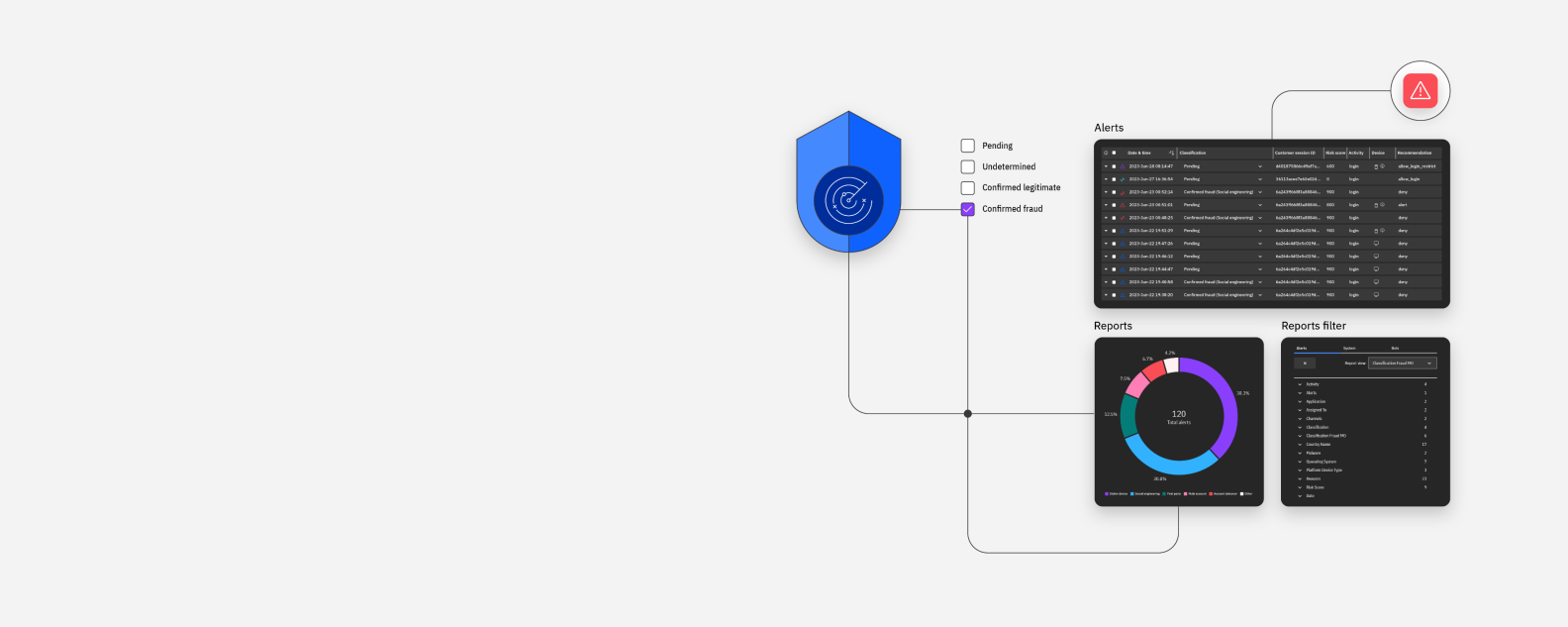
IBM Security® Trusteer® Mobile protects native iOS and Android applications through device risk factor analysis, behavior anomaly detection, and persistent mobile device IDs. IBM Security Trusteer Mobile is fully integrated into the Pinpoint cloud risk platform.
IBM Security Trusteer Mobile helps detect device and session risks in real time, helping maintain the integrity of the application in which it has been embedded by using advanced analytics. Trusteer Mobile assesses the device to determine if it has been compromised by malicious actors such as malware, remote access Trojans (RAT) and SMS stealing apps or through jailbreaking and rooting, overlay attacks and more. It uses advanced technologies to continuously process additional cross-channel indicators such as behavioral anomalies, navigation discrepancies and phishing compromise evidence.
