Troubleshooting
Problem
Customer needs to allow users to logon to Controller, using Windows usernames that belong to completely separate authentication sources.
How can they configure Controller to use more than one namespace?
Symptom
Example:
Customer wishes for its users to logon to Controller using their Windows username/password. They logon to their application server, and launch Cognos Configuration. They create a new 'Active Directory' namespace called 'DOMAIN1' and configure the rest of the Controller application server as appropriate. This works OK.
However, some of their Controller end users do not belong to DOMAIN1. Instead, their Windows usernames belong to a separate forest called DOMAIN2.
Cause
This technique is typically necessary when users belong to Active Directory (AD) domains which are entirely separate.
- In other words, they are not part of the same AD Forest.
Because the two AD domains are entirely separate, there are no cross-domain trusts (or forest links)
- Therefore you cannot use a single Cognos Analytics (CA) namespace (using techniques such as 'ChaseReferrals' or 'MultiDomainTrees' to sllow CA to search the entire forest for the users from different domains).
Resolving The Problem
Imagine a scenario where you wanted all of the following users to be able to logon to Controller:
| Active Directory username | Controller Username | Role |
| DOMAIN1\john_smith | ADM | Administrator (can create/edit users from Domain1) |
| DOMAIN1\mmouse | USER1 | standard user in domain1 |
| DOMAIN1\dduck | USER2 | standard user in domain1 |
| DOMAIN2\fred_bloggs | ADM2 | Administrator (can create/edit users from Domain2) |
| DOMAIN2\aperson | USER3 | standard user in domain2 |
| DOMAIN2\brogers | USER4 | standard user in domain2 |
To achieve the above:
1. On your report server (Cognos Analytics) launch Cognos Configuration
2. Create a namespace (for example called 'DOMAIN1' and 'DOMAIN2') for each of your separate AD domains
3. Launch CA administration portal (website), and open the role: Controller Administrators
- Add the AD users 'DOMAIN1\john_smith' and 'DOMAIN2\fred_bloggs' into that role
4. Launch CA administration portal (website), and open the role: Controller Users
- Add the role 'Controller Administrators' to be a member
- Add the following AD users:
- DOMAIN1\mmouse
- DOMAIN1\dduck
- DOMAIN2\aperson
- DOMAIN2\brogers
5.Launch Controller client, and logon as the existing Domain1 superuser, for example: DOMAIN1\john_smith
- In other words, you have now authenticated to Controller using the native user 'ADM'
6. Click "Maintain - Rights - Users"
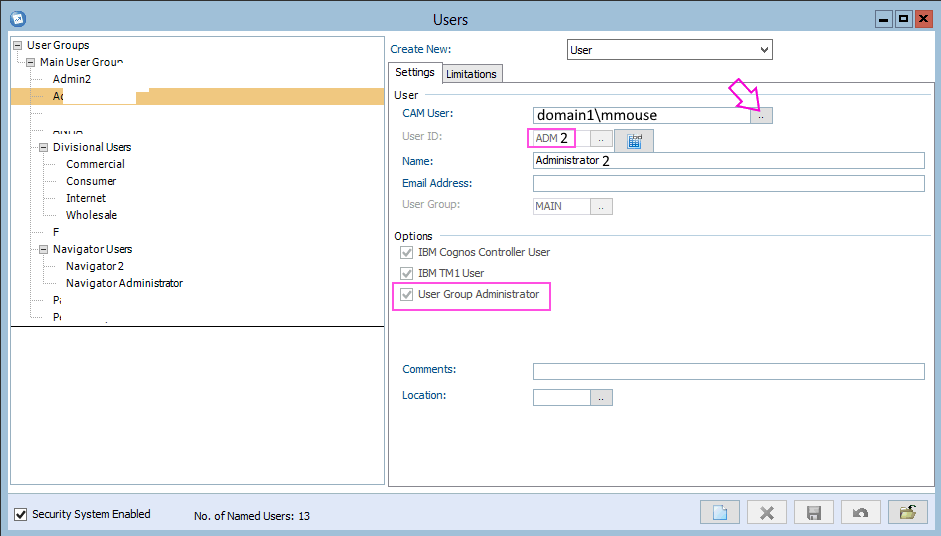
7. Create a new Controller user
- User ID = ADM2
- Click the 'CAM User' button and choose any of the DOMAIN1 users, for example: DOMAIN1\mmouse
- NOTE: At this point in time, you will only be able to select (inside the Controller GUI) users from DOMAIN1 when you create this user.
- Do not worry about this! This user will only temporarily be used ... it will be changed later!
- Make sure "User Group Administrator" is ticked:
8. Save changes, and exit Controller
9. Launch your database management tool (for example SQL Management Studio)
- These instructions assume using MS SQL. For other database systems, modify the instructions as appropriate
10. Locate the Controller database (for example "ControllerLIVE")
- As a precaution, you can optionally perform a complete backup of the database (before proceeding)
11. Expand the database, and open the section "tables"
12. Right-click on the table "XCAMUSER" and choose "Edit Top 200 Rows"


13. Locate the row for the new user (for example called "ADM2") that was created earlier.
14. Manually modify the table so that:
- the entry for the column "CAMUSER" points to the new namspace (for example DOMAIN2\Fred_Bloggs)
- the entry for the column "CAMID" is the correct value for that same user (for example something similar to: CAMID("Domain2:u:authid=xxxxxxx").
- TIP: To find the CAMID, see separate IBM Technote #1371371.
For example:


15. Close the SQL table, and save changes
16. Launch Controller. Logon (to the domain2 Cognos namespace) using the NEW user (for example DOMAIN2\Fred_Blogs)
17. Click "Maintain - Rights - Users".
- You will notice that you can now successfully add/modify users for this new domain namespace (for example DOMAIN2).
- However, you will not be able to administer users from DOMAIN1.
18. Create new Controller users in Domain2
- for example create Controller user 'User3' and then click 'CAM User' button to map it to: DOMAIN2\aperson
19. Repeat for all users in Domain2
20. Close Controller client.
21. Launch Controller. Logon (to the domain1 Cognos namespace) using the original superuser (for example DOMAIN1\john_smith)
22. Click "Maintain - Rights - Users".
22. Click "Maintain - Rights - Users".
- You will notice that you can now only add/modify users for the old domain namespace (for example DOMAIN1).
23. Create new Controller users in Domain1
- for example create Controller user 'User1' and then click 'CAM User' button to map it to: DOMAIN1\mmouse
24. Repeat for all users in Domain1
25. Close Controller client.
Related Information
[{"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SS9S6B","label":"IBM Cognos Controller"},"Component":"Controller","Platform":[{"code":"PF033","label":"Windows"}],"Version":"All Versions","Edition":"","Line of Business":{"code":"LOB10","label":"Data and AI"}}]
Historical Number
1035740
Was this topic helpful?
Document Information
Modified date:
07 November 2019
UID
swg21371936