Question & Answer
Question
How do you configure and use SSL with the CCRC client and CCRC WAN Server?
Answer
Procedure:
- How IBM® Rational ClearCase Remote Client (CCRC) handles and store SSL certificates for use during secure (HTTPS) connections to IBM® Rational CCRC WAN Server
The CCRC client looks for the certificate presented by the HTTPS server in the following keystores:- JRE maintained truststore of known SSL certificates: <JRE_ROOT_DIR>/lib/security/jssecacerts
Or
<JRE_ROOT_DIR>/lib/security/cacerts
Where <JRE_ROOT_DIR> is the JRE install directory. - The per-user truststore: <USER_HOME>/.keystore, commonly used by some applications.
- CCRC-specific truststore: <USER_HOME>/.keystore_clearcase
Add public (that is, self-signed or internally issued) certificate authority root keys to this truststore. - (V9.0 and later) CMAPI-specific exception truststore: <USER_HOME>/.keystore_clearcase_exc
If the certificate presented to the client by the HTTPS server is found in any of these stores, it is accepted by the client without user action. The certificate can also be part of a certificate "chain". When some certificate in the chain is found in the truststores, the connection succeeds.
If a CCRC user is presented with this prompt:
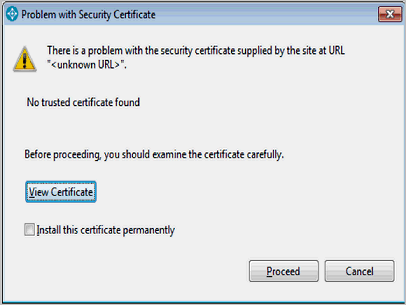
This prompt indicates that client is not able to find a certificate and the user must take some action. If the user chooses the selection to “Install this certificate permanently”, CCRC stores the certificate to <USER_HOME>\.keystore_clearcase. In V9.0 and later releases, the certificate is treated as an exception and stored in <USER_HOME>/.keystore_clearcase_exc.
The “jssecacerts” and 'cacerts' files are included with the JRE. They are pre-filled with certificates from "certifying authorities" (such as Verisign or Thwate). Commercially signed certificates (from vendors such as Verisign or Thwate), are presented to the client as part of a certificate chain that ends in a certificate that is already in one of the 'cacerts' file. If a commercially signed certificate is not available, CCRC administrators can create a “self-signed” certificate. This certificate is not in the 'cacerts' files and is handled explicitly, either by manually importing it into the <USER_HOME>/.keystore or <USER_HOME>/.keystore_clearcase truststores or installing the certificate via the CCRC "Problem with Security Certificate" dialog. A certificate can be manually installed by using the keytool utility, which is included with the JRE. For examples of using the keytool, refer to technote 541765 and Oracle reference documentation on keytool.
- JRE maintained truststore of known SSL certificates: <JRE_ROOT_DIR>/lib/security/jssecacerts
- Additional Java Runtime Environment (JRE) libraries required with large encryption keys
In accordance with the United States of America export restrictions, the Java version in use might have limited encryption key sizes. In order to successfully communicate with a server when large key size is in use, you must replace the bundled encryption policy files with the unrestricted files published by IBM. This file is called "Unrestricted JCE Policy files for SDK".
Procedure to obtain this file:- Go to the following website: http://www.ibm.com/developerworks/java/jdk/security/index.html.
- Click J2SE 6.0.
- Click IBM SDK Policy files in the “Contents” pane on the left.
The Unrestricted JCE Policy files for the SDK website is displayed. - Click Sign in and provide your IBM ID and password or register with IBM® to download the files.
- Select Unrestricted JCE Policy files for SDK Java 5.0 SR16, Java 6 SR13, Java 7 SR4 and later versions, and click Continue.
- View the license agreement and then click I Agree.
- Click Download Now.
- Install the files:
- Extract the file: unrestricted.zip into a directory of your choice in Windows.
- Copy the two .jar files from the extraction directory to following directories:
- If you are using a specific JDK version, then copy in $JAVA_HOME/jre/lib/security
- If you are using Weblogic AS, then WAS_HOME/java/jre/lib/security
- For the case of Weblogic AS, restart the Weblogic server for this change to take effect.
- SP800-131 security standard compliance in CCRC (client)
IBM® Rational ClearCase Remote Client versions 8.0.0.9 and newer include support for TLSv1.2 (default setting). CCRC can communicate with a server enforcing TLSv1.2, and is tolerant of SSL communication with a server not enforcing TLSv1.2.
Support for TLSv1.2 is included in IBM JRE 6 SR12 or newer, or Oracle JRE 7. CCRC and CMAPI do not yet support Oracle JRE 7.
Disable SP800-131 compliance
In special cases where a customer must disable SP800-131 compliance, the CCRC user can set a CCRC-specific property, introduced in CCRC version 8.0.0.10.
Add -vmargs -Dcom.ibm.rational.clearcase.transport.client.protocol=TLS in the application *.ini file or on the startup command line.
Note: SP800-131 compliance cannot be disabled if JRE property com.ibm.jsse2.sp800-131=strict (this setting might be required by other plug-ins or application, for example, IBM Rational Team Concert sharing the same Eclipse instance with CCRC).
Enforce SP800-131 compliance
Plug-ins or applications, such as IBM® Rational Team Concert, sharing an Eclipse instance with CCRC can enforce SP800-131 compliance, by setting -vmargs -Dcom.ibm.jsse2.sp800-131=strict. In this case, the CCRC-specific property -vmargs -Dcom.ibm.rational.clearcase.transport.client.protocol must be set to TLSv1.2. With these property settings, CCRC will not accept an SSL handshake with a server that does not communicate by using TLSv1.2. - SP800-131 security standard compliance in CCRC WAN Server
SP800-131 compliance must be configured in WAS.
- SSL communication between CCRC WAN Server and ClearQuest® Web
For access to ClearQuest® enabled UCM projects in CCRC, the CCRC WAN Server can be configured to communicate with ClearQuest® Web server by using SSL (URL specified in cq-db-mapfile.conf). The CCRC WAN Server does not handle SSL exceptions. Special certificate management is not required. Verification of validity of the certificates by system administrator is required to ensure successfully communication with CQWeb Server. This can be done by accessing the URL for ClearQuest® Web from a browser running on the server machine running the CCRC WAN Server.
(Windows only)
If you experience login failures with ClearQuest® in CCRC by using CCRC WAN Server versions 8.0.0.5 - 8.0.0.9, contact IBM® Rational support for a fix.
[{"Type":"MASTER","Line of Business":{"code":"LOB45","label":"Automation"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSSH27","label":"Rational ClearCase"},"ARM Category":[{"code":"a8m50000000L0i5AAC","label":"ClearCase"},{"code":"a8m50000000L0i5AAC","label":"ClearCase"},{"code":"a8m50000000L0i5AAC","label":"ClearCase"},{"code":"a8m50000000L0i5AAC","label":"ClearCase"},{"code":"a8m50000000L0i5AAC","label":"ClearCase"}],"ARM Case Number":"","Platform":[{"code":"PF002","label":"AIX"},{"code":"PF016","label":"Linux"},{"code":"PF027","label":"Solaris"},{"code":"PF033","label":"Windows"}],"Version":"10.0.0;10.0.1;8.0.0;8.0.1;9.0.0;9.0.1;9.0.2;9.1.0;and future releases"}]
Was this topic helpful?
Document Information
Modified date:
03 October 2023
UID
swg21666060