IBM Security Verify Privilege Vault
Quick Start Guide
This guide describes a quick way to get started with the product.
IBM® Security Verify Privilege Vault Licensed Materials - Property of IBM. © Copyright IBM Corporation and others 2020. U.S. Government Users Restricted Rights - Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp.
IBM, the IBM logo,
and ibm.com® are trademarks or registered trademarks of
International Business Machines Corp., registered in many jurisdictions worldwide. Other product and
service names might be trademarks of IBM or other companies. A
current list of IBM trademarks is available on the Web at
Copyright
and trademark information
(www.ibm.com/legal/copytrade.shtml).
About this task
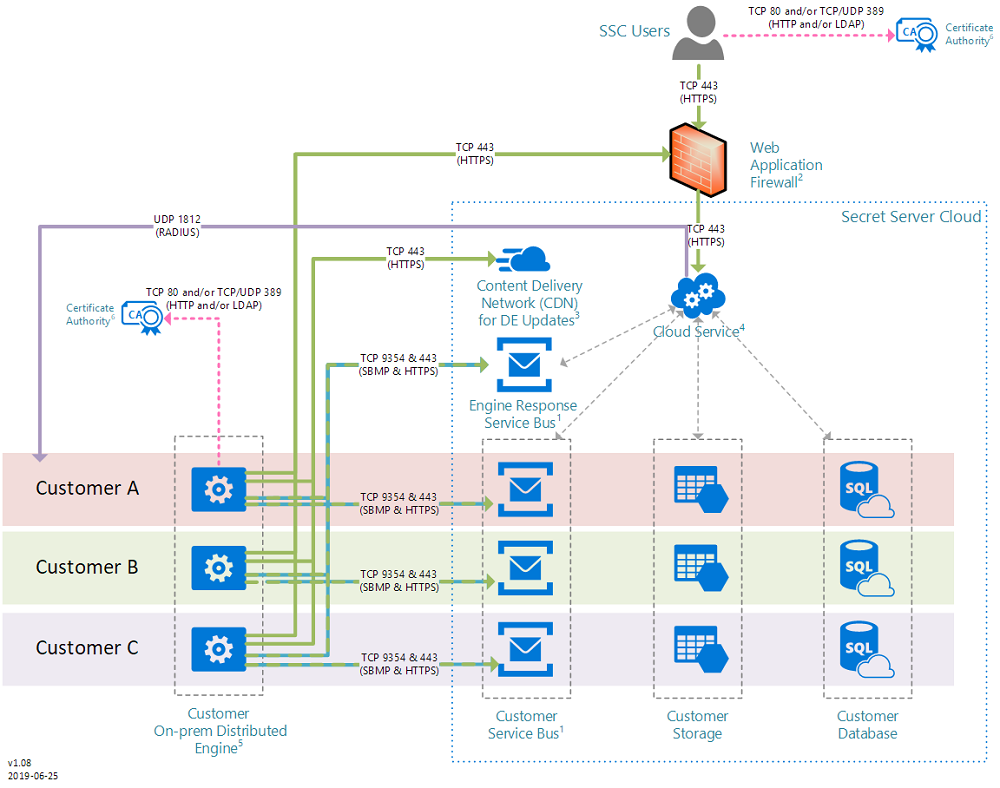
IBM Security Verify Privilege Vault helps organizations manage, automate, and track the use of shared privileged identities from a scalable, multi-tenant cloud platform.
Procedure
What to do next
Product documentation: http://www.ibm.com/support/knowledgecenter/SSWHLP_cloud.
Product support: http://www.ibm.com/support