Typical network implementation
This topic describes one possible network implementation of the Sterling™ Sensitive Data Capture Server along with the Sterling Field Sales, Sterling Call Center, Sterling Store Engagement (Legacy), and Distributed Order Management applications.
Topics listed under "Planning for secure deployment of the PA-DSS and SSDCS" present alternative network implementation strategies. You should consult this documentation if your implementation has a different mix of application components, or if you want to place your application components in more restricted network security zones as a result of your security risk assessment.
The following diagram illustrates a typical network implementation.
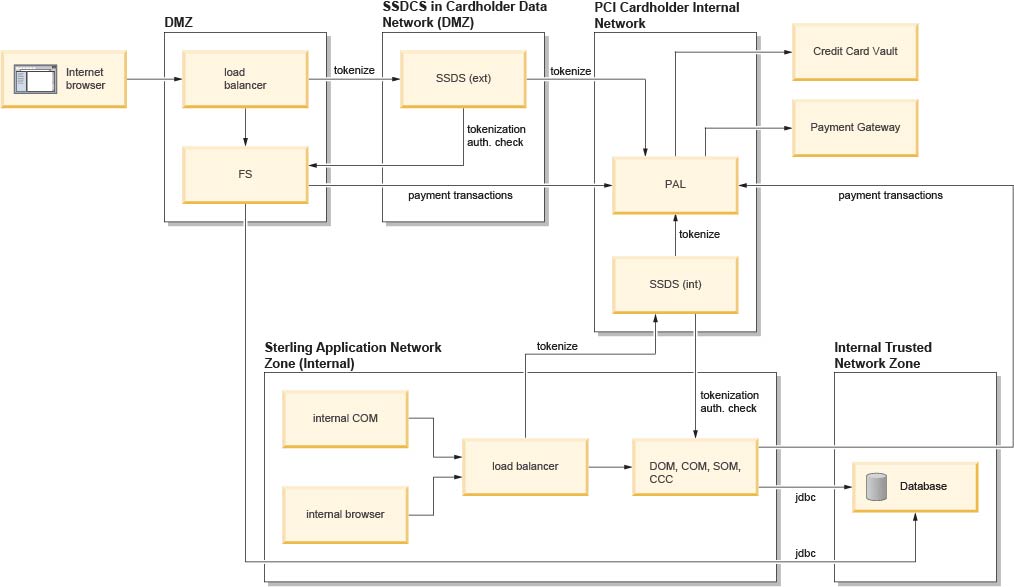
In the implementation shown in this illustration, the IBM® applications perform the following roles:
- Sterling Field Sales (FS) enables users to create quotes for complex orders.
- Distributed Order Management (DOM) provides order fulfillment functionality, such as performing payment authorization, picking fulfillment channels, and so forth.
- Sterling Call Center, Sterling Call Center,
(COM) and Sterling Store Engagement (Legacy) (SOM)
enable internal call center and store representatives to create and
manage orders. Orders (and credit card information) can be entered
through one of the following three channels:
- Internet-based users, such as sales representatives, generate complex sales quotes and then proceed to create the orders through the Sterling Field Sales (FS) applications.
- Internal Distributed Order Management (DOM) users, such as customer service representatives, enter orders through the DOM console.
- Internal DOM users, such as customer service representatives, enter orders through the web based Sterling Call Center, RCP-based Sterling Call Center (COM) and Sterling Store Engagement (Legacy) (SOM) application.
As the previous illustration shows, any of these applications that touches credit card data or PANs should reside inside the SSDCS DMZ PCI Cardholder Network. Cardholder data is kept away from the database and the Payment Abstraction Layer (PAL), which reside in the Internal Trusted Network Zone and the Internal PCI Cardholder Network, respectively. Because the PAL performs all of the tokenization and detokenization requests for payment processing, it can be monitored and securely protected, while the application sees only the order and the token, keeping the application in a PCI-compliant environment.