Technical Blog Post
Abstract
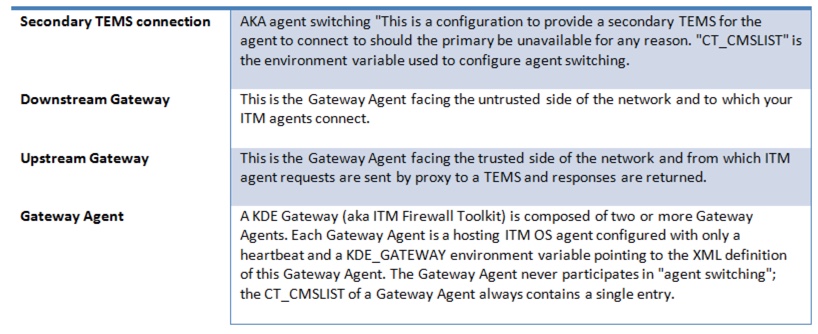
ITM Nuggets: ITM KDE firewall gateway redundancy configurations
Body
As normal, I like to blog about areas of ITM that I cover when working with you, either through PMRs or direct on customer site.
Today's series topics is all related to creating hot standby / failover of the KDE gateway.
Terminology
Before we start, here are some of the basic terminology you need to know as you read this blog....
Configurations
There are two types of configurations for the setup of the KDE_GATEWAY. The examples below demonstrate each type in turn.
Configuration #1 - Redundant configuration
Configuration #2 - Failover configuration
Configuration #1
This configuration uses no firewall redundancy, but uses a secondary TEMS connection (CT_CMSLIST) in the agents configuration file to allow multiple connections.
This configuration uses a secondary TEMS connection (CT_CMSLIST) for agents in the untrusted zone.
This configuration uses the proven logic in the agent to determine when it should switch to another TEMS (if it looses its primary connection)
Configuration #2
Starting with configuration #1 as a base model, we are adding failover capability to the gateways in the trusted zones.
There is additional capability in this set up. The configuration below will add a layer of resiliency to the Upstream Gateways and proxy TEMA clients requests to either of the two available TEMS. This is completed in the gateway XML configuration files.
Required files
You will need four XML configuration files to achieve this setup. These will need to be placed on the same machines as the nominated OS agent gateways.
 |  GATEWAY1_Upstream.xml|View Details GATEWAY1_Upstream.xml|View Details |
 |  DMZGW1_Downstream.xml|View Details DMZGW1_Downstream.xml|View Details |
 |  GATEWAY2_Upstream.xml|View Details GATEWAY2_Upstream.xml|View Details |
 |  DMZGW2_Downstream.xml|View Details DMZGW2_Downstream.xml|View Details |
Modifying the files
You will need to modify the following ****(stared) parts in the files to map them to your environments hostname or IP addresses for the various components.
***RTEMS1*** = Hostname/IP of your primary RTEMS (RTEMS 01 in above diagram)
***RTEMS2*** = Hostname/IP of your secondary RTEMS (RTEMS 02 in above diagram)
***WPA*** = Hostname/IP of your WPA
***DMZGW2*** = Hostname/IP of your DMZ Gateway 2 OS agent (Agent 4 in above diagram)
***DMZGW1*** = Hostname/IP of your DMZ Gateway 2 OS agent (Agent 3 in above diagram)
Example:
File shows:
<connection remoteport="3660">***RTEMS1***</connection>
Change ***RTEMS1*** to the IP of your RTEMS1 in this case . My RTEMS IP address is 1.1.1.1.
The line in the file now looks like this:
<connection remoteport="3660">1.1.1.1</connection>
How to enable the files
Setting the parameters
As mentioned above you need to place these files on the same machine as the OS agent you wish to use as the gateway. Once the files are on the machine you need to add the following line to the agents config file and specify the full path name and the file name.
Add this line to each of the agents configuration files that are being used as the gateway::
KDE_GATEWAY=Full path/<name>.xml
Location of the configuration files
•Windows OS agent located in the ITMHOME/tmaitm6/KNTENV file.
•UNIX OS agent in the ITMHOME/config/ux.ini files.
•Linux OS agent in the ITMHOME/config/lz.ini files.
Once the parameter has been added to the configuration file, The agent will need to be restarted for the configuration in the XML files to take effect.
Other information
Here is some information on what some of the parameters in the files mean
Roles that can be defined in the KDE_GATEWAY xml file and what they mean (this will help you read the files and set any non default ports).
§3 different functions can be defined at a Gateway:
–role="connect“: TEMA opens the defined Port and tries a first time to connect to the defined server port –Counterpart of LISTEN
–role="listen“: TEMA starts to listen on de defined Port for incoming connections from the defined server/port –Counterpart of CONNECT
–role=“proxy“: TEMA can start 2 different kinds of Proxy:
•ClientProxy: runs in the Secure Zone and connects the incoming Gateway Connections to the TEMS or WPA
•ServerProxy: runs in any of the Less Secure Zones and starts listening on the TEMS (1918) and/or WPA (63358) port
Further Reading
The best source of information id the install and setup guide in the "appendices C" section for the version of the product you are using
Let's connect!
To follow my social updates on IBM software, please feel free to connect with me by clicking on the images below:
 |
Find all my other blogs here:
LINK
Subscribe and follow us for all the latest information directly on your social feeds:
|
|
 |

|
| Check out all our other posts and updates: | |
| Academy Blogs: | http |
| Academy Videos: | http |
| Academy Google+: | http |
| Academy Twitter : | http |
UID
ibm11082775