OpenJCEPlus provider
The OpenJCEPlus cryptographic provider is an implementation of the Java™ Cryptography Extensions (JCE) APIs, which include, for example: ciphers, signatures, message digests, MACs and HMACs, secure random number generation, and key generation. In version 8 of the SDK, this security provider was known as the IBMJCEPlus provider.
The OpenJCEPlus provider uses native interfaces to IBM Z® hardware, offering hardware-accelerated cryptographic algorithms where supported.
- z17 adds the Message Security Assist Extension 11
- Through the OpenJCEPlus provider, Java uses the new KMAC-HMAC-SHA function codes that are available to improve Message digest performance
The z17 HMAC performance improvements were added in 11.0.27.0.
Enabling the OpenJCEPlus provider
The OpenJCEPlus security provider is enabled by default due to its position in the JAVA_HOME/conf/security/java.security file. If you want to use a different provider as the default instead, move that provider ahead of the OpenJCEPlus provider in this file.
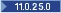 For proper operation of the OpenJCEPlus security provider, install and
initialize the Central Processor Assist for Cryptographic Function (CPACF) hardware function and
configure the random number files. CPACF provides hardware acceleration for various cryptographic
operations and is used by OpenJCEPlus to enhance the efficiency of cryptographic processing by
offloading tasks from the main CPU. Making sure that CPACF is properly initialized is essential for
OpenJCEPlus to function effectively and meet the security and performance demands of enterprise
applications. If CPACF is not installed or the random number files are not available, OpenJCEPlus
might encounter a
For proper operation of the OpenJCEPlus security provider, install and
initialize the Central Processor Assist for Cryptographic Function (CPACF) hardware function and
configure the random number files. CPACF provides hardware acceleration for various cryptographic
operations and is used by OpenJCEPlus to enhance the efficiency of cryptographic processing by
offloading tasks from the main CPU. Making sure that CPACF is properly initialized is essential for
OpenJCEPlus to function effectively and meet the security and performance demands of enterprise
applications. If CPACF is not installed or the random number files are not available, OpenJCEPlus
might encounter a java.security.ProviderException: Failed to initialize OpenJCEPlus
provider error during startup. For more information about the random number files, see
Random number files.
Supported algorithms
The following table shows the algorithms that are supported. More algorithm support is intended for future releases.
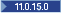 Support for the following algorithms was added in 11.0.15:
Support for the following algorithms was added in 11.0.15:- HMAC-SHA3 algorithms for message authentication code
- SHA3 algorithms for creating message digests

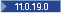 Support for the following algorithms was added in 11.0.19:
Support for the following algorithms was added in 11.0.19:- RSASSA-PSS algorithm for algorithm parameter
- XDH, X25519, and X448 algorithms for key agreement
- EdDSA, Ed25519, Ed448, RSASSA-PSS, XDH, X25519, and X448 algorithms for key factory and key pair generator
- EdDSA, Ed25519, Ed448, and RSASSA-PSS support for signature algorithms

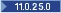 Support for the following algorithms was added in 11.0.25:
Support for the following algorithms was added in 11.0.25:- Password Based Encryption (PBE) algorithm parameter.
- PBEWith<digest>And<encryption>: The password-based encryption cipher algorithm PKCS#5
using the specified message digest (<digest>) and encryption algorithm (<encryption>).
Some combinations of <digest> and <encryption> might not be valid.
- <digest> can have one of the following values: MD2, MD5, SHA, SHA1, HmacSHA1, HmacSHA224, HmacSHA256, HmacSHA384, and HmacSHA512.
- <encryption> can have one of the following values: DES, DESede, TripleDES, 2KeyTripleDES, 3KeyTripleDES, RC4_40, RC4_128, AES_128, AES_256.
- PBEWith<digest>and<encryption>: The password-based secret key factory algorithm
using the specified message digest (<digest>) and encryption algorithm (<encryption>).
Some combinations of <digest> and <encryption> might not be valid.
