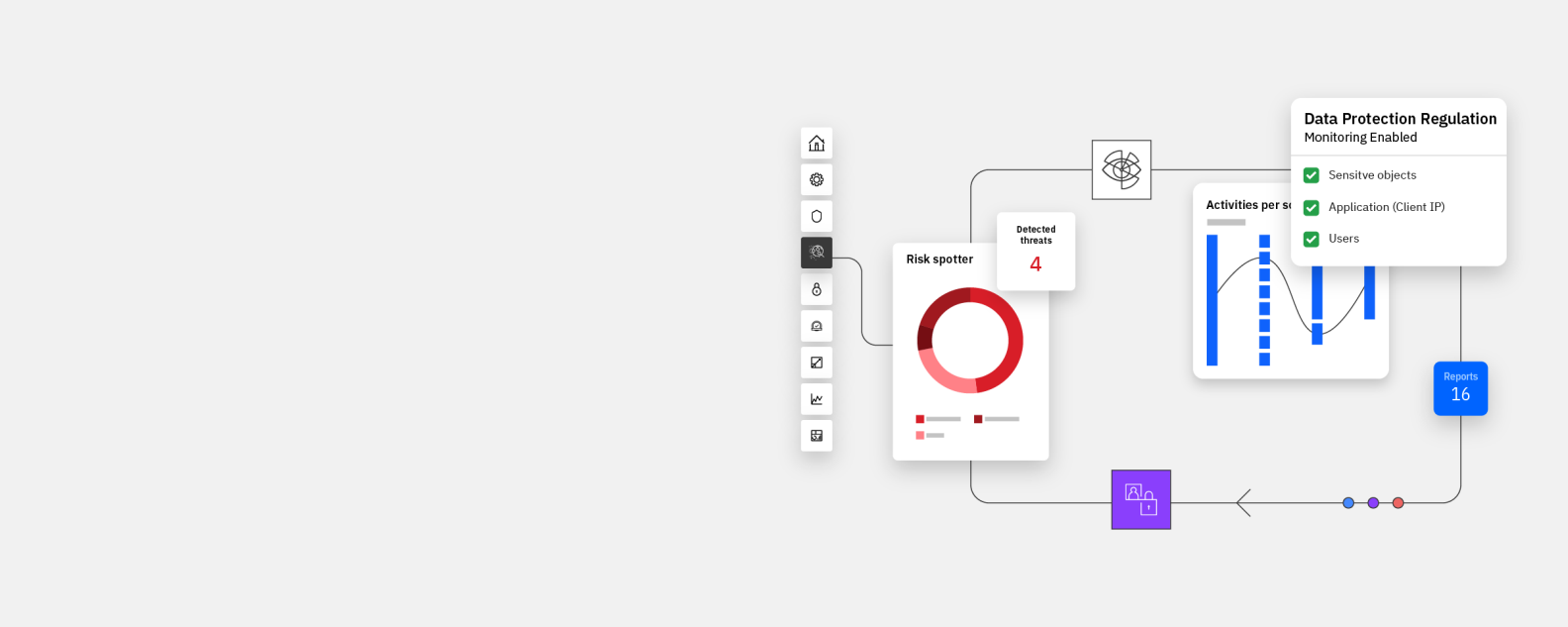
IBM Security® Guardium® Data Protection is data security software in the Guardium family of IBM Security® products. It is comprehensive data protection software that guards on-premises and cloud data stores through features such as data activity monitoring and analytics, near real-time threat response workflows, and automated compliance auditing and reporting.
IBM Security Guardium Data Protection supports a modern, zero-trust approach to data security. No matter where your data resides you can have comprehensive security.
Discover and classify sensitive data across major data repositories, from AWS, DBaaS, and unstructured data in files to on premise mainframes and structured data environments.
Comprehensive activity monitoring and flexible demployment options for quick and intelligent response to advanced threats.
Streamline and automate data compliance workflows using prebuilt templates for regulations including PCI DSS, SOX, HIPAA, GDPR, CCPA and many more.
Learn about effective strategies to fortify your data residency with compliance measures.
Check out the X-Force Threat Intelligence Index 2024 for deeper insight into attackers’ tactics and recommendations to safeguard identities
Hear experts discuss data security strategies for a gen AI world in 2024
The study found a 406% ROI with benefits of USD 5.86 million over 3 years.
