Enabling groups of users
After authenticating users in your application server, you manage users and groups from the Administration tab of the Business console or using an Ant task.
Decision Center uses groups for fine-grained security access to the different branches (decision services, releases, and activities) and permissions on the different types of rule artifacts (see Decision Center security). To make use of this security and permissions feature, you must create groups in the Decision Center database, and assign all users to one or more of these groups.
- Decision Center Groups
- You create in Decision Center as many groups as you need to organize your users functionally. When you create or import a group, you must map the group to a role, and then place users in the groups. It is not possible to map a user to a role directly.
- UI Roles
- A role determines what portions of the Decision
Center UI
are available to a user. Decision
Center has
the following predefined roles:
Role Description Business console Enterprise console Standard user (rtsUser) The standard Decision Center user. Basic use. Basic use. Configuration manager (rtsConfigManager) Has all the rights of the standard user, plus additional rights in the Business and Enterprise consoles. Create and edit deployment configurations. Manage RuleApps, servers, ruleset extractors, and other features described in Groups. Administrator (rtsAdministrator) Has all the rights of the standard and configuration manager users, plus additional rights in the Business and Enterprise consoles. - Access the Administration tab to enable security and manage users.
- Take on the role of any governance framework participant.
- Set security.
- Administer the Decision Center database.
- Release locks.
Installer (rtsInstaller) Only required for the initial installation of Decision Center. - Access the Installations Settings Wizard.
- For the initial configuration of Decision Center, choose a group in your LDAP or create a group for administrators and installers, for example AdminGroup and InstallGroup. Map these groups to the roles rtsAdministrator and rtsInstaller, and place all administrator users as members of both these groups.
- After the initial configuration, create or import new groups, map these groups to the rtsUser role, and place users in the new groups. When you import groups from an LDAP, an equivalent Decision Center group is created.
The following image shows how roles, groups, and users interact:
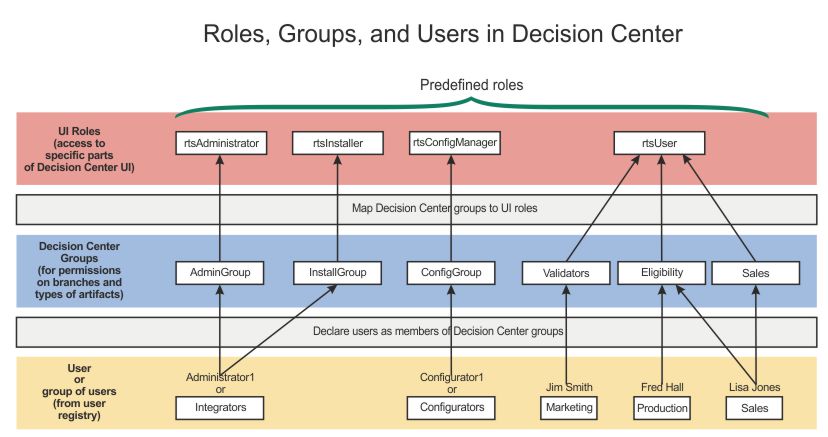
- The bottom of the diagram shows that you declare, in the Decision Center database, the users present in your user registry.
- The middle of the diagram shows that all users must be members of one or more Decision Center groups. You create these Decision Center groups yourself, either manually or by importing them from an LDAP. You name these groups according to their functional relationship in Decision Center, or according to how they are grouped in the registry. If you are using an LDAP, you can connect to the LDAP from Decision Center to facilitate importing of groups and users.
- The top part of the diagram shows how you map each Decision Center group to one of the predefined roles. You can also create new roles but this requires an equivalent customization of the Decision Center UI.
Permission profiles
In Decision Center, security defines which groups have access to the different branches of a decision service (see Decision Center security).
With security implemented, you must specify, for each Decision Center group that can access the branch, what permissions they have to view, create, update, and delete which types of artifacts.
- None
- Groups assigned this permission profile have access to the branch, but cannot see its content.
- Read Only
- Groups assigned this permission profile can view the contents of the branch, but cannot create, update, or delete content.
- Full Authoring
- Groups assigned this permission profile can view, create, update, or delete all content in the branch.
- Custom
- Assigning this permission profile requires you to use the Enterprise console to manually create a permissions table for that group (see Permissions.)
The permission profile that you assign in the Business console is automatically switched to Custom if you make changes to the permission table in the Enterprise console.