IAM Best Practices in AWS
With AWS Identity and Access Management (IAM), you can help ensure that your users are following security best practices. This management is important for the protection of your data and overall effectiveness of your security.
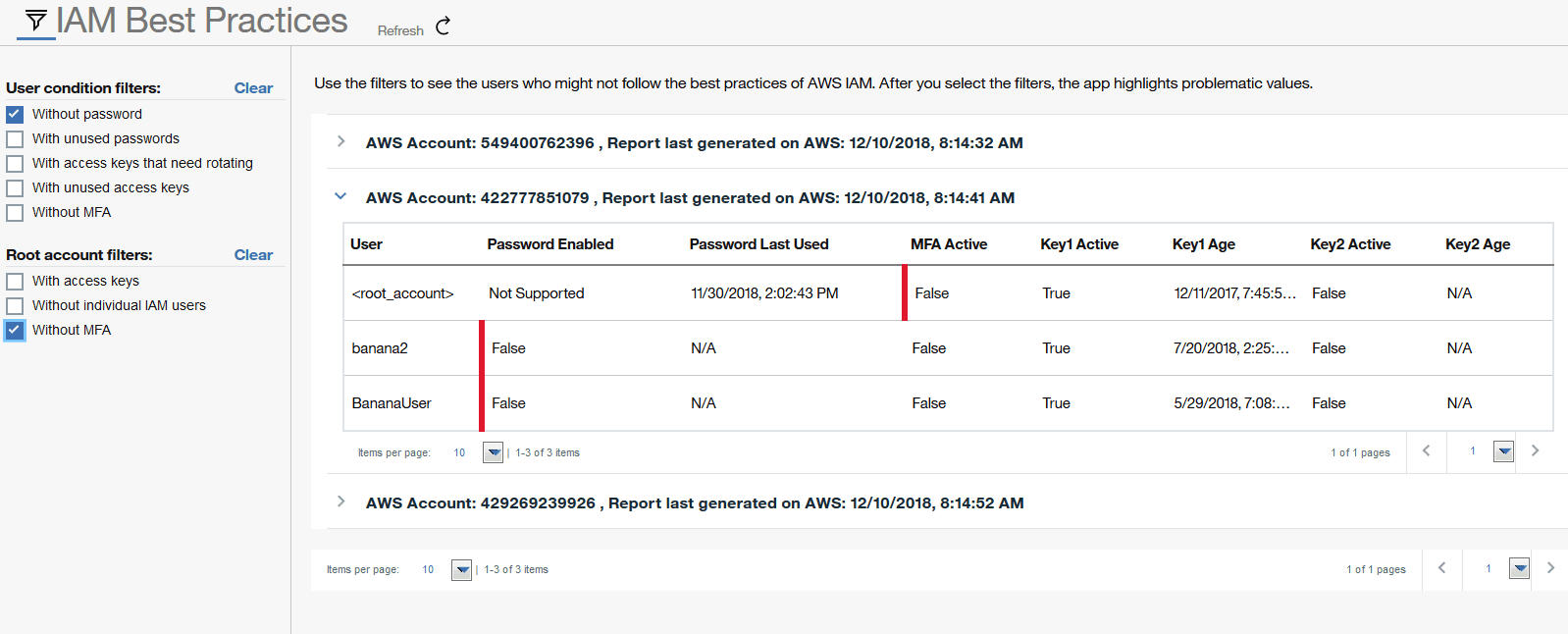
Use the IAM Best Practices page in the app to see which AWS users might be at risk of a security violation. Compliance with IAM is based on how many of the security best practices each user follows. You can also review user authentication policies. The IAM Best Practices page also shows you data retention policies and sensitive data locations.
If you request a credential report through IBM® QRadar® Cloud Visibility, IAM detects when the most recent report was generated. If the report was generated within the last 4 hours, IAM downloads the most recent report. If the report is older than 4 hours, or if you are requesting your first report request, IAM creates and downloads a new report.
Access the Filters sidebar by clicking the filter icon (![]() ) in the upper left of the page. Filter your view by user condition or by root account to
identify which users might not be following specific IAM best practices. Each time that you select
or clear filters from the sidebar, the page automatically updates with your preferred settings.
After you select the filters, the app highlights potentially problematic values.
) in the upper left of the page. Filter your view by user condition or by root account to
identify which users might not be following specific IAM best practices. Each time that you select
or clear filters from the sidebar, the page automatically updates with your preferred settings.
After you select the filters, the app highlights potentially problematic values.