The study revealed a 70% reduction in time spent on auditing.
The study calculated that 25% of data security analysts’ time was saved.
Preinstalled capabilities enable faster compliance and data security. Compliance tagging, prebuilt policies, easy-to-use workflows and long-term data retention help speed time to value, so you can meet various compliance requirements such as PCI DSS, GDPR and CCPA in a shorter amount of time.
A data protection strategy with centralized policy management and enforcement across hybrid multicloud environments helps organizations break down silos, accelerate response, and reduce risk to the business with actionable intelligence from a central location.
Actionable, high-priority events are automatically shared with SIEM and SOAR solutions to reduce response times, remove the need for manual action and improve the quality of the data being analyzed, significantly reducing the cost of your SIEM.
Enable your team to quickly discern and focus on the most significant threats with actionable intelligence. Quickly monitor security policies and sensitive data access control, privileged user actions, change control, application user activities and security exceptions for faster remediation.
Enforce security policies that protect data across the enterprise—for all data access, change control and user activities. Guardium supports deployment on several cloud platforms, including Amazon AWS, Google, IBM Cloud, Microsoft Azure and Oracle OCI.
Containerized orchestration supports elastic scalability and flexible deployment options. Evolve your data security as your data and IT infrastructure change and grow—while reducing costs.
For agent-based monitoring, Guardium supports S-TAPs (installed at the data source) and External S-TAPs (installed inline for containerized and cloud data sources). Supported agentless options include Universal Connector plug-ins and cloud event streams (for example, AWS Kinesis and Azure Event Hubs).
The IBM Security® Guardium® Vulnerability Assessment scans data infrastructure such as databases, data warehouses and big data environments—both on premises and in the cloud—to detect vulnerabilities and suggest remedial actions based on benchmarks from STIG, CIS, CVE and other configurations.
IBM Security Guardium Data Protection is built to scale seamlessly from one data source to tens of thousands with little to no impact on performance. To support this immense scalability and facilitate better management of load balancing, the platform automatically adapts to changes in the data center, an ideal feature when you need to support large deployments and frequent changes.
IBM Security Guardium provides a data security and compliance solution designed to help clients locate risks, classify them and take action to protect sensitive data residing on premises and in the cloud. By integrating Guardium Data Protection and Guardium Insights, you can streamline your architecture, increase agility and improve response to threats and business requirements, all while supporting your specific business needs.
Guardium Data Protection can integrate with IBM Security® Verify and other identity management solutions (such as AWS Secrets Manager and CyberArk) for security automation use cases such as securely storing, provisioning and auditing your Guardium data source credentials.
Guardium helps surface data-level security threats and can improve security operations with integrations to ServiceNow and to SIEM solutions such as Splunk and IBM Security® QRadar® SIEM. It also enables security orchestration and response with IBM Cloud Pak® for Security and IBM Security® QRadar® SOAR.
Guardium agents are available on the IBM Cloud Pak® for Data for proactive monitoring of hosted containerized database services and data sources external to the cloud pak. These agents also provide separation of duties between database access and the processes responsible for monitoring behavior.
IBM Security Discover and Classify provides automated, near real-time discovery, network mapping and tracking of sensitive data. Combined with the robust data monitoring provided by Guardium Data Protection, it can help your organization boost operational efficiency, significantly reduce risk and lower costs.
Guardium Data Protection for Databases provides automated data discovery and classification, near real-time activity monitoring, and machine learning analytics to discover unusual activity around sensitive data stored in databases, data warehouses and other structured data environments. The solution supports data on IBM Db2®, Oracle, Teradata, Sybase, Microsoft® SQL Server, Windows®, UNIX®, Linux®, AS/400 and z/OS®, and Hadoop NoSQL. It also supports key enterprise resource planning, CRP and custom applications.
Guardium Data Protection for Big Data provides full visibility on data activity, detecting unusual activity around sensitive data with near real-time data monitoring and machine learning analytics. The solution learns user access patterns to detect suspicious activity, giving administrators the option to block access or quarantine users to defend against internal and external threats. It accelerates compliance workflows through a prebuilt regulation template and supports both Hadoop and NoSQL environments.
Guardium Data Protection for Files provides automated discovery and classification of unstructured data in files and file systems, including NAS, SharePoint, Windows, Unix and Linux, to help you better understand and control unstructured data risks. Machine learning analytics detect unusual activity around sensitive data with intelligent access management and file activity monitoring across files and file systems.
