Specifying CipherSpecs
Specify a CipherSpec by using the SSLCIPH parameter in either the DEFINE CHANNEL MQSC command or the ALTER CHANNEL MQSC command.
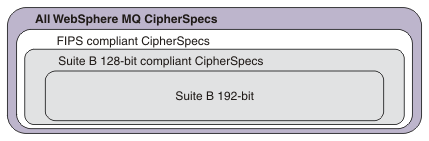
Some of the CipherSpecs that you can use with IBM® WebSphere® MQ are FIPS compliant. Others, such as NULL_MD5, are not. Similarly, some of the
FIPS compliant CipherSpecs are also Suite B compliant although others, are not. All Suite B
compliant CipherSpecs are also FIPS compliant. All Suite B compliant CipherSpecs fall into two
groups: 128 bit (for example, ECDHE_ECDSA_AES_128_GCM_SHA256) and 192 bit (for
example, ECDHE_ECDSA_AES_256_GCM_SHA384),
The following diagram illustrates the relationship between these subsets:
Cipher specifications that you can use with IBM WebSphere MQ SSL and TLS support are listed in the following table. When you request a personal certificate, you specify a key size for the public and private key pair. The key size that is used during the SSL handshake is the size stored in the certificate unless it is determined by the CipherSpec, as noted in the table.
| CipherSpec name | Protocol used | MAC algorithm | Encryption algorithm | Encryption bits | FIPS1 | Suite B 128 bit | Suite B 192 bit |
|---|---|---|---|---|---|---|---|
NULL_MD5 a |
SSL 3.0 | MD5 | None | 0 | No | No | No |
NULL_SHA a |
SSL 3.0 | SHA-1 | None | 0 | No | No | No |
RC4_MD5_EXPORT 2 a |
SSL 3.0 | MD5 | RC4 | 40 | No | No | No |
RC4_MD5_US a |
SSL 3.0 | MD5 | RC4 | 128 | No | No | No |
RC4_SHA_US a |
SSL 3.0 | SHA-1 | RC4 | 128 | No | No | No |
RC2_MD5_EXPORT 2 a |
SSL 3.0 | MD5 | RC2 | 40 | No | No | No |
DES_SHA_EXPORT 2 a |
SSL 3.0 | SHA-1 | DES | 56 | No | No | No |
RC4_56_SHA_EXPORT1024 3 b |
SSL 3.0 | SHA-1 | RC4 | 56 | No | No | No |
DES_SHA_EXPORT1024 3 b |
SSL 3.0 | SHA-1 | DES | 56 | No | No | No |
TLS_RSA_WITH_AES_128_CBC_SHA a |
TLS 1.0 | SHA-1 | AES | 128 | Yes | No | No |
TLS_RSA_WITH_AES_256_CBC_SHA 4 a |
TLS 1.0 | SHA-1 | AES | 256 | Yes | No | No |
TLS_RSA_WITH_DES_CBC_SHA a |
TLS 1.0 | SHA-1 | DES | 56 | No5 | No | No |
FIPS_WITH_DES_CBC_SHA b |
SSL 3.0 | SHA-1 | DES | 56 | No6 | No | No |
TLS_RSA_WITH_AES_128_GCM_SHA256 b |
TLS 1.2 | AEAD AES-128 GCM | AES | 128 | Yes | No | No |
TLS_RSA_WITH_AES_256_GCM_SHA384 b |
TLS 1.2 | AEAD AES-256 GCM | AES | 256 | Yes | No | No |
TLS_RSA_WITH_AES_128_CBC_SHA256 b |
TLS 1.2 | SHA-256 | AES | 128 | Yes | No | No |
TLS_RSA_WITH_AES_256_CBC_SHA256 b |
TLS 1.2 | SHA-256 | AES | 256 | Yes | No | No |
ECDHE_ECDSA_RC4_128_SHA256 b |
TLS 1.2 | SHA-1 | RC4 | 128 | No | No | No |
ECDHE_RSA_RC4_128_SHA256 b |
TLS 1.2 | SHA_1 | RC4 | 128 | No | No | No |
ECDHE_ECDSA_AES_128_CBC_SHA256 b |
TLS 1.2 | SHA-256 | AES | 128 | Yes | No | No |
ECDHE_ECDSA_AES_256_CBC_SHA384 b |
TLS 1.2 | SHA-384 | AES | 256 | Yes | No | No |
ECDHE_RSA_AES_128_CBC_SHA256 b |
TLS 1.2 | SHA-256 | AES | 128 | Yes | No | No |
ECDHE_RSA_AES_256_CBC_SHA384 b |
TLS 1.2 | SHA-384 | AES | 256 | Yes | No | No |
ECDHE_ECDSA_AES_128_GCM_SHA256 b |
TLS 1.2 | AEAD AES-128 GCM | AES | 128 | Yes | Yes | No |
ECDHE_ECDSA_AES_256_GCM_SHA384 b |
TLS 1.2 | AEAD AES-256 GCM | AES | 256 | Yes | No | Yes |
ECDHE_RSA_AES_128_GCM_SHA256 b |
TLS 1.2 | AEAD AES-128 GCM | AES | 128 | Yes | No | No |
ECDHE_RSA_AES_256_GCM_SHA384 b |
TLS 1.2 | AEAD AES-256 GCM | AES | 256 | Yes | No | No |
TLS_RSA_WITH_NULL_SHA256 b |
TLS 1.2 | SHA-256 | None | 0 | No | No | No |
ECDHE_RSA_NULL_SHA256 b |
TLS 1.2 | SHA-1 | None | 0 | No | No | No |
ECDHE_ECDSA_NULL_SHA256 b |
TLS 1.2 | SHA-1 | None | 0 | No | No | No |
TLS_RSA_WITH_NULL_NULL b |
TLS 1.2 | None | None | 0 | No | No | No |
TLS_RSA_WITH_RC4_128_SHA256 b |
TLS 1.2 | SHA-1 | RC4 | 128 | No | No | No |
| Notes:
Platform support:
|
|||||||