In 2023, organizations saw a 71% spike in cyberattacks caused by exploiting identities. Check out the new report to learn how to best safeguard identities.
KuppingerCole Leadership Compass - See why Trusteer was named an overall leader in the latest Leadership Compass: Fraud Reduction Intelligence Platforms (FRIP).
Detect and assess the risks associated with the mobile device, account and connection prior to accessing the mobile app.
Generate a persistent mobile device ID, based on hardware and software attributes, that is resilient to application reinstallation.
Correlate online and mobile banking risk data for mobile risk detection through Pinpoint Cloud scalable machine learning and AI capabilities.
Automatic updated risk assessment detects mobile threats.
Trusteer Mobile SDK contains a root/jailbreak detection capability that helps determine whether a modified version of the operating system is installed.
Trusteer Mobile SDK enables certificate pinning, also known as SSL Pinning or augmented certificate authority security, to help detect and block such attacks.
Trusteer Mobile provides a set of APIs that natively integrate into your mobile banking app to provide real-time risk analysis and detection of overlay attacks.
Trusteer Mobile detects transactions originating from virtual machines or emulators and provides actionable recommendations on whether to allow, restrict or deny user or device access.
By generating a persistent mobile device ID (based on hardware and software attributes) that is resilient to application reinstallation, Trusteer Mobile SDK helps detect new, spoofed (proxy) and known criminal devices.
The Trusteer native user behaviour biometric profiling capability uses device telemetry and built-in accelerators and motion sensors for securing user identities.
Trusteer Mobile detects installed malicious mobile remote access tools on devices as well as real-time remote access sessions.
The global consortium provides mobile intelligence including carrier intelligence and known fraudsters intelligence.
Trusteer Mobile detects on-device risk such as malware, re-packaged applications or rooted/jailbroken devices.
Use cases
Through cloud-based intelligence, backed by AI and patented machine learning, Trusteer provides a holistic approach to identifying new and existing customers, without negatively impacting user experience.
Forrester showed a 3-year 156% ROI on fraud detection with IBM Security Trusteer.
IBM Security Trusteer researchers discovered a new trend in financial mobile malware that targets Android and is replacing the classic overlay approach.
Seamlessly assess the risk of new and guest digital identities.
Outsmart account takeover attempts with seamless digital fraud detection.
Detect and remediate malware and identify phishing attacks within minutes.
Frequently asked questions
Get answers to the most commonly asked questions about this product.
Companies often have to make tradeoffs between security and customer experience in today's threat landscape. Digital identity trust technology lets companies measure both risk and trust to keep the customer’s digital journey secure while still offering a better digital experience.
Trusteer Mobile SDK creates a strong device ID that helps differentiate a known device from others. By applying extensive risk protection capabilities, behavioral analytics and contextual vectors, Trusteer Mobile SDK helps determine whether a device has been compromised and verifies that the user is the trusted user.
A new device can usher in threat through poor hygiene or questionable activity. Trusteer Mobile SDK uses a global consortium database and threat intelligence platform with AI and machine learning to help identify bad devices and malicious patterns.
Trusteer Mobile SDK can help identify fraud early during digital account creation or one-time guest engagement from a mobile device. It correlates provided identifiers and context with known fraud and assesses risk by scanning for indicators such as recent mobile carrier changes and suspicious timing.
In general, software as a service (SaaS) solutions offer the ability to deploy quickly and easily. The SaaS deployment also allows Trusteer Mobile SDK to employ agile, ongoing threat protection that uses AI and analytics to identify new threats and patterns.
Trusteer Mobile SDK combines with IBM Security Trusteer Pinpoint Detect to offer multi-factor omnichannel risk assessment by understanding user activity. The solution collects a wide range of attributes and performs multi-layered assessments of network, device, environment and behavioral patterns.
Trusteer Mobile SDK combines with IBM Security Trusteer Pinpoint Assure to help identify fraudsters and establish digital trust with customers by using cloud-based threat intelligence and global visibility during account creation and guest-user transactions.