Troubleshooting
Problem
Offenses are being created based on IP addresses in a superflow that are not contained in a reference set which is specified in the rule test.
Cause
Suppose a new custom rule is created that raises an offense whenever an IP in a created reference set is detected in a flow. This reference set would have been added to the rule test while making the rule. The created offense will be indexed by the Source IP.
However, users might notice that the rule is triggering on and creating offenses based on IPs which are not found in the reference set that was specified in the rule test. When inspecting the superflow which triggered the offense, the superflow will contain one or more IP addresses from the reference set in the rule set.
However, the IP address in the reference set is not the one being used to index the Offense, instead a random IP is pulled from the superflow IP list and an offense is created from that.
When the rule test passes, the superflow is sent to the offense model to create the offense. The Offense Model is unaware of which tests were used by the BB/Rules, or which IPs are relevant from Superflow perspective.
For flows that are a part of superflows, the IP's in those flows (source of destination), or a port-based superflow, are not broken out to generate offenses, one on each unique IP in the list of addresses.
However, users might notice that the rule is triggering on and creating offenses based on IPs which are not found in the reference set that was specified in the rule test. When inspecting the superflow which triggered the offense, the superflow will contain one or more IP addresses from the reference set in the rule set.
However, the IP address in the reference set is not the one being used to index the Offense, instead a random IP is pulled from the superflow IP list and an offense is created from that.
When the rule test passes, the superflow is sent to the offense model to create the offense. The Offense Model is unaware of which tests were used by the BB/Rules, or which IPs are relevant from Superflow perspective.
For flows that are a part of superflows, the IP's in those flows (source of destination), or a port-based superflow, are not broken out to generate offenses, one on each unique IP in the list of addresses.
Environment
QRadar 7.2.0 and later.
Diagnosing The Problem
Open an offense which was triggered on a rule set. This must be an offense that was triggered on a superflow. Navigate to the source IP that fired the offense and compare the IP address to the list defined in the reference set of the rule test. The IP address may not be listed in the reference set. However an offense was created based on that rule.
Resolving The Problem
There are two workarounds that users can implement:
- Create a test within your Rule to exclude the rule from firing on a specific type of Superflow. For example, in this case we use the 'and NOT' condition to exclude type A Superflows from the rule.
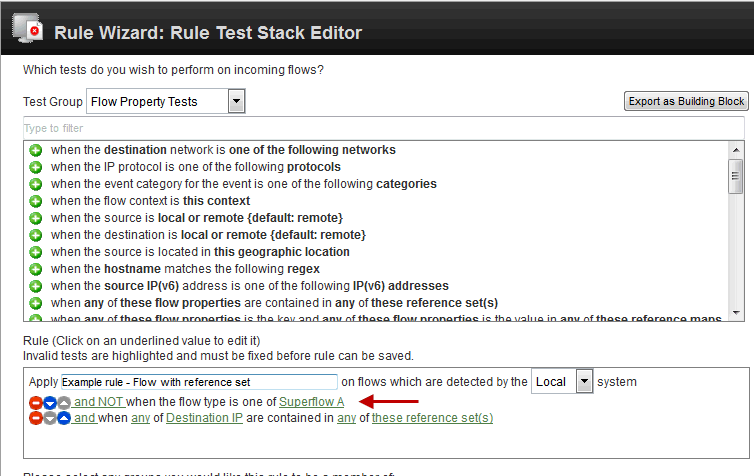
Figure 1: Creating an 'and NOT' rule test to exclude superflows.
- Edit the QFlow advanced configuration in the Deployment Editor to increase the threshold for superflow creation. If the administrator increases the threshold of superflow by a factor of 10 times, then this will reduce or eliminate the number of superflows created in the entire environment.

Figure 2: Administrators can adjust the threshold for superflow creation.
[{"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000Cbr3AAC","label":"QRadar->Rules->CRE"}],"ARM Case Number":"","Platform":[{"code":"PF016","label":"Linux"}],"Version":"7.2","Edition":"","Line of Business":{"code":"LOB24","label":"Security Software"}}]
Historical Number
46616;L6Q;000
Was this topic helpful?
Document Information
Modified date:
03 April 2020
UID
swg21968800