Configuring SSL and TLS by using CA-signed certificates
Configure Secure Sockets Layer (SSL) and Transport Layer Security (TLS) on the Tivoli® Storage Manager server, backup-archive client, and storage agent to ensure that data is encrypted during communication. You can use a signed certificate from a third-party Certificate Authority (CA) to verify an SSL communication request between the server, client, and storage agent.
Before you begin
To use the SSL to secure communications between the Operations Center and the hub server, see Configuring for SSL communication between the Operations Center and the hub server.
The following figure shows the step number to complete the task.
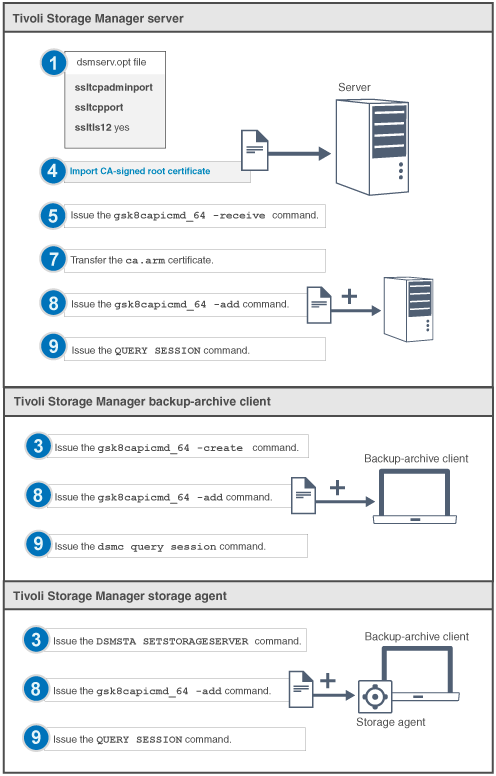
- Enter commands on one line. In the following steps, commands are displayed here on multiple lines to make it easier to read. Ensure that you enter a space after each command.
- If your client operating system is 32-bit, replace the gsk8capicmd_64 command with gsk8capicmd in all GSKit commands.
- Before you set up the server certificate on the client, follow these steps:
- Open a command window and change the directory to your Tivoli Storage Manager client directory, for example: cd "C:\Program Files\Tivoli\TSM\baclient"
- Append the GSKit binary path and library path to the PATH
environment variable, for example:
where x: is the system drive where Tivoli Storage Manager is installed.set PATH=x:\Program Files\Common Files\Tivoli\tsm\api64\gsk8\bin\; x:\Program Files\Common Files\Tivoli\tsm\api64\gsk8\lib64;%PATH%
About this task
Each Tivoli Storage Manager server, client, or storage agent that enables SSL must use a trusted self-signed certificate or obtain a unique certificate that is signed by a CA. You can use your own certificates or purchase certificates from a CA. Either certificate can be installed and added to the key database on the Tivoli Storage Manager server, client, or storage agent. If you use a root certificate from a CA, you must install it on each key database for the client, server, and storage agent that initiates SSL communication. The certificate is verified by the SSL client or server that requests or initiates the SSL communication.
You can restrict SSL communication to use TLS 1.2 and prevent the use of previous TLS protocol levels, which are less secure. To use TLS 1.2, in addition to configuring the source server to use TLS 1.2, you must also configure the target server or storage agent to use TLS 1.2.