IBM Security® Guardium® Insights is a modern data security solution built to adapt to changing environments, connect to critical IT and security tools, streamline compliance and audit processes, and intelligently respond to data threats. Modernize your data security with Guardium Insights and get more out of your data security investments.
Explore the Guardium Insights Standard Edition SaaS environment with a free 30-day trial.
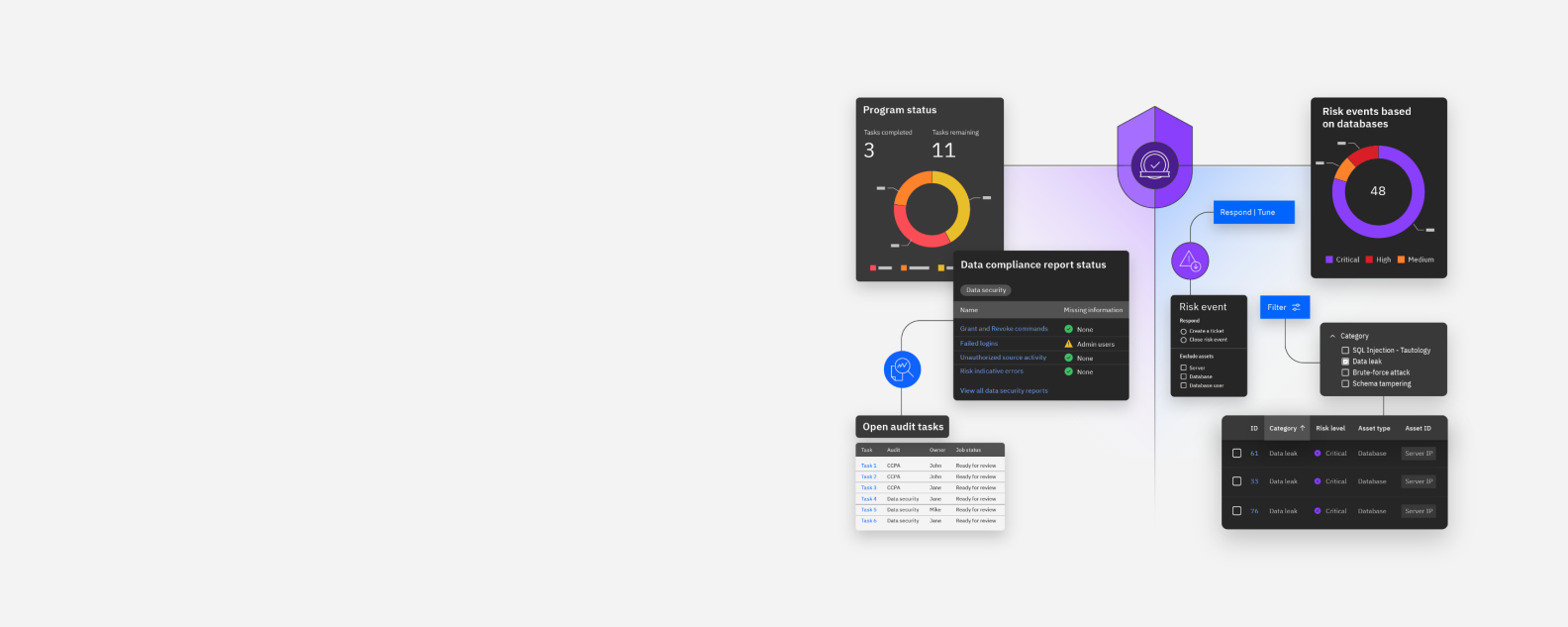
Guardium Insights features in action
Monitor data activity and accelerate compliance auditing and reporting for your data stored anywhere. Discover and classify data and data sources, monitor user activity, and respond to threats in real time.
Rely on zero-trust based discovery and classification of sensitive and regulated data, wherever it resides, structured or unstructured, at rest or in motion. Provide visibility, context and insight into your data.
Encrypt sensitive data in all states and across environments, including your files, databases and applications. Address data security and privacy regulations, and control encryption keys for cloud-based data.
Deliver centralized, secured key management with reduced costs and greater operational efficiency.
Scan your data to detect vulnerabilities, threats and security gaps.