Technical Blog Post
Abstract
Setting the Secure and HTTPOnly flags on the JSESSIONID cookie in WebSphere Application Server versions v7.0 and v.8.x
Body
WebSphere Application Server v8.0 and Higher:
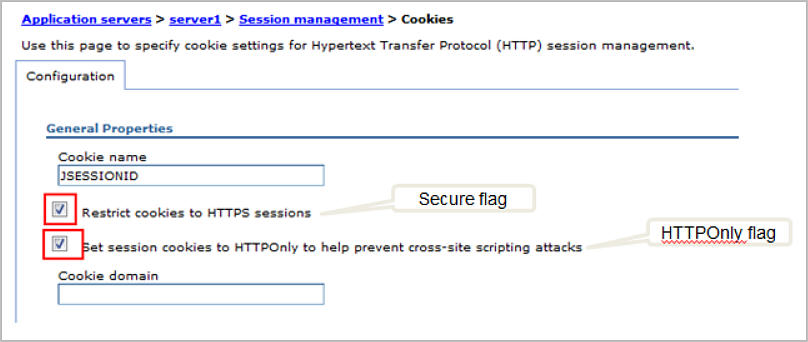
- The HTTPOnly flag on the JSESSIONID is enabled by default. Check and make sure the option "Set session cookies to HTTPOnly to help prevent cross-site scripting attacks" is selected.
- The Secure flag on the JSESSIONID is not enabled by default. To add the Secure flag to the JSESSIONID, make sure the option "Restrict cookies to HTTPS sessions" is selected.
- In the administrative console: click on Application servers > servername > Session management > Enable cookies
WebSphere Application Server v7.0:
HTTPOnly flag
- The HTTPOnly setting on the JSESSIONID cookie is a new function that was added in fixpack 7.0.0.9. You need to be at fix pack 7.0.0.9 and higher in order to configure the Webcontainer custom property "com.ibm.ws.webcontainer.HTTPOnlyCookies" for adding the HTTPOnly flag to the JSESSIONID.
- In the administrative console, click on Application servers > servername > Web Container Settings > Web container > Custom properties, click on New...
Name: com.ibm.ws.webcontainer.HTTPOnlyCookies
Value: JSESSIONID
Secure flag
- To set the Secure flag on the JSESSIONID cookie: Go to the Session management panel below and make sure the option "Restrict cookies to HTTPS sessions" is checked.
- In the administrative console: click on Application servers > servername > Session management > Enable cookies
[{"Business Unit":{"code":"BU053","label":"Cloud & Data Platform"},"Product":{"code":"","label":""},"Component":"","Platform":[{"code":"","label":""}],"Version":"","Edition":"","Line of Business":{"code":"","label":""}}]
UID
ibm11080411