Use secure boot to ensure that only trusted kernels and kernel modules are loaded when
you start QRadar. The firmware ensures that the kernel and kernel modules are signed and a valid key
is stored in the system keyring before passing control to the kernel.
Before you begin
Secure Boot is only available on EFI firmware systems and is not available for BIOS systems.
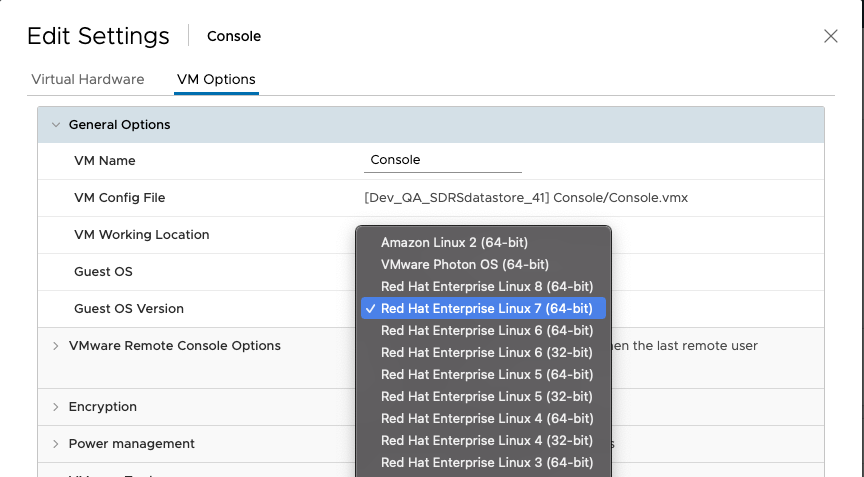
Verify you are using Red Hat Enterprise Linux 7 or later.
QRadar 7.5.0 Update Package 2 and any current EFI system that is upgraded to 7.5.0 Update Package
2 can turn on secure boot as long as the IBM public key has been imported into the system
keyring.
Access to the Machine Owner Key (MOK) importing tool called mokutil. To verify if mokutil is
installed type the command: mokutil. If mokutil is not installed and the system
uses EFI firmware you can install the RPM from the ISO or SFS. The RPM can be found on the ISO at
<mount_point>/Packages/mokutil-15-11.el7.x86_64.rpm or on the SFS at
<mount_point>/repo/mokutil-15-11.el7.x86_64.rpm
Important: Importing the public key works the same way whether secure boot is turned on
or not. These keys only load when secure boot is enabled. Once the key is imported into the system
keyring, it does not need to be imported again, unless the key has been updated (even after a
factory reinstall).
Procedure
- Import the public key by completing the following steps:
- Run the command: mokutil --import
/opt/qradar/si/certs/ibm_public_key.cer
When prompted, enter and reenter a password. This password is used during the MOK manager screens
when the system is rebooted.
- Once the public key is imported, reboot the machine from the remote console.
The MOK Manager screen opens.
- To enroll the public key complete the following steps:
- Select
and then enter the password used when you imported the public key.
- Reboot the system.
- To verify the public key was imported complete one of the following
choices:
- Run the command
keyctl list %:.system_keyring.
- If the keyutils package is not installed, you can verify using the command cat
/proc/keys.
If the key was successfully imported, the public key International Business Systems Corporation
appears in the list.
- To verify a specific key is enrolled in the system keyring use the command:
mokutil -t <path to public key>/<public key file>
For a host that is installed or patched with QRadar 7.5.0 UP2 or later, the latest IBM
public key is available at:
/opt/qradar/si/certs/ibm_public_key.cer.
For each version of QRadar
after 7.5.0 UP2 the ISO and SFS has the IBM public key in the root filesystem that is valid for the
kernel modules contained in the ISO/SFS, filename:
ibm_public_key.cer.
- Enable secure boot.
Secure boot is only available on EFI firmware systems. The option to enable or disable secure
boot is in the firmware setup screen and each firmware setup screen is different so refer to
firmware setup manual.
- To enable secure boot in VMware complete the following steps.
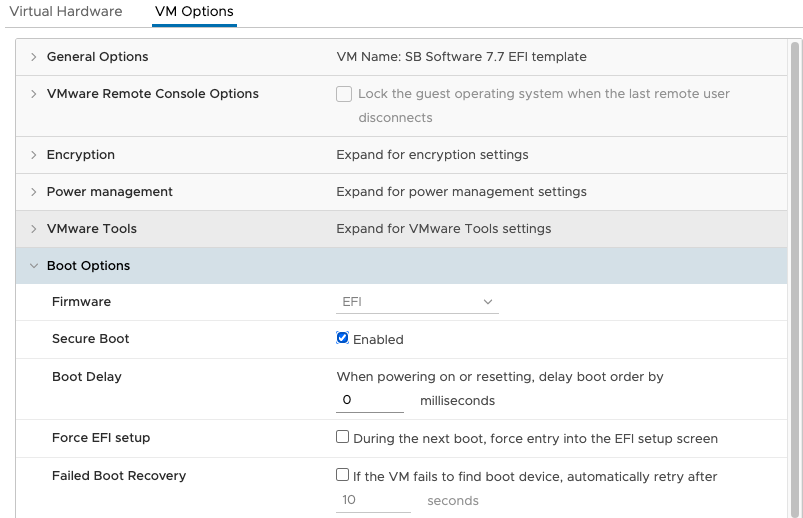
To utilize the Secure Boot feature in VMware ensure you have ESXi 6.5 to greater (Hardware
version) and Red Hat Enterprise Linux 7 or greater (OS Version).
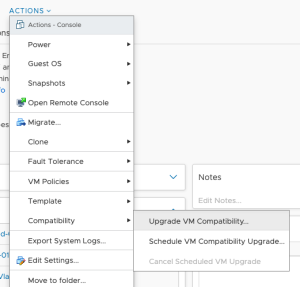
- You can upgrade the ESXi version by selecting the Upgrade VM
Compatibility option in the settings.
The machine needs to be off for this
operation.
- You can upgrade the OS version to Red Hat Enterprise Linux 7 in
.
- To enable secure boot in an VMware system, select and the select the Enabled box in the
Secure Boot field.
- To verify if Secure Boot is enabled run the command
mokutil
--sb-state.
- To verify on a system with QRadar installed you can run the command
/opt/qradar/bin/myver -sb.