Using self-signed certificates for mutual authentication of two queue managers
Follow these sample instructions to implement mutual authentication between two queue managers, using self-signed SSL or TLS certificates.
About this task
Scenario:
- You have two queue managers, QM1 and QM2, which need to communicate securely. You require mutual authentication to be carried out between QM1 and QM2.
- You have decided to test your secure communication using self-signed certificates.
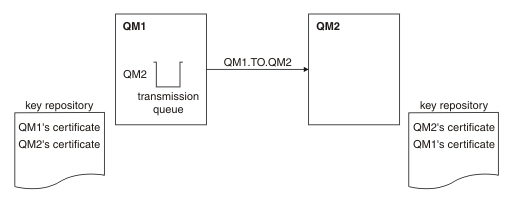
In Figure 1, the key repository for QM1 contains the certificate for QM1 and the public certificate from QM2. The key repository for QM2 contains the certificate for QM2 and the public certificate from QM1.
Procedure
Results
What to do next
Check that the task has been completed successfully by using DISPLAY commands. If the task was successful, the resulting output is similar to that shown in the following examples.
DISPLAY CHS(QM1.TO.QM2) SSLPEER SSLCERTI
DISPLAY CHSTATUS(QM1.TO.QM2) SSLPEER SSLCERTI
4 : DISPLAY CHSTATUS(QM1.TO.QM2) SSLPEER SSLCERTI
AMQ8417: Display Channel Status details.
CHANNEL(QM1.TO.QM2) CHLTYPE(SDR)
CONNAME(9.20.25.40) CURRENT
RQMNAME(QM2)
SSLCERTI("CN=QM2,OU=WebSphere MQ Development,O=IBM,ST=Hampshire,C=UK")
SSLPEER("SERIALNUMBER=4C:D0:49:D5:02:5E:02,CN=QM2,OU=WebSphere MQ Development,O=IBM,ST=Hampshire,C=UK")
STATUS(RUNNING) SUBSTATE(MQGET)
XMITQ(QM2)
DISPLAY CHS(QM1.TO.QM2) SSLPEER SSLCERTI
DISPLAY CHSTATUS(QM1.TO.QM2) SSLPEER SSLCERTI
5 : DISPLAY CHSTATUS(QM1.TO.QM2) SSLPEER SSLCERTI
AMQ8417: Display Channel Status details.
CHANNEL(QM2.TO.QM1) CHLTYPE(RCVR)
CONNAME(9.20.35.92) CURRENT
RQMNAME(QM1)
SSLCERTI("CN=QM1,OU=WebSphere MQ Development,O=IBM,ST=Hampshire,C=UK")
SSLPEER("SERIALNUMBER=4C:D0:49:D5:02:5F:38,CN=QM1,OU=WebSphere MQ Development,O=IBM,ST=Hampshire,C=UK")
STATUS(RUNNING) SUBSTATE(RECEIVE)
XMITQ( )
In each case, the value of SSLPEER must match that of the DN in the partner certificate that was created in Step 2. The issuers name matches the peer name because the certificate is self-signed .
SSLPEER is optional. If it is specified, its value must be set so that the DN in the partner certificate (created in step 2) is allowed. For more information about the use of SSLPEER, see WebSphere® MQ rules for SSLPEER values .