 z/OS Communications Server: IP Diagnosis Guide
z/OS Communications Server: IP Diagnosis Guide
 z/OS Communications Server: IP Diagnosis Guide
z/OS Communications Server: IP Diagnosis Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
Main mode z/OS Communications Server: IP Diagnosis Guide GC27-3652-02 |
|
|
A Main mode exchange is composed of six messages as shown in Figure 1.
Figure 1. Main mode
exchange
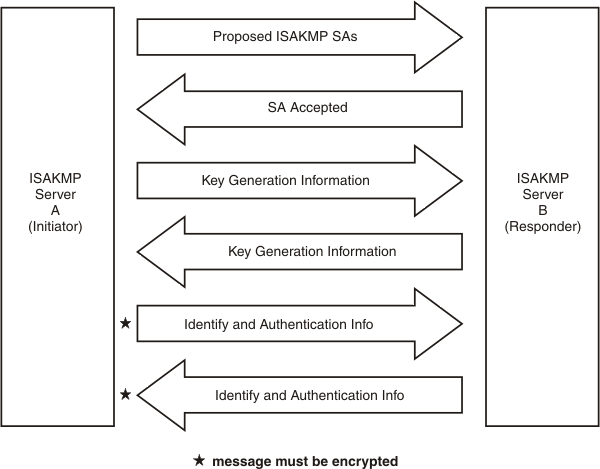 Messages 1 and 2 provide agreement on the negotiable attributes of the ISAKMP security association. These associations are used to protect phase 2 negotiations that are established by using this phase 1. The initiator sends a list of acceptable security associations to the responder in message 1. Each security association defines an acceptable combination of attributes for the ISAKMP SA that is being negotiated. The responder picks a security association that is acceptable and returns the choice to the initiator in message 2. The following attributes can be negotiated in phase1:
Messages 3 and 4 are used to exchange information specific to the generation of a shared secret key. This information includes Diffie-Hellman public values and a randomly generated value called a nonce. The initiator sends their Diffie-Hellman public value (for example, g**x mod n) and a nonce in message 3. The responder sends a Diffie-Hellman public value (for example, g**y mod n) and a nonce in message 4. With this information, both the responder and initiator can independently generate the identical keying information. The calculations that are used to generate keying information vary depending on the authentication method that was agreed upon during messages 1 and 2. The keying information that is generated by both sides
includes the following:
Messages 5 and 6 are used to exchange identity information and authentication information. The authentication information varies depending on the authentication method that was agreed upon during messages 1 and 2. For pre-shared key authentication, public key encryption authentication, and revised public key encryption authentication, the information takes the form of an encrypted hash. For signature-based authentication, this information takes the form of a signature. The initiator includes their identity and authentication information in message 5. The responder includes their identity and authentication information in message 6. Main mode provides a mechanism to exchange certificates when signature-based authentication is used. This mechanism is not shown in Figure 1, but works in the following way. In message 5 the initiating ISAKMP server can include the certificate it used to create its signature. In message 6 the responding ISAKMP server might include the certificate it used to create its signature. Inclusion of the certificate is optional unless the ISAKMP server’s peer explicitly requests that the certificate be sent. 


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |