Comparison of Transport-Layer Security and Message-Layer Security
Transport-layer security secures the network communication between the communication
partners by encrypting the data that is being transmitted over the network. In
addition, data integrity, authentication, and confidentiality can be achieved.
Transport-layer security typically uses digital signatures, PKI certificates, and
secure hash functions to prevent messages from being camouflaged
, passwords
from being hacked, and transactions from being denied.
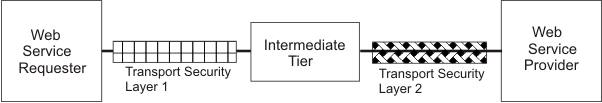
As shown in Figure 1, the connections between each hop might use
different transport-layer security methods (or even no transport
security for some connections). Transport-layer security does not span
multiple hops. This means, an intermediate hop might be able to read the message. To
achieve end-to-end security, you must therefore use message-layer security.
Using message-layer security, the message itself is secure and does not change when
sent over multiple hops.
- SSL/TLS (Secure Socket Layer/Transport Layer Security), which is denoted by HTTPS.
- VPN/IPSec (which is transparent to applications).
Message-layer security includes security-related information in the SOAP message (or more specifically, within the SOAP header).