Guardium Data Protection for z/OS enables you to deploy on-premises mainframes, including IBM z Systems® with data protection built in. The solution protects against threats by automating data discovery and classification, with near real-time activity monitoring and machine learning analytics. Alerts are sent to SIEM solutions for correlating threats and streamlining response. You can also proactively assess vulnerabilities and misconfigurations in your Db2, information management system and data sets.
Guardium Data Protection for Database Services is optimized to provide automated data discovery and classification, near real-time activity monitoring, and machine learning analytics to sensitive data stored in database-as-a-service (DBaaS) platforms and cloud-native platforms, such as IBM Cloud Pak for Data. The solution supports databases consumed as a service from the cloud, including AWS RDS and Azure Database-Platform-as-a-Service.
Guardium Data Protection enables you to scale and innovate in AWS while safeguarding sensitive data. You will quickly achieve smarter, more unified data protection across your hybrid AWS cloud environment with a unified set of powerful security controls, including discovery and classification, vulnerability and risk assessments, near real-time monitoring and alerting, security policy controls, advanced analytics, and integration across the security stack.
Use cases
Find threats faster by enhancing data security across complex environments with Guardium Data Protection V12.
Get an overview of the Data Security Platforms market, along with guidance and recommendations for finding the sensitive data protection and governance products that best meet clients’ requirement.
Learn more about how to protect your data wherever it resides with the IBM Security Guardium platform.
Learn how to integrate data security and governance platforms to protect data, enhance operations and reputation, and boost productivity.
Read a senior analyst's perspective on the importance of data compliance.
Scan your data to detect vulnerabilities, threats and security gaps.
Get centralized visibility, monitoring, compliance, advanced analytics and data source flexibility. Simplify data security and analytics.
Looking to identify shadow data and its movement across applications? Read about the Data Security Posture Management (DSPM) capabilities in Guardium Insights.
Enable zero-trust based discovery and classification of sensitive and regulated data, wherever it resides, structured or unstructured, at rest or in motion.
Deliver centralized, secured key management with reduced costs and greater operational efficiency.
Encrypt sensitive data in all states and across environments, including your files, databases and applications. Address data security and privacy regulations, and control encryption keys for cloud-based data.
Frequently asked questions
Data security is everyone's business. While security and compliance teams are primary users, the implications of data security is now beyond IT. Data, privacy, lines of business, risk and legal teams all have use cases that are supported by Guardium Data Protection.
Guardium can help address the challenges of having visibility into sensitive data, whether on premises or in the cloud, detecting risky users and suspicious data access and activity, and simplifying data security and data privacy compliance.
Guardium Data Protection wraps security around data with context through data activity monitoring to learn when, where, how and who is accessing data to detect anomalous and non-compliant activity—and dynamically adjust controls and access rights.
Guardium can help accelerate your ability to address data privacy compliance with easy-to-set-up compliance policies and monitoring, a data access audit trail, entitlement reporting and other compliance reports.
Guardium supports data discovery using a policy-based approach. Prebuilt and custom classifier policies can be defined to perform catalog or metadata discovery using sensitive data regexes and patterns. It can also be used to perform exact data match and unstructured data discovery.
Yes, Guardium supports deployment on several cloud platforms. Get more information about deploying Guardium on Amazon AWS, Google, IBM Cloud, Microsoft Azure and Oracle OCI.
Guardium Data Protection provides both agent-based and agentless methods to monitor data sources. It supports multiple monitoring methods under each of these categories based on the type of data source and where it is located—in the cloud or in your data center.
For agent-based monitoring, Guardium supports S-TAPs (installed at the data source) and External S-TAPs (installed in-line for containerized and cloud data sources). Supported agentless options include Universal Connector plug-ins and cloud event streams (for example, AWS Kinesis and Azure Event Hubs).
Guardium provides prebuilt report templates to get started with compliance monitoring for various regulations and standards such as PCI DSS, SOX, HIPAA, GDPR and CCPA. It also offers Workflow Builder to define custom audit workflows and reports that can be tailored to the needs of various teams.
Guardium Data Protection does not directly prevent data loss, but visibility of sensitive data and knowing where it resides is an important part of DLP. The discover and classification capabilities of Guardium help to address those challenges.