IBM Cloud Hyper Protect Crypto Services is an as-a-service (aaS) key management and encryption solution, which gives you full control over your encryption keys for data protection.
The integrated Unified Key Orchestrator acts as a secure key repository for distributing and orchestrating keys across multiple clouds, enabling quick recovery from key loss or disasters. With Hyper Protect Crypto Services, you can:
- Build on the highest level of security with FIPS 140-2 level 4 certified hardware.
- Experience a worry-free approach to multi cloud key management through the all-in-one as-a-service solution. Benefit from automatic key backups built-in high availability secure business continuity and disaster recovery.
- Manage your keys seamlessly across multiple cloud environments. Create keys securely and bring your own key seamlessly to hyperscalers such as Microsoft Azure AWS and Google Cloud Platform to enhance the data security posture and gain key control.
- Protect data by pervasively encrypting data at rest and in transit with Keep Your Own Key (KYOK). You have full control and authority over encryption keys and no one except you has access to your master key.
Get two production grade crypto units at no charge for 30 days with code HPCRYPTO30
Encrypt integrated IBM Cloud Services and applications with Keep Your Own Key (KYOK). Retain complete control of your data encryption keys with technical assurance and provide runtime isolation with confidential computing.
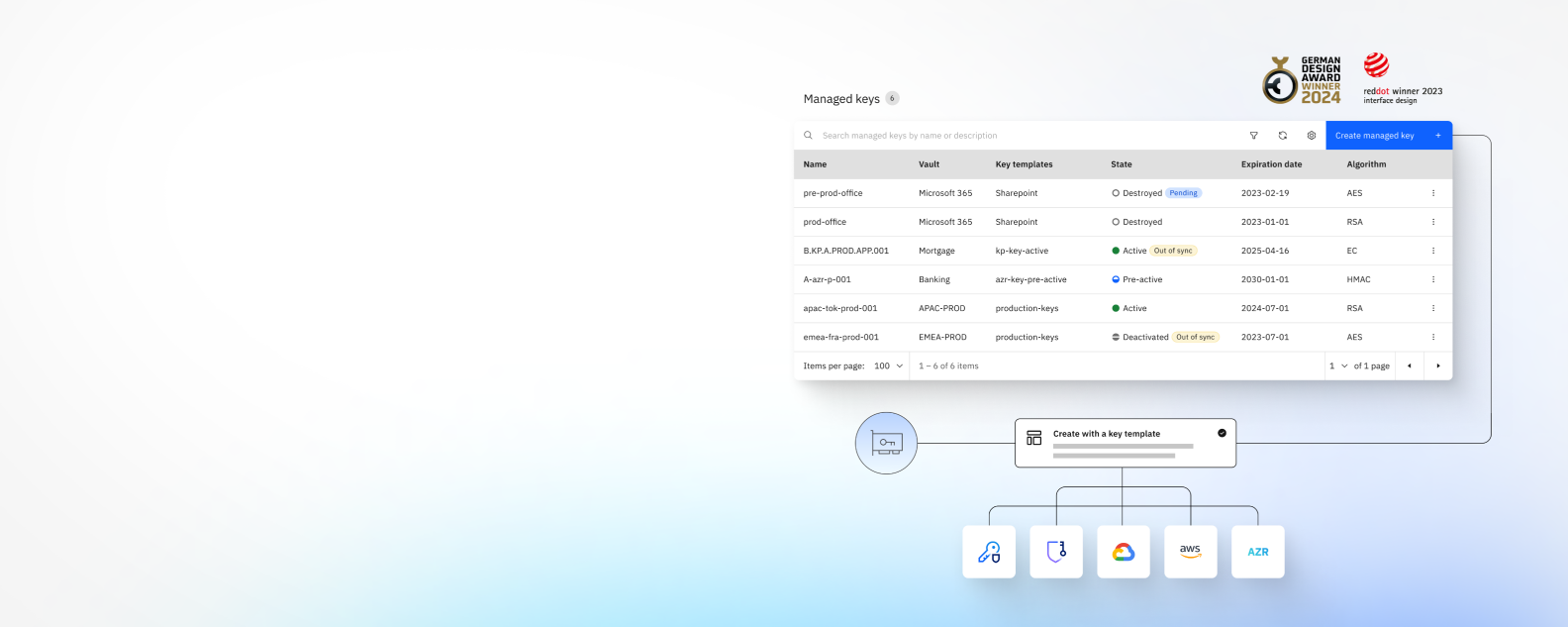
Enhance your security posture and manage keys with Unified Key Orchestrator in a multicloud environment that includes IBM Cloud, Microsoft Azure, AWS, and Google Cloud Platform.Minimize errors and maximize operational efficiency for your key management procedures by leveraging a design-award-winning user experience ( link resides outside ibm.com).
Protect your sensitive data quantum-safe and stay crypto agile. Currently, Hyper Protect Crypto Services provides quantum safe signing with Dillithium. Using a key management system is essential to ensure crypto agility and future-proof your security against potential quantum threats.
Use the FIPS 140-2 Level 4 hardware security module to leverage the highest security level in the industry to store and transfer high-value digital assets in highly secure wallets reliable at scale.
Using keys under your unique control can help you achieve total data privacy and data sovereignty through enhanced data protection and control. Follow several guidances and regulations around the world, such as from NIST, GDPR, C5, ACSC/ASC, ECUC, ENISA, DPDPA, DORA, and more.
Create keys securely and seamlessly in a multicloud environment including Microsoft Azure, AWS, and Google Cloud Platform. Manage your keys under your exclusive control with a generic key lifecycle model based on NIST recommendations.
Encrypt IBM Cloud services with keys under your control through KYOK integration for consistent adoption. Utilize a user-friendly GUI and Cloud APIs to track key lifecycles, ensuring unrecoverable deletion of data regardless of the source application.
Take ownership of HSM. IBM is the first to provide cloud command-line interface (smart cards) for the HSM key ceremony to operate your HSM fully remotely. Key ceremony and smart cards management software is completely made available in the offering (with no extra charge).
Utilize a built-in central backup to redistribute and rotate keys to quickly recover from loss and minimize security threats. High Availability and Disaster Recovery are available in the offering.
Business scenarios of Hyper Protect Crypto Services
Discover procedures, API, and CLI references as well as video resources that assist you to securely manage your keys using Hyper Protect Crypto Services.
Explore an overview of IBM Cloud® Hyper Protect Crypto Services for VMware.
Learn how to securely manage AWS S3 encryption keys using Hyper Protect Crypto Services with Unified Key Orchestrator.
Gain authority over LinuxONE virtual servers for workloads with sensitive data or business IP.
Read the announcement about the new on-premises solution that lets you securely build deploy and manage critical applications for hybrid cloud.
A key management solution that centrally orchestrates and secures the lifecycle of encryption keys across your enterprise for both on premises and multiple cloud environments.