- <digest> can have one of the following values: MD2, MD5, SHA, SHA1, HmacSHA1, HmacSHA224, HmacSHA256, HmacSHA384, HmacSHA512.
- <encryption> can have one of the following values: DES, DESede, TripleDES, 2KeyTripleDES, 3KeyTripleDES, RC4_40, RC4_128, AES_128, AES_256.
- PBKDF2With<digest>: The password-based secret key factory algorithm using the specified
message digest (<digest>).
- <digest> can have one of the following values: HmacSHA1, HmacSHA224, HmacSHA256, HmacSHA384, HmacSHA512.

 Support for AES/CCM mode was added in 11.0.26.0.
Support for AES/CCM mode was added in 11.0.26.0.
| API | Supported algorithms |
|---|---|
| Algorithm parameter | AES, CCM, ChaCha20, ChaCha20-Poly1305, DESede, DH, DSA, EC, GCM, OAEP, PBE, RSASSA-PSS |
| Algorithm parameter generator | CCM, DH, DSA, EC, GCM |
| Cipher algorithms | AES, ChaCha20, ChaCha20-Poly1305, DESede, PBEWith<digest>And<encryption>, RSA |
| Cipher modes |
AES supports these modes: CBC, CCM, CFB8, CFB128, CFB, ECB, GCM, OFB
DESede supports these modes: CBC, ECB RSA supports these modes: null, ECB, SSL |
| Key agreement algorithms | DH, ECDH, XDH, X25519, X448 |
| Key factory | DH, DSA, EC, EdDSA, Ed25519, Ed448, RSA , RSASSA-PSS, XDH, X25519, X448 |
| Key generator | AES, ChaCha20, DESede, HmacMD5, HmacSHA1, HmacSHA224, HmacSHA256, HmacSHA384, HmacSHA512, HmacSHA3-224, HmacSHA3-256, HmacSHA3-384, HmacSHA3-512 , kda-hkdf-with-sha1, kda-hkdf-with-sha224, kda-hkdf-with-sha256, kda-hkdf-with-shasha384, kda-hkdf-with-sha512 |
| Key pair generator | DH, DSA, EC, EdDSA, Ed25519, Ed448, RSA, RSASSA-PSS, XDH, X25519, X448 |
| Message authentication code (MAC) | HmacMD5, HmacSHA1, HmacSHA224, HmacSHA256, HmacSHA384, HmacSHA512, HmacSHA3-224, HmacSHA3-256, HmacSHA3-384, HmacSHA3-512 |
| Message digest | MD5, SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256, SHA3-224, SHA3-256, SHA3-384, SHA3-512 |
| Secret key factory | AES, ChaCha20, DESede, PBEWith<digest>And<encryption>, PBKDF2With<digest> |
| Secure random | HASHDRBG, SHA256DRBG (default), SHA512DRBG |
| Signature algorithms | EdDSA, Ed25519, Ed448, NONEwithDSA, NONEwithECDSA, NONEwithRSA, RSASSA-PSS, SHA1withDSA, SHA224withDSA, SHA256withDSA, SHA1withECDSA, SHA224withECDSA, SHA256withECDSA, SHA384withECDSA, SHA512withECDSA, SHA1withRSA, SHA224withRSA, SHA256withRSA, SHA384withRSA, SHA512withRSA, SHA3-224withDSA, SHA3-256withDSA, SHA3-384withDSA, SHA3-512withDSA, SHA3-224withECDSA, SHA3-256withECDSA, SHA3-384withECDSA, SHA3-512withECDSA, SHA3-224withRSA, SHA3-256withRSA, SHA3-384withRSA, SHA3-512withRSA |
Supported elliptic curves
secp256r1, 1.2.840.10045.3.1.7, NIST P-256, and X9.62
prime256v1 refer to the same curve. You can use the curve names to create parameter
specifications for EC parameter generation with the ECGenParameterSpec class.
