Technical Blog Post
Abstract
MDM Standard Edition with external LDAP
Body
Configuring MDM Standard Edition for external LDAP
- Configurations to be done WAS Admin console of MDM.
- Configurations to be done on imm file.
Configurations to be done on WAS Admin console:
When we are using external LDAP , we have to create federated repositories on MDM WAS. The reason for this being there are default groups like mdm_admin , mdm_all_cvws etc that are created during MDM installation.
Following are the steps to configure MDM to external LDAP using WebSphere Application Server Administrative Console.
- Open up the WAS administrative console of MDM.
- Navigate to Security -> Global security
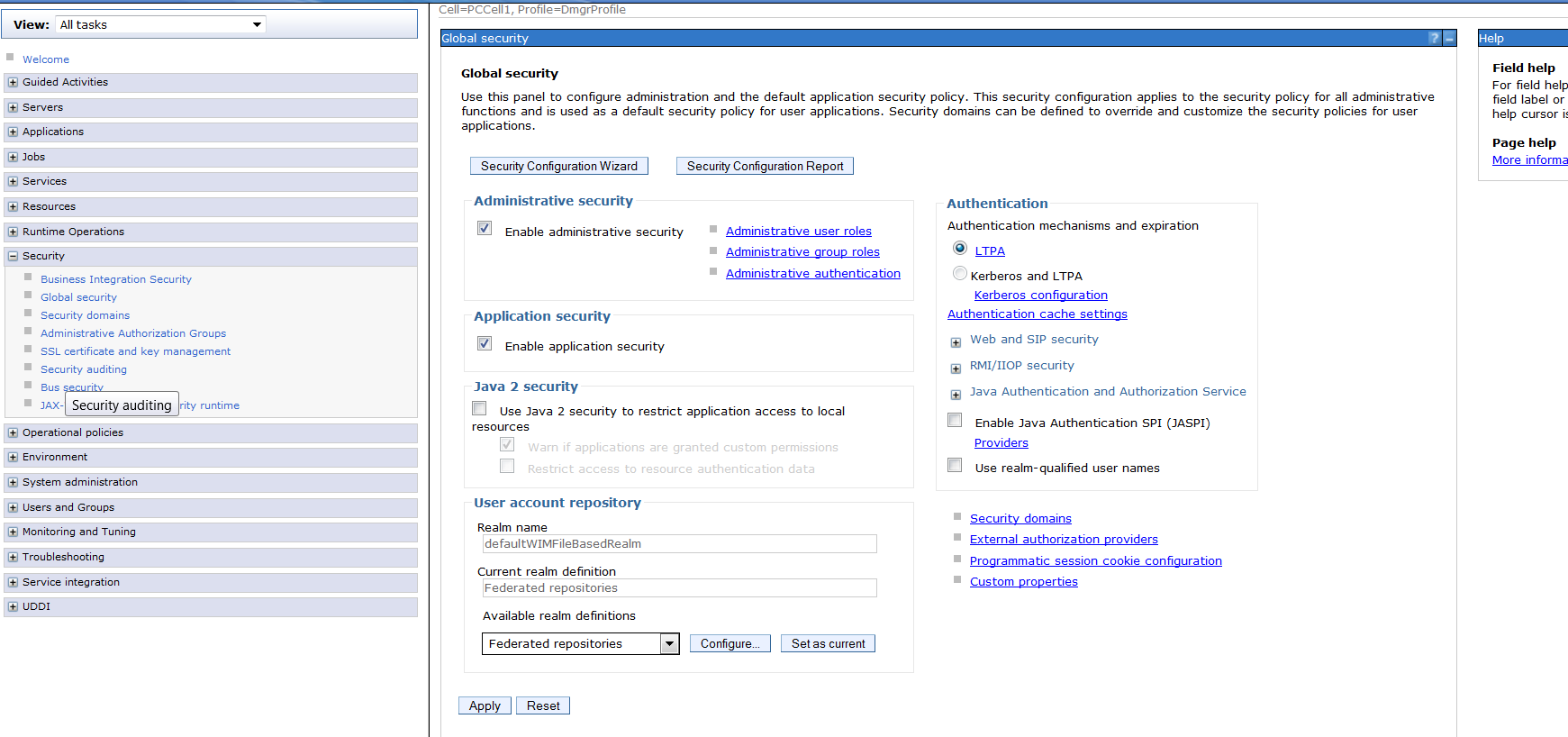
- Select “Configure” for Federated repositories and the screen would be like this.

- Click on “Manage repositories” link under section “Related Items”.
- Add a new LDAP repository. Details of the LDAP repository to be given are in the screenshot below. Need to specify the Primary host name and port number details for the LDAP which you want to use. Click on Apply once the details are given and this new LDAP repository gets added to the list of repositories for this WAS.


- Now go back to Global security -> Federated repositories. Here Click on “Add repositories(LDAP, custom,etc)…”

- It will list down the new LDAP repository we have created. Select that repository. We also need to give unique distinguished name of base entry in this repository. For the sample LDIF file we have this would be the string “cn=localhost”. All users and groups from this LDIF file are created from this base entry. It could be different based on your LDAP.

- Click on Apply and save configuration.
- Now when we go back to Federated repositories it would look like this.

- Save all the configurations.
- We will now define how to identify groups uniquely in our LDIF file. A snapshot of the way groups defined in our LDIF file here :

- We will have to now define this in our LDAP configuration in WAS. Go to the following link:

- We have to make sure Object classes property is set to an appropriate value based on your LDIF or LDAP configuration. In this example it had to be “groupOfUniqueNames”.
- We will now define how to get the relationship between users and groups uniquely in our LDIF file. Go to the following link Global security > Federated repositories > Manage repositories > LDAP1 > Group attribute definition > Member attributes If not present already create a new member attribute with “Name of member attribute” set as “uniquemember” and Object class as “groupOfUnqiueNames”. This is specifically for the LDIF configuration shown here where a user is associated with group by uniquemember/groupOfIniqueNames combination.
- Save all the configurations and restart MDM server.
Configurations to be done on IMM in MDM Workbench
- Open the imm file and in the Groups tab create a new group with the same name as the one in external LDAP. In our example it is “Group1”.
- In all the corresponding sub sections i.e., Attributes/Sources , Relationship Attributes , Composite Views , Interactions , Operations you need to give the appropriate access for this group.
- I will just take an example of giving users of this group ability to do read write access to legal name and do a memput interaction. Screenshots for the same



- Save the imm file and do deploy hub configuration.
-
Now when we use SOAP UI to do a memput for PerLegalName attribute with these users present in group the txn is successful. Any other user from the LDAP doesn’t have access and MDM fails with the same error.
Tip : To make users from an LDAP group ability to login to inspector the list of Interactions that are to be given access are APPGETINFO , DICGET , USRGETINFO. Once done this we need to save it and redeploy hub configuration.
Note : If you create a user and group on WAS instead of external LDAP , in addition to doing imm config changes you would need to add the user entry to mpi_usrhead table.
UID
ibm11142116