| Curve name | Object identifier | Additional names or aliases |
|---|---|---|
secp112r1 |
1.3.132.0.6 |
|
secp112r2 |
1.3.132.0.7 |
|
secp128r1 |
1.3.132.0.28 |
|
secp128r2 |
1.3.132.0.29 |
|
secp160k1 |
1.3.132.0.9 |
|
secp160r1 |
1.3.132.0.8 |
|
secp160r2 |
1.3.132.0.30 |
|
secp192k1 |
1.3.132.0.31 |
|
secp192r1 |
1.2.840.10045.3.1.1 |
NIST P-192, X9.62 prime192v1 |
secp224k1 |
1.3.132.0.32 |
|
secp224r1 |
1.3.132.0.33 |
NIST P-224 |
secp256k1 |
1.3.132.0.10 |
|
secp256r1 |
1.2.840.10045.3.1.7 |
NIST P-256, X9.62 prime256v1 |
secp384r1 |
1.3.132.0.34 |
NIST P-384 |
secp521r1 |
1.3.132.0.35 |
NIST P-521 |
X9.62 prime192v2 |
1.2.840.10045.3.1.2 |
|
X9.62 prime192v3 |
1.2.840.10045.3.1.3 |
|
X9.62 prime239v1 |
1.2.840.10045.3.1.4 |
|
X9.62 prime239v2 |
1.2.840.10045.3.1.5 |
|
X9.62 prime239v3 |
1.2.840.10045.3.1.6 |
|
brainpoolP160r1 |
1.3.36.3.3.2.8.1.1.1 |
|
brainpoolP192r1 |
1.3.36.3.3.2.8.1.1.3 |
|
brainpoolP224r1 |
1.3.36.3.3.2.8.1.1.5 |
|
brainpoolP256r1 |
1.3.36.3.3.2.8.1.1.7 |
|
brainpoolP320r1 |
1.3.36.3.3.2.8.1.1.9 |
|
brainpoolP384r1 |
1.3.36.3.3.2.8.1.1.11 |
|
brainpoolP512r1 |
1.3.36.3.3.2.8.1.1.13 |
Known limitations
- Only RSA key sizes 512, 1024, 2048, and 4096 are supported.
- RSA key public exponents must be 65537 or greater.
- RSA private keys must be CRT (Chinese Remainder Theorem) keys. Private keys without the CRT parameters are not supported. Generated key pairs will have CRT private keys.
- RSA decryption with the NoPadding option might leave padding bytes in the decrypted text.
- Binary Elliptic Curves are not supported.
- The providers in OpenJCEPlus do not have their own Keystore implementations. Instead, Keystore implementations (JKS, JCEKS, PKCS#12) come from the SUN and SunJCE providers.
- OpenJCEPlus does not support user input for random for EC and XDH Key Pair Generator, hence the user input for random is skipped.
- The version of the underlying native library used by OpenJCEPlus adds
support for some algorithms, which are not yet supported by OpenJCEPlus. These algorithms are:
- The AES-CTR algorithm for data encryption and decryption is not supported.
-
AES-GCM encryption and decryption Cipher.update operations should be done only for large amounts of data that need to be protected, for the following reason. The authentication tag can be validated only on the doFinal (Cipher.doFinal()) operation; if the doFinal operation fails for any reason, all plaintext that is returned from a previous update operation must be discarded. For smaller amounts of data, it is therefore sensible to run only doFinal operations.
AES-GCM is not suggested for use with the cipher stream APIs (CipherInputStream and CipherOutputStream) because these APIs were not designed to deal with the complexities of AES-GCM, such as the one just described.
 RSASSA-PSS signature does not support RSA plain
keys.
RSASSA-PSS signature does not support RSA plain
keys.
 RSASSA-PSS supports SHA-1, SHA-224, SHA-256, SHA-384,
and SHA-512 as input digest algorithms.
RSASSA-PSS supports SHA-1, SHA-224, SHA-256, SHA-384,
and SHA-512 as input digest algorithms.
 EdDSA signature supports two pure modes of Ed25519 or
Ed448.
EdDSA signature supports two pure modes of Ed25519 or
